OpenVPN is an open-source VPN protocol that is trusted by many cloud service providers to provide site-to-site, point-to-site, and point-to-point connectivity to cloud resources. Now Azure AD authentication also works with OpenVPN protocol. This means we can use Azure AD features such as conditional access, user-based policies, Azure MFA with VPN authentication. In this Demo, I am going to demonstrate how to configure OpenVPN for Azure point-to-site VPN and then how to integrate Azure AD authentication with it.
Prerequisites
1. To configure OpenVPN, first, we need to have a working point-to-site setup. The native Azure point-to-site VPN setup uses Azure certificate authentication. I wrote an article about it before and it can be accessed using http://www.rebeladmin.com/2018/07/step-step-guide-azure-point-site-vpn/
So, before we start, please go ahead and configure the VPN gateway with certificate authentication.
2. Also, I am going to use Azure PowerShell for configuration. Please make sure you have the Azure PowerShell module installed. More info about it can find under https://docs.microsoft.com/en-us/powershell/azure/install-az-ps?view=azps-2.6.0
Configure OpenVPN for Azure P2S VPN
1. Launch PowerShell console and connect to Azure using Connect-AzAccount (Using Global Administrator Account)
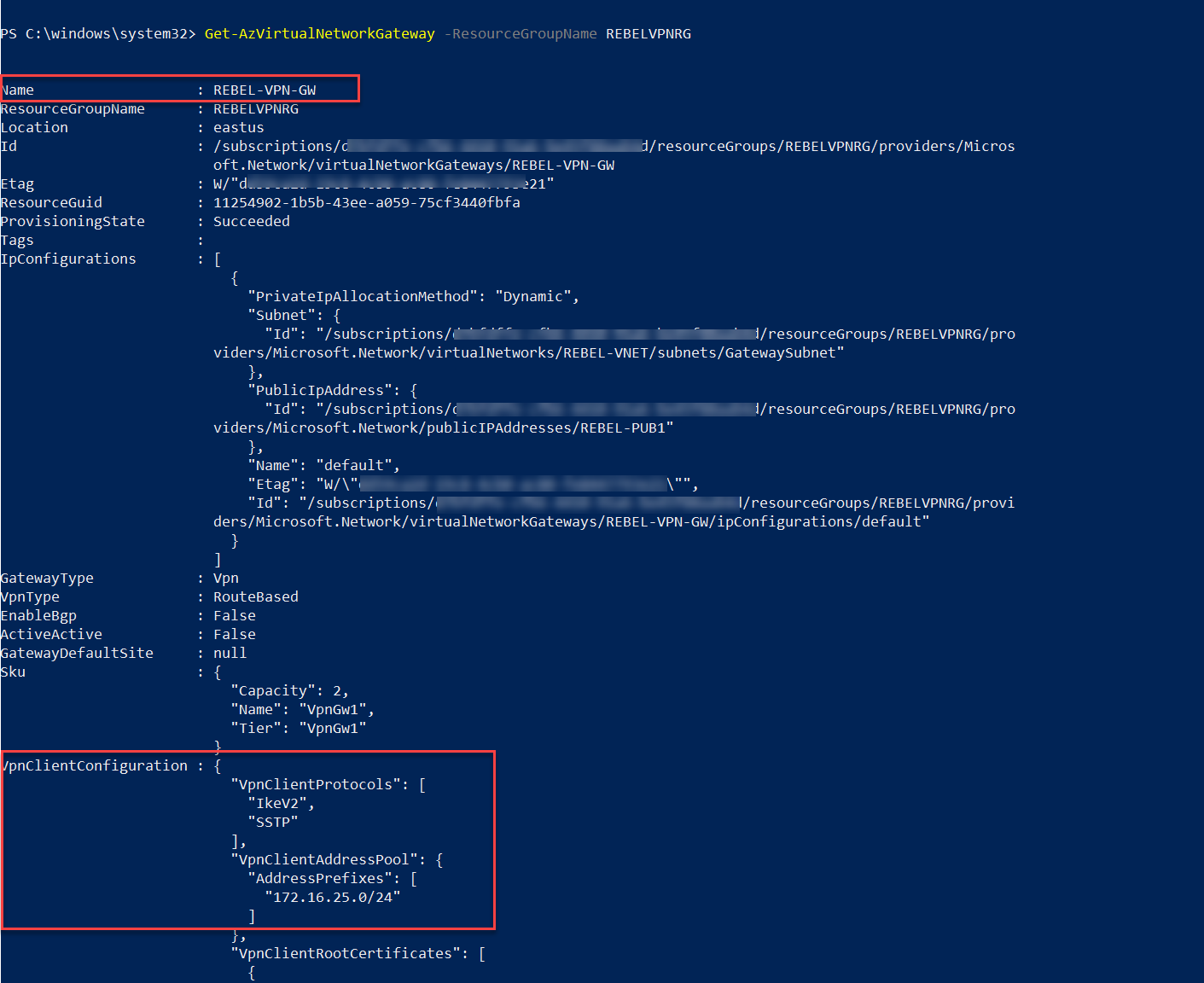
2. Then I ran Get-AzVirtualNetworkGateway -ResourceGroupName REBELVPNRG to review my VPN gateway configuration. Here REBELVPNRG is the resource group it belongs to.
