In my previous posts I explained how we can add devices to Intune and how we can push applications to those. This is another blog post under same category and in here I am going to talk about managing device compliances using Microsoft Intune.
In an infrastructure, we know how trusted device should looks like. We use different tools and services to make sure those does. As a simple example, most use group policies to make sure firewall, windows updates are up and running. But now, it is hard to define infrastructure boundaries as many people use same device for work and personal stuff. More and more people are working remotely. So, administrators are losing control over the devices. With Microsoft Intune we can easily define compliance policies and detect devices which is not meeting infrastructure requirements. It is similar how network policy server works in BYOD environment.
In this demo I am going to create compliance policy to detect the devices which doesn’t have firewall and antivirus services running. once it detects, it also should send notification to IT department so they aware that non-compliance device is in network.
1. To start, log in Azure portal as Global administrator
2. Then go to All Services | Intune | Devices
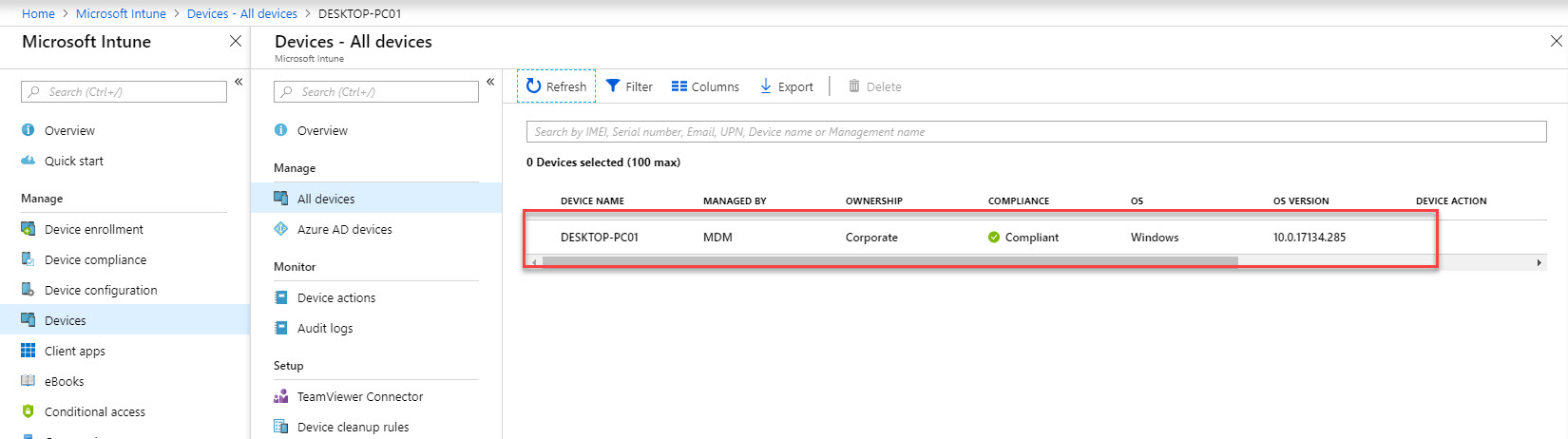
3. Under devices I can see my demo device is in healthy state.
