In my previous blog post, I explained how we can manage Azure AD users by using Azure Active Directory PowerShell for Graph module. In there I also shared many examples. You can access it via http://www.rebeladmin.com/2019/05/step-step-guide-manager-users-using-azure-active-directory-powershell-graph-module/
In this blog post I am going to show how we can manage Groups, using same method.
Azure AD Groups also works similar to on-premises AD groups. It can use to manage permissions in affective manner. In Hybrid environment there will be cloud-only groups as well as synced groups from on-premises AD environment. In this section we are going to look in to group management using Azure Active Directory PowerShell for Graph module.
Let’s start with listing groups.
We can search for a group using,
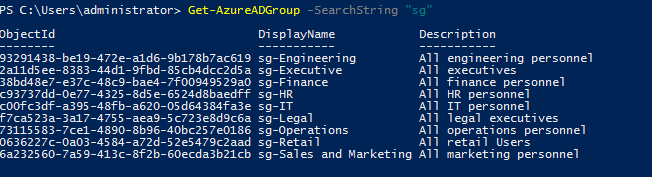
Get-AzureADGroup -SearchString "sg"
In above command, SearchString is used to define the search criteria. Above example will list down any group containing “sg” in Display name field.
In search result, we can see the objectId for the group. Once we know the ObjectId, we can see the details of the group using,
Get-AzureADGroup -ObjectId 93291438-be19-472e-a1d6-9b178b7ac619 | fl
In hybrid environment, there will be security groups which is synced from on-premises Active Directory. We can filter this groups using,
Get-AzureADGroup -Filter 'DirSyncEnabled eq true' | select ObjectId,DisplayName,LastDirSyncTime
In above example, LastDirSyncTime column display the last successful sync time of the group.
We can filter cloud-only groups using,
Get-AzureADGroup -All $true | where-Object {$_.OnPremisesSecurityIdentifier -eq $null}
In preceding command, we are using attribute OnPremisesSecurityIdentifier to filter the groups. This attribute only has value if it is synced from on-premises AD.
We can view group memberships by using,
Get-AzureADGroupMember -ObjectId 2a11d5ee-8383-44d1-9fbd-85cb4dcc2d5a
In above command, we are using ObjectId to uniquely identify the group.
We can add members to group using Add-AzureADGroupMember cmdlet.
Add-AzureADGroupMember -ObjectId 2a11d5ee-8383-44d1-9fbd-85cb4dcc2d5a -RefObjectId a6aeced9-909e-4684-8712-d0f242451338
In preceding command, ObjectId value represent the group and RefObjectId value represent the user.
We can remove a member from group by using,
Remove-AzureADGroupMember -ObjectId 2a11d5ee-8383-44d1-9fbd-85cb4dcc2d5a -MemberId a6aeced9-909e-4684-8712-d0f242451338
In preceding command, ObjectId value represent the group and MemberId value represent the user’s Object Id.
We also can combine Add-AzureADGroupMember cmdlet with Get-AzureADUser cmdlet to add bulk users to a group.
In below script, I used Get-AzureADUser cmdlet to search users in Marketing Department. Then used Add-AzureADGroupMember to add those users to Sales group as members.
#######Script to Add Multiple users to Security Group#############
Import-Module AzureAD
Connect-AzureAD
##### Search for users in Marketing Department ##########
Get-AzureADUser -All $true -Filter "Department eq 'Marketing'" | select ObjectId | Out-File -FilePath C:\salesusers.txt
#####Add Users to Sales Group#########
(Get-Content "C:\salesusers.txt" | select-object -skip 3) | ForEach { Add-AzureADGroupMember -ObjectId f9f51d29-e093-4e57-ad79-2fc5ae3517db -RefObjectId $_ }
In hybrid environment, the security groups are mainly synced from on-premises AD. But there can be requirements for cloud-only groups as well. We can create cloud-only group by using,
New-AzureADGroup -DisplayName "REBELADMIN Sales Team" -MailEnabled $false -MailNickName "salesteam" -SecurityEnabled $true
Preceding command creates a security group called "REBELADMIN Sales Team". This group is not a mail enabled group.
We can remove Azure AD group using,
Remove-AzureADGroup -ObjectId 7592b555-343d-4f73-a6f1-2270d7cf014f
In above, Object ID value defines the group.
Apart from security groups, Azure AD also have predefined administrative roles which can use to assign access permissions to Azure AD and other cloud services. There are more than 35 predefined administrative roles. Each of role have their own set of permissions. More details about this roles can find in https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/directory-assign-admin-roles
We can list down all the administrative roles using,
Get-AzureADDirectoryRoleTemplate
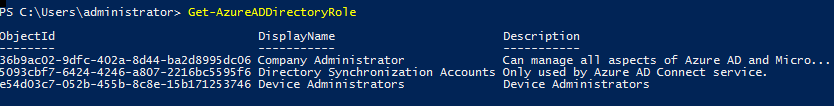
By default, only few administrative roles are enabled. We can list these roles using,
Get-AzureADDirectoryRole
[su_note]Company Administrator directory role represent the Azure AD Global Administrators.[/su_note]
We can enable Administrative role using,
Enable-AzureADDirectoryRole -RoleTemplateId e6d1a23a-da11-4be4-9570-befc86d067a7
In above command, RoleTemplateId value represent the Administrative Role.
We can assign administrative role to a user by using,
Add-AzureADDirectoryRoleMember -ObjectId b63c1671-625a-4a80-8bae-6487423909ca -RefObjectId 581c7265-c8cc-493b-9686-771b2f10a77e
In preceding command, ObjectId value represent the Administrative Role. RefObjectId is the object id value of the user.
We can list down members of Administrative role using,
Get-AzureADDirectoryRoleMember -ObjectId 36b9ac02-9dfc-402a-8d44-ba2d8995dc06
In above command, ObjectId represent the Administrative role.
We can remove a member from the role using,
Remove-AzureADDirectoryRoleMember -ObjectId 36b9ac02-9dfc-402a-8d44-ba2d8995dc06 -MemberId 165ebcb7-f07d-42d2-a52e-90f44e71e4a1
In preceding command, MemberId is equal to user’s object id value.
This marks the end of this post. I hope this was useful and If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.