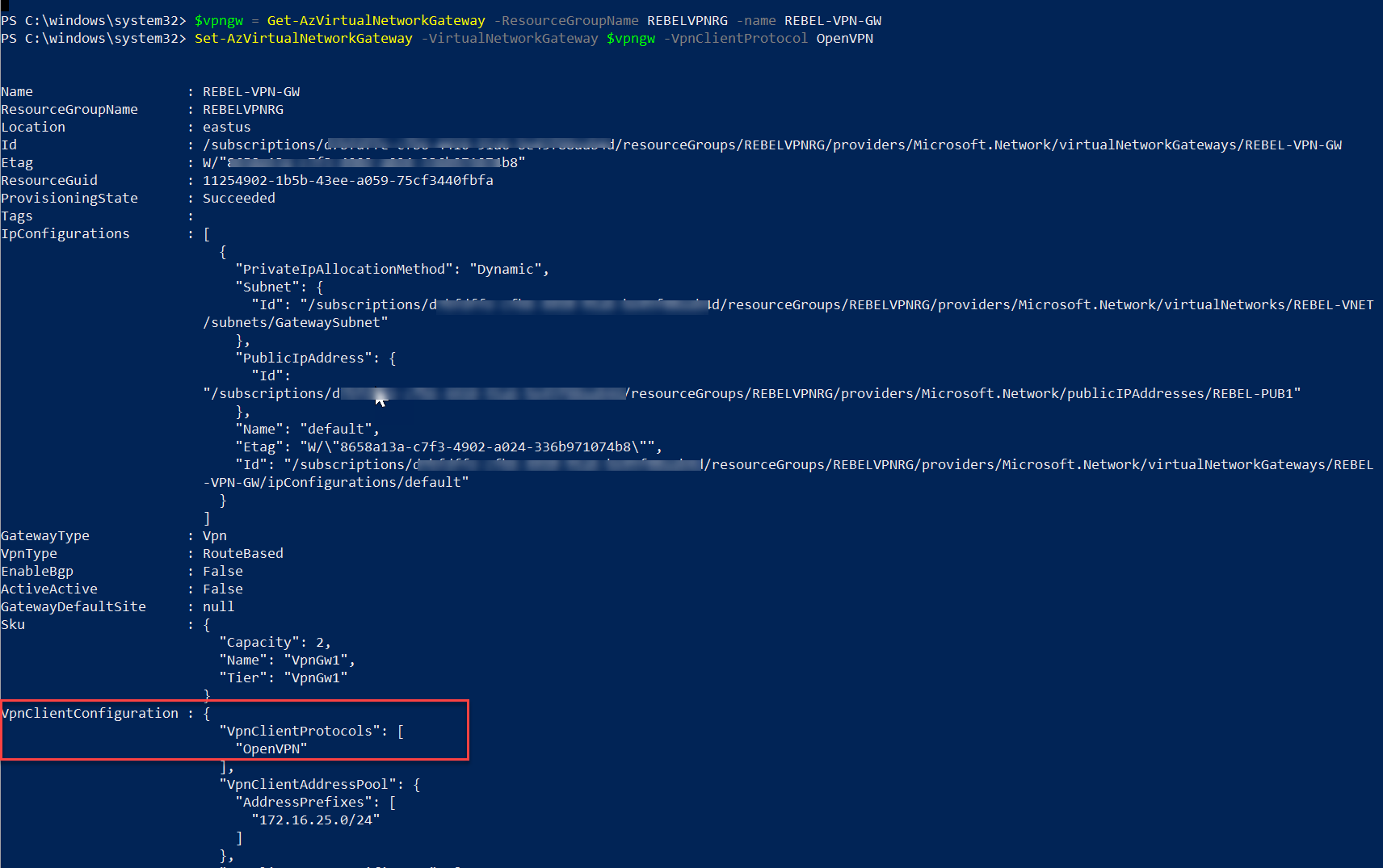
3. Then let's go ahead and change the VPN client protocol to OpenVPN using,
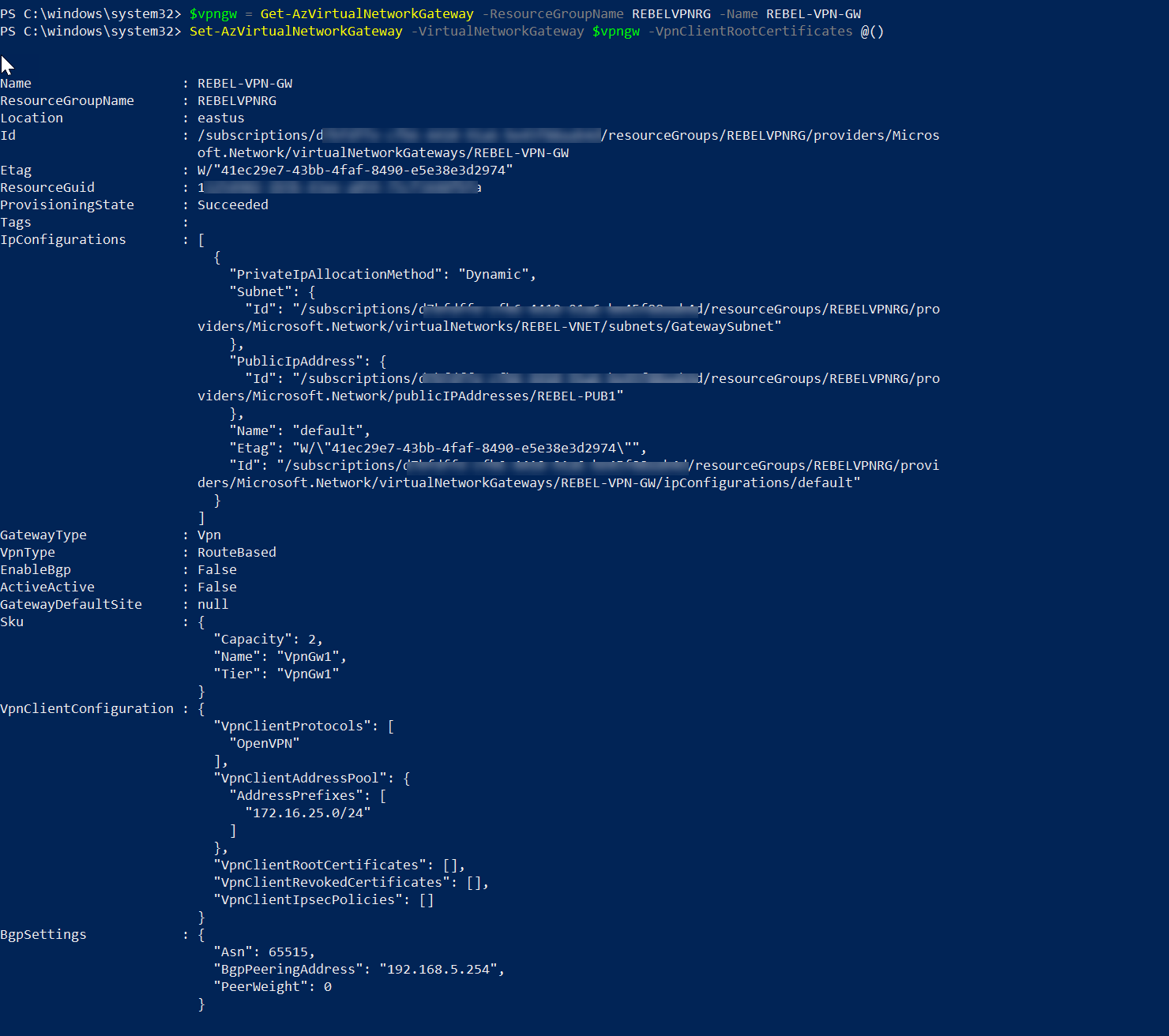
$vpngw = Get-AzVirtualNetworkGateway -ResourceGroupName REBELVPNRG -name REBEL-VPN-GW
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $vpngw -VpnClientProtocol OpenVPN
In the above, REBEL-VPN-GW is the VPN gateway name.