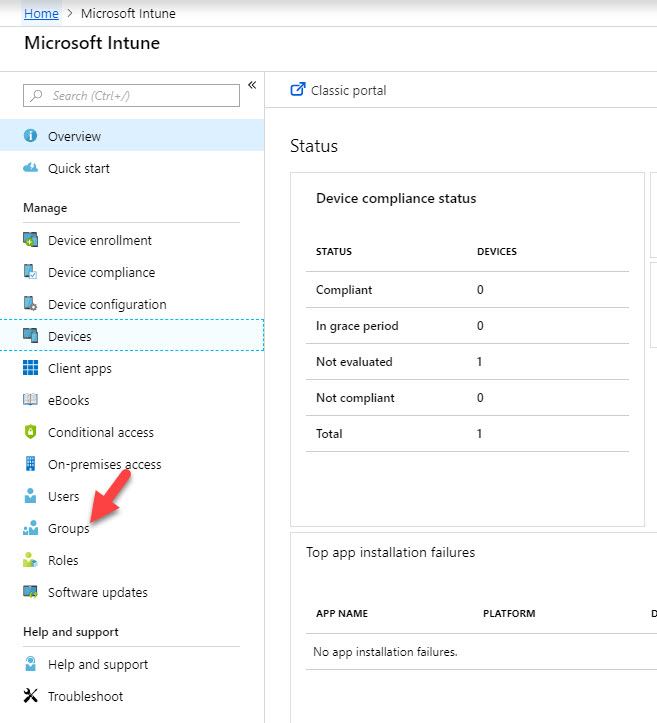
4. First, we need to create device group, so I can target it with the policy. to do that go to Intune home page and click on Groups
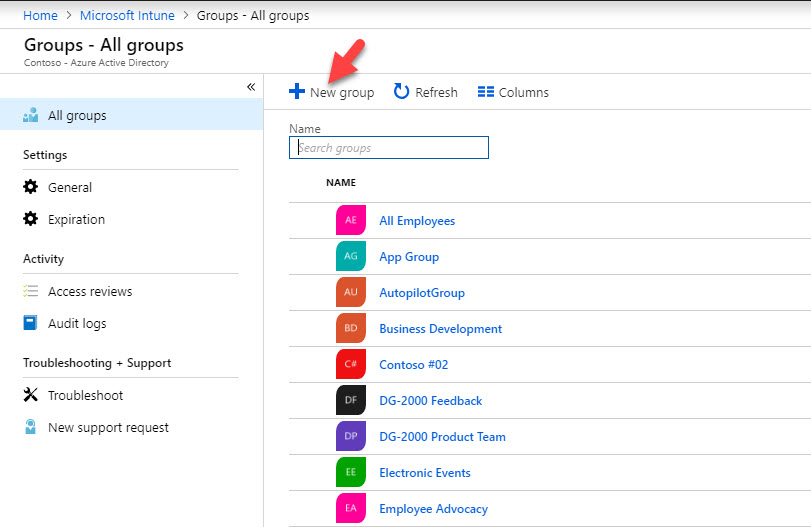
5. Then click on New Group
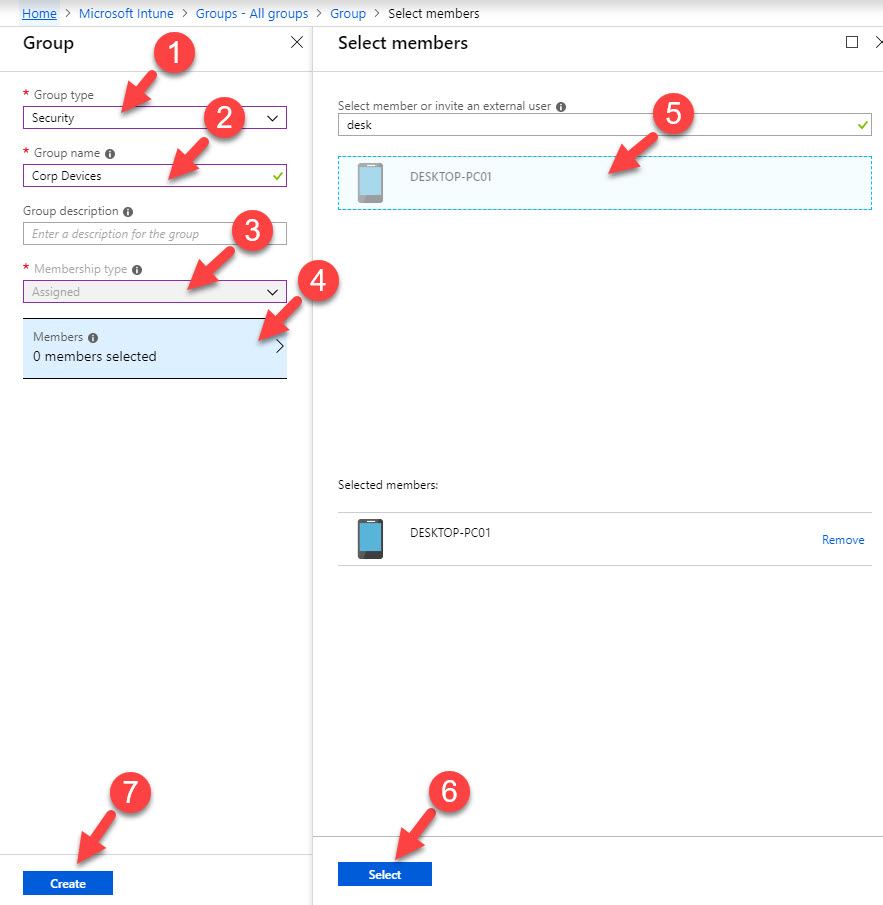
6. Then create the new security group with demo device.
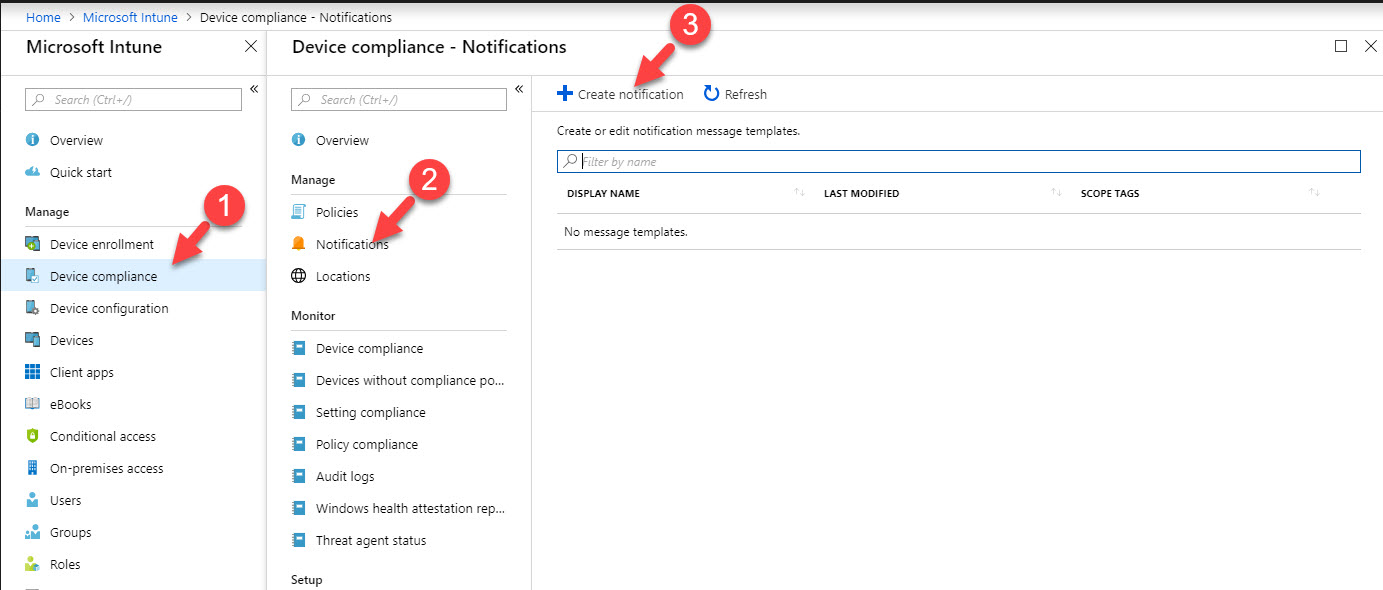
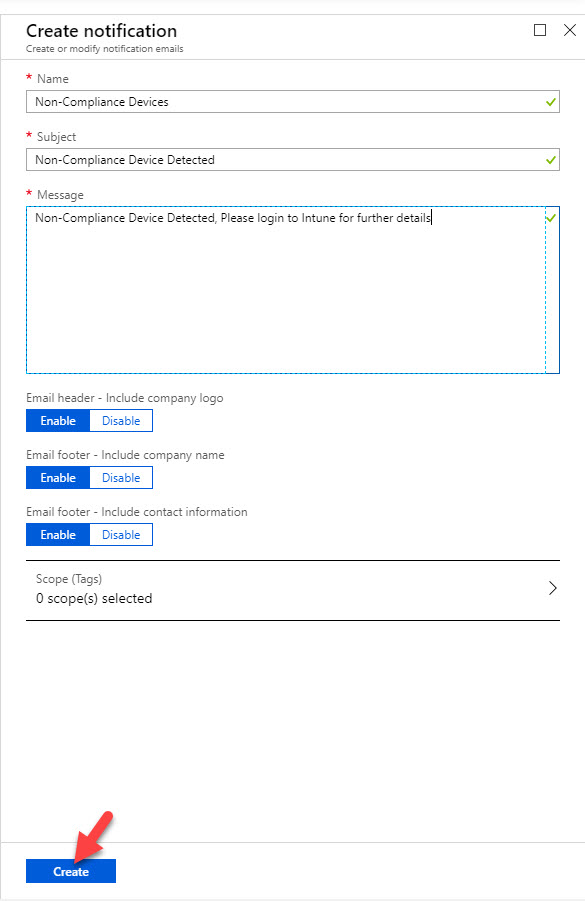
7. As next step, we need to create notification. This is email template that we going to fire when policy detects a non-compliance device. To do that go to Intune home page, Device compliance | Notifications | Create notification