Enable Azure AD authentication
1. Log in to Azure Portal (https://portal.azure.com) as Global Administrator
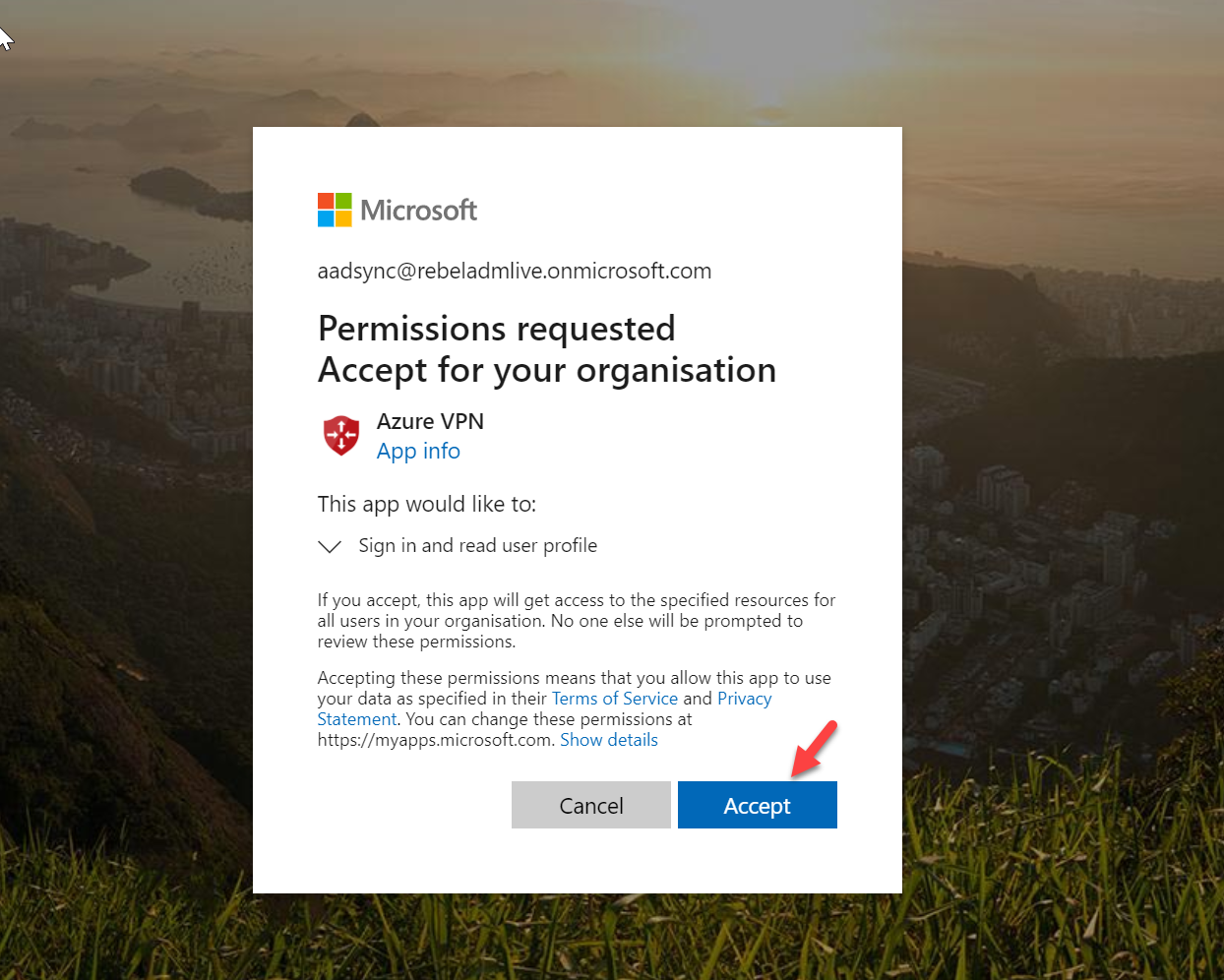
2. Copy https://login.microsoftonline.com/common/oauth2/authorize?client_id=41b23e61-6c1e-4545-b367-cd054e0ed4b4&response_type=code&redirect_uri=https://portal.azure.com&nonce=1234&prompt=admin_consent and paste it in the browser window and press enter.
3. Then we can see the prompt for admin approval. Click on accept to grant permission to the Azure VPN app.
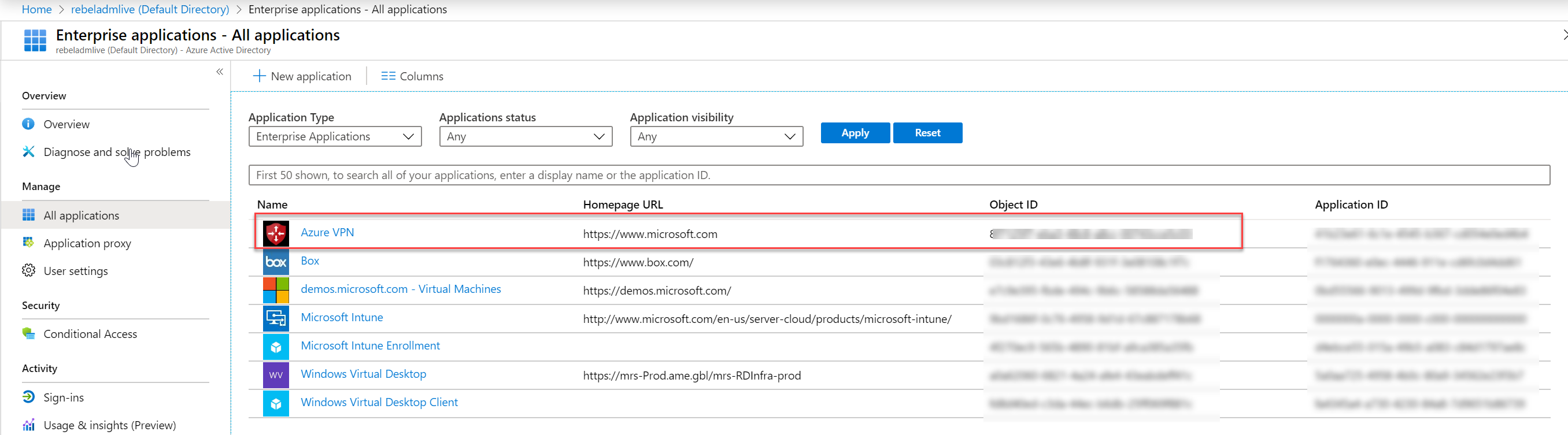
4. After a few minutes, we should be able to see Azure VPN app under Azure Active Directory | All Applications
5. Launch PowerShell console and connect to Azure using Connect-AzAccount (Using Global Administrator Account)
6. As soon as login, we will see the Azure AD tenant id. Go ahead and note down the value.
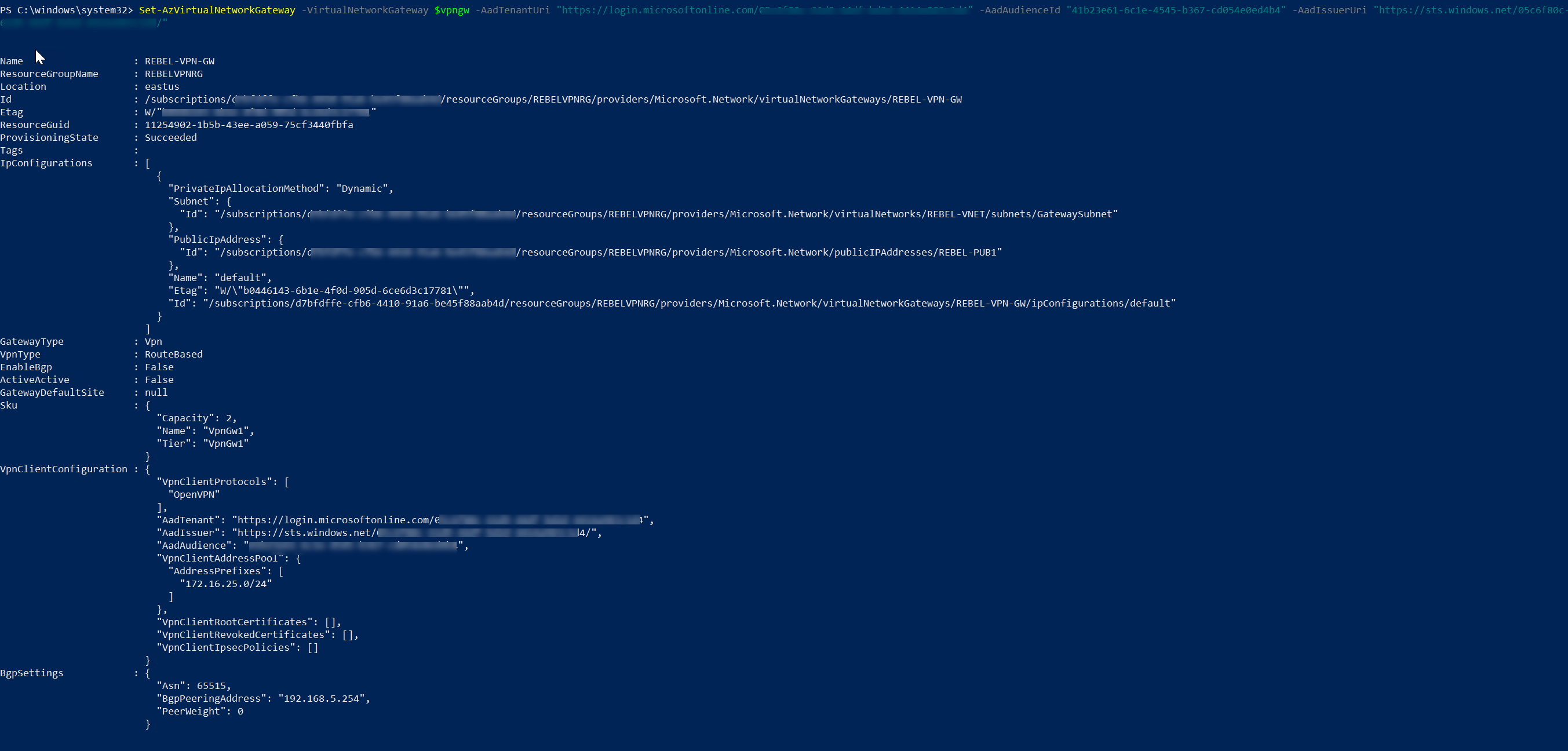
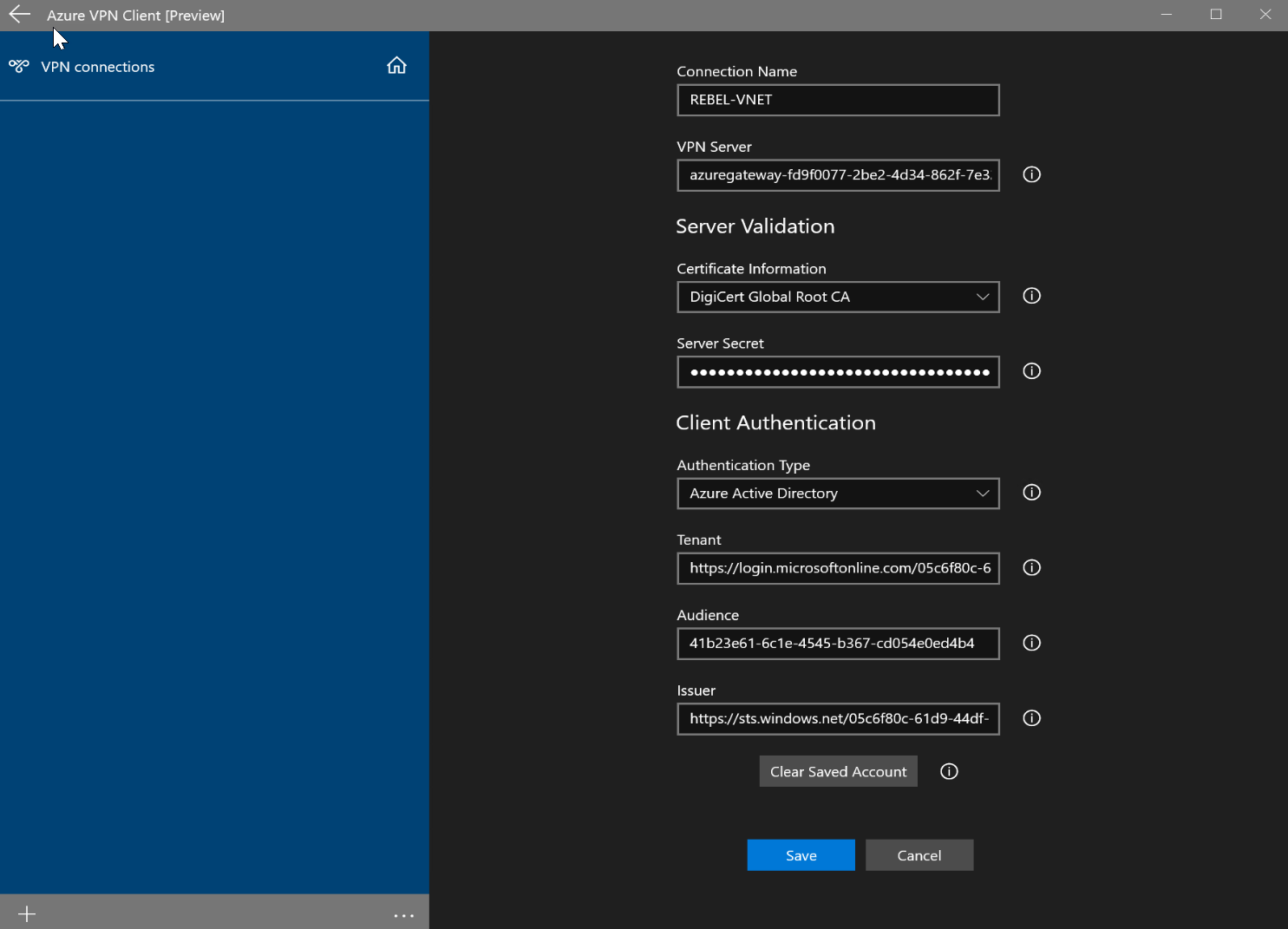