8. Then create template with relevant data.
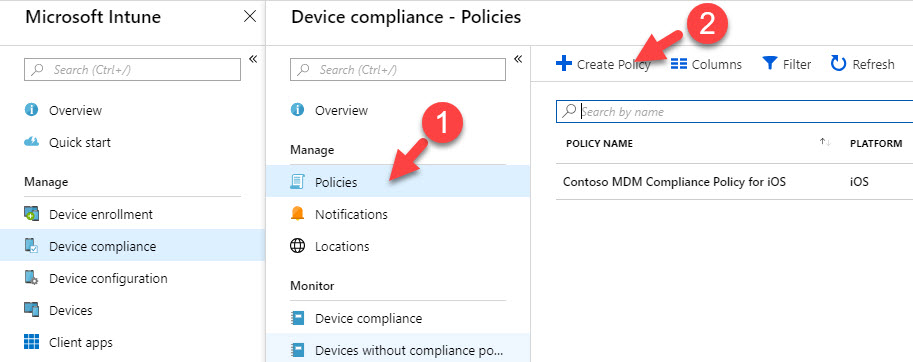
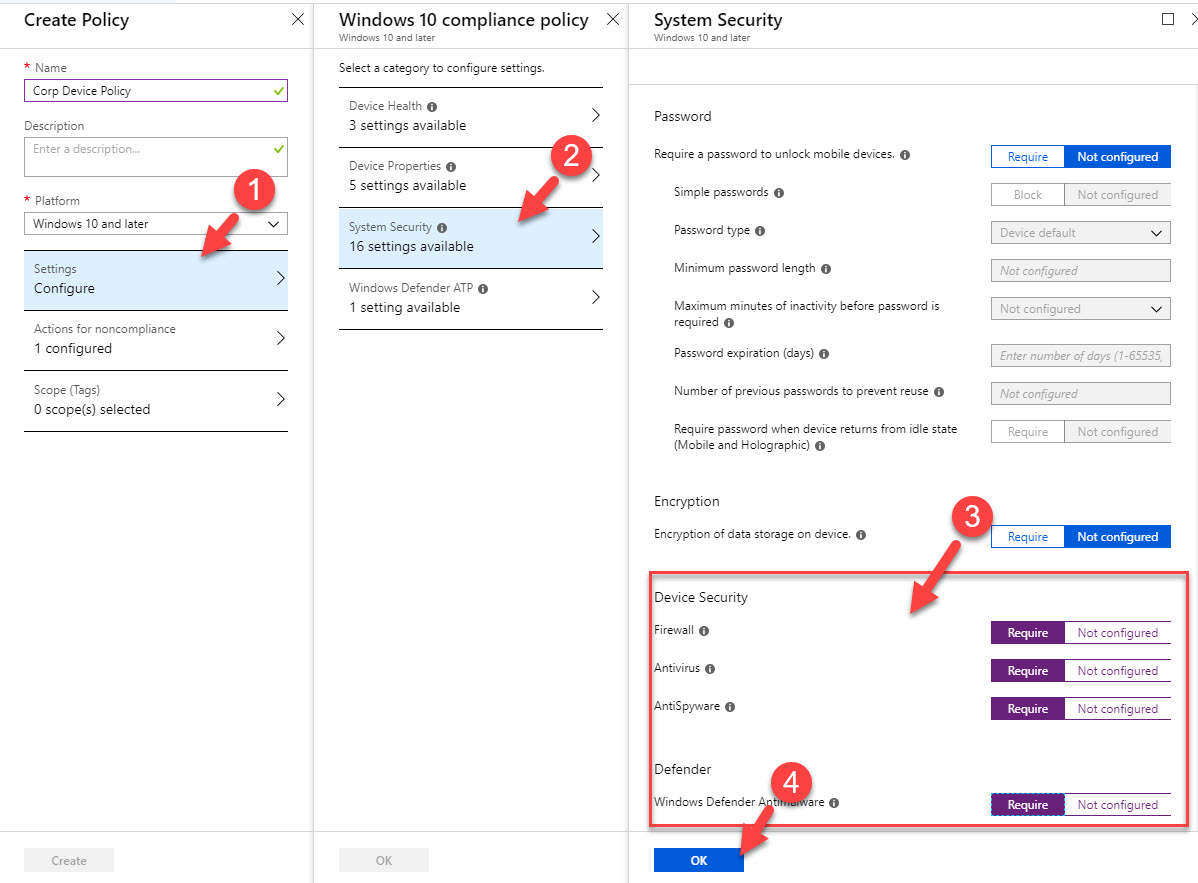
9. Now we have everything ready for the policy. To start click on Policies | Create Policy
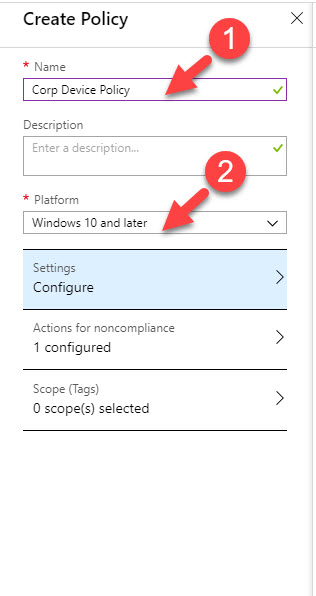
10. In next window type policy name & select the platform. In my demo it is going to be for Windows 10 device.
11. Then click on Setting | System Security & set Require for Firewall, Antivirus, Antispyware & Defender.
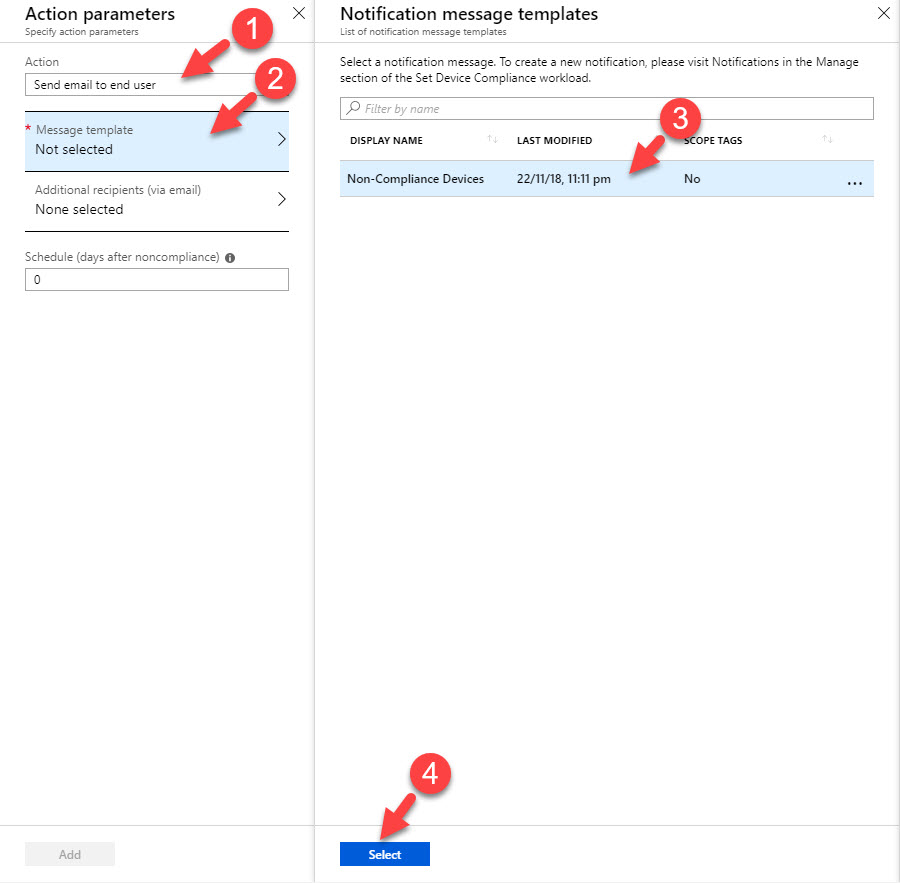
12. Next, click on Actions for noncompliance | Add and select the action option as send email to end user. Under message template select new notification we created.
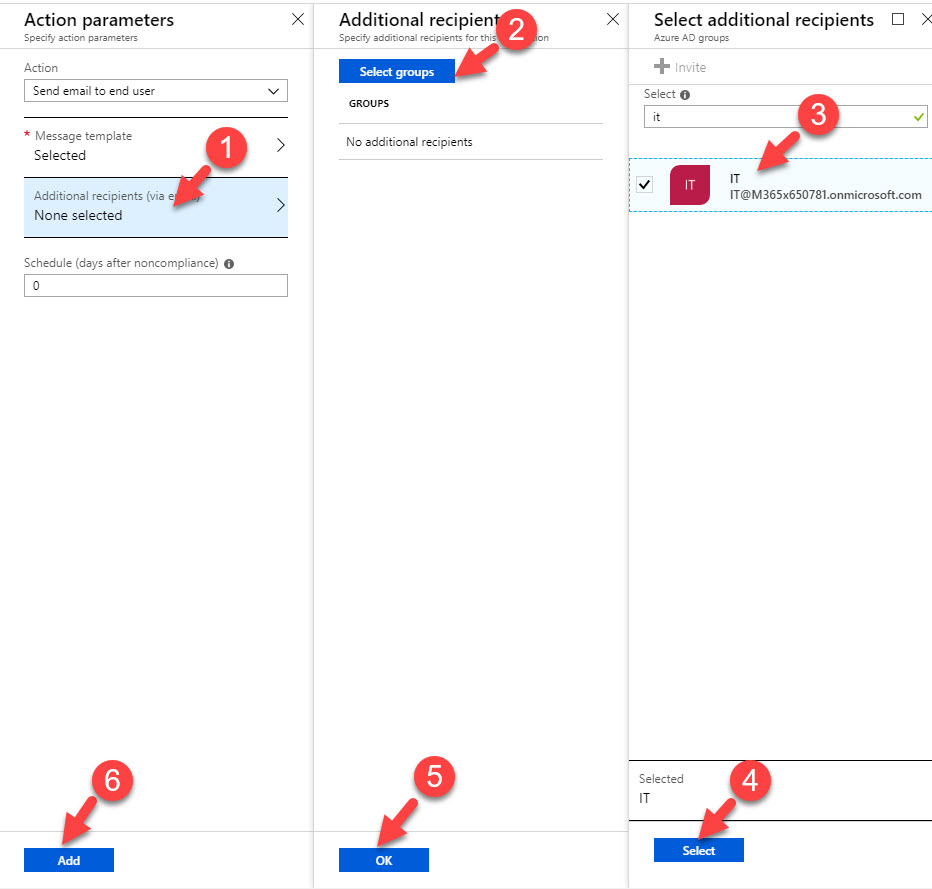
13. Above will only send notification to the global admin account that I am using to setup this policy. I also need to send notifications to IT department. To do that, click on Additional recipient and select the IT distribution group.
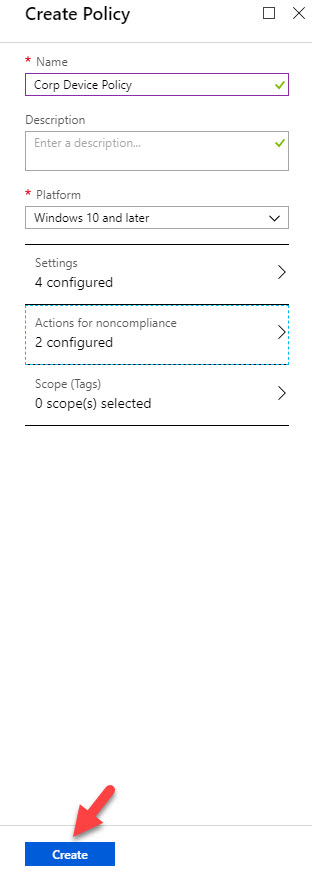
14. After all settings are in place, click on Create
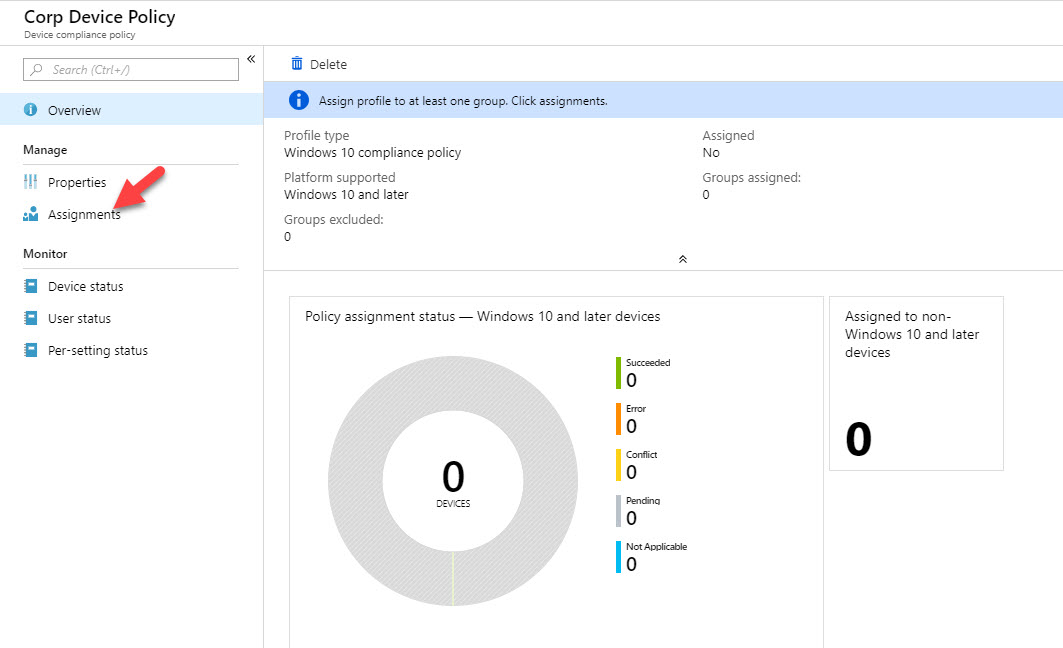
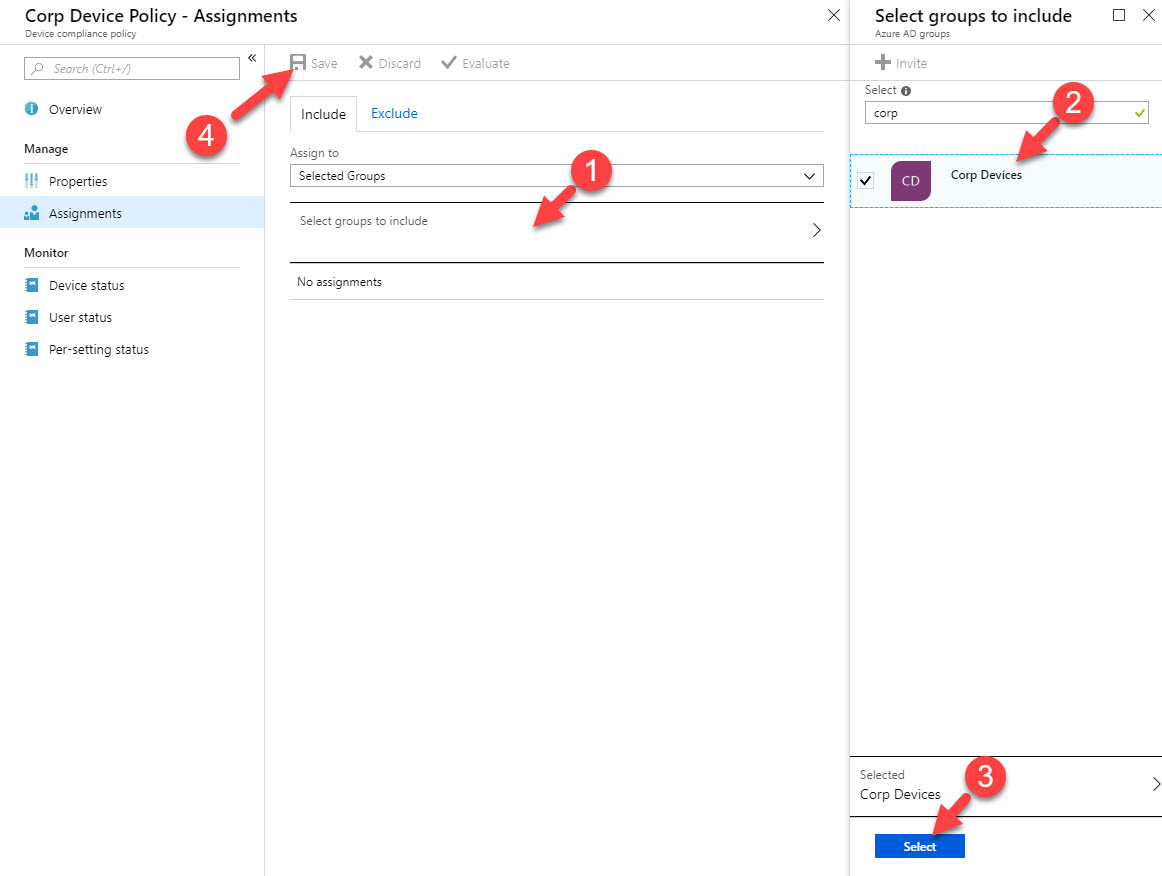
15. Once policy is in place, click on it and then click on Assignments
16. Then select the device group we created in the beginning. This will be the target for the policy.
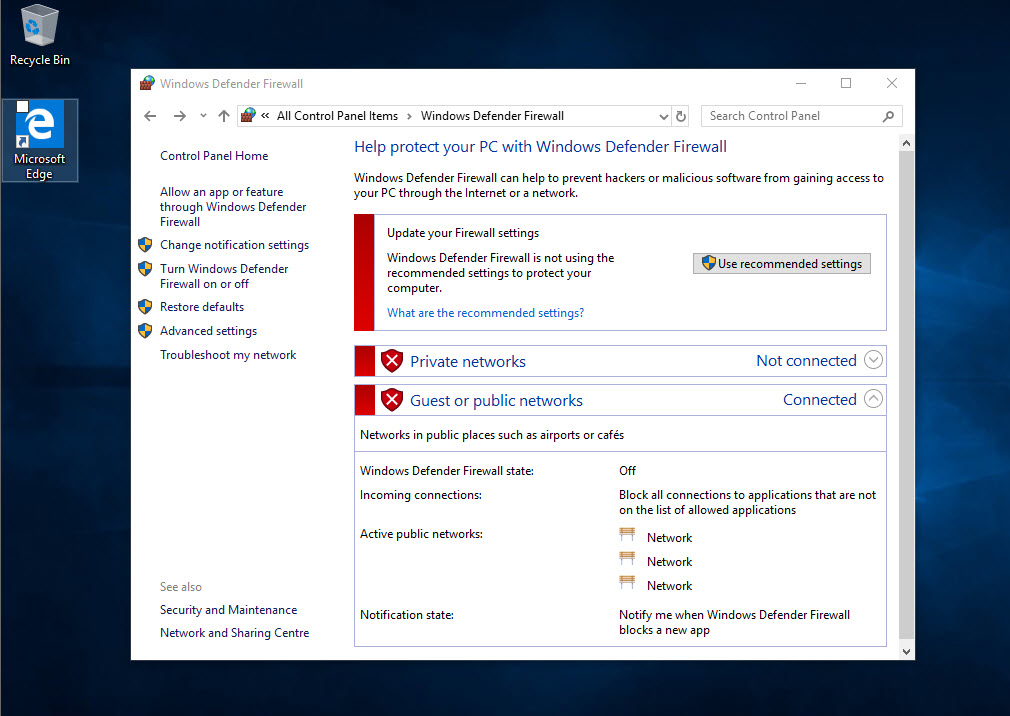
17. Now it is time for testing. I went to my demo pc and turn off the firewall.
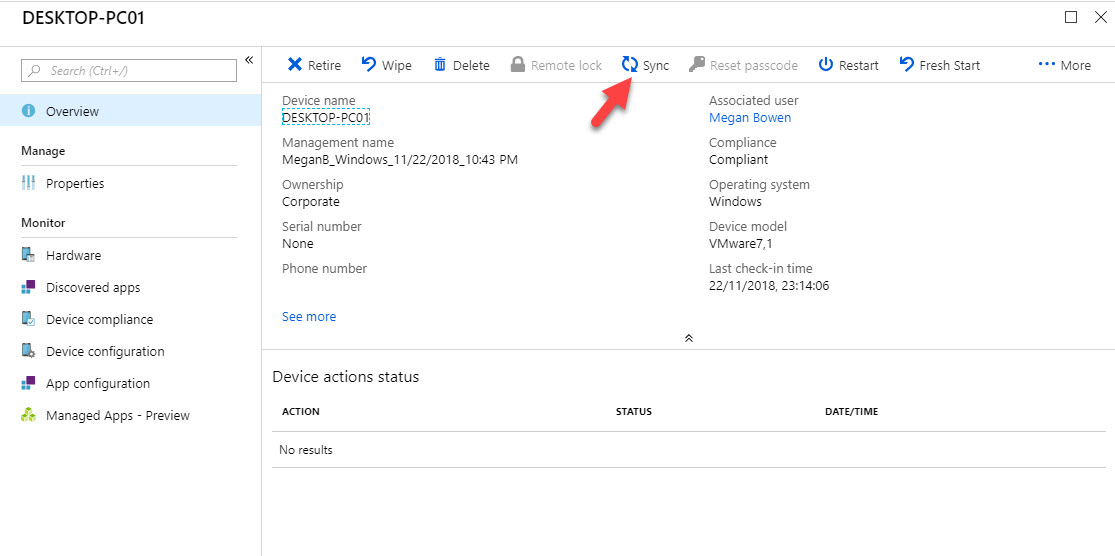
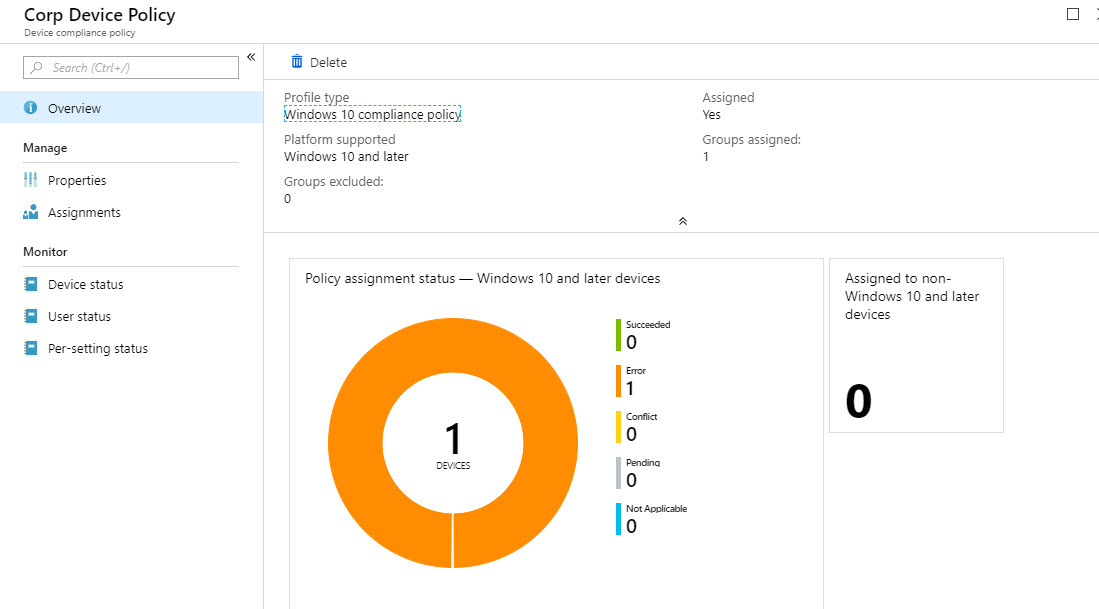
18. Then go to Intune | Devices | All Devices and click on the demo device.
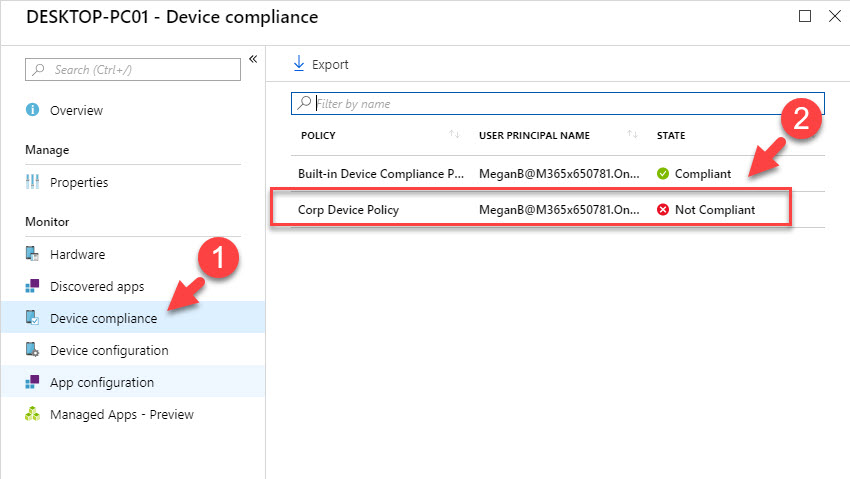
19. In new window click on Sync so it will forcefully speed up the policy evaluation.
20. Then after few minutes, I go to new policy and click on overview. In there I can see 1 device is detected.
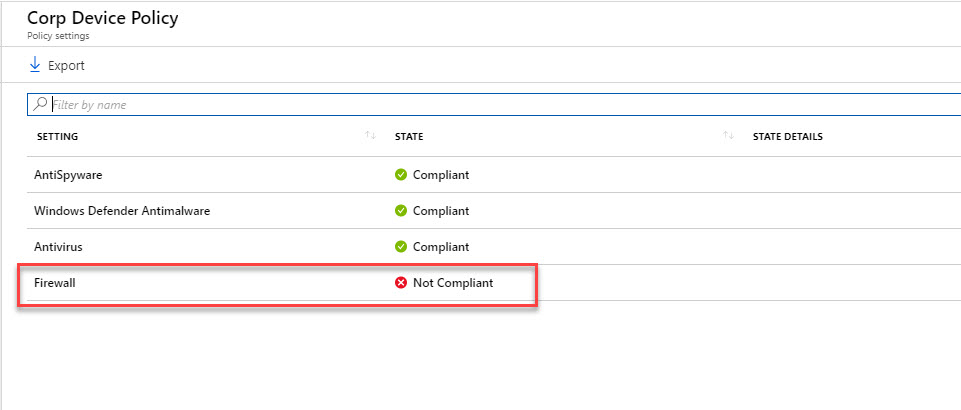
21. If I go in details I can see the device is non-compliant with the new policy and it is flagged because it is not running firewall services.
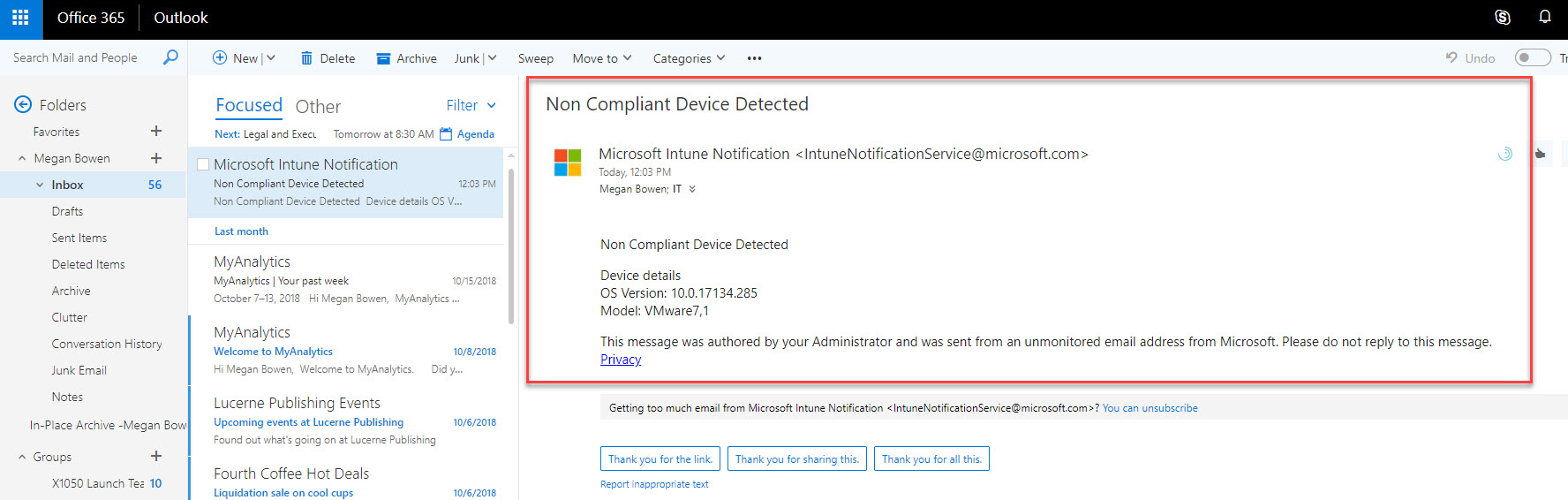
22. As expected, it sent email notification to IT department as well.
As we can see it does the job. It is easy to setup and easy to detect. This marks the end of this blog post. If you have any further questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.