7. Then to enable Azure AD authentication for Azure VPN gateway user,
$vpngw = Get-AzVirtualNetworkGateway -ResourceGroupName REBELVPNRG -Name REBEL-VPN-GW
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $vpngw -VpnClientRootCertificates @()
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $vpngw -AadTenantUri "https://login.microsoftonline.com/<Azure AD Directory ID>" -AadAudienceId "41b23e61-6c1e-4545-b367-cd054e0ed4b4" -AadIssuerUri https://sts.windows.net/<Azure AD Directory ID>/
In the above, REBELVPNRG is the resource group name and REBEL-VPN-GW is the VPN gateway. Also, replace <Azure AD Directory ID> with your Azure AD tenant id value we found in previous steps.
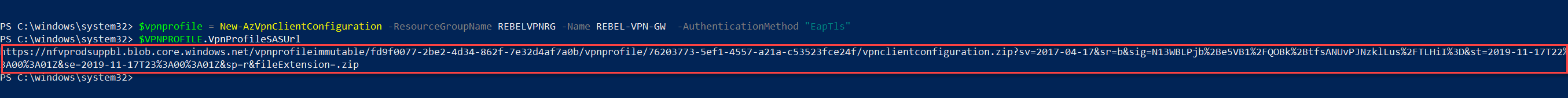
8. The next step of the configuration is to generate VPN profile settings XML so we can use it with the client. To do that run,
$vpnprofile = New-AzVpnClientConfiguration -ResourceGroupName REBELVPNRG -Name REBEL-VPN-GW -AuthenticationMethod "EapTls"
$VPNPROFILE.VpnProfileSASUrl
This will return a URL. Copy it and place it in the browser. Then download and save it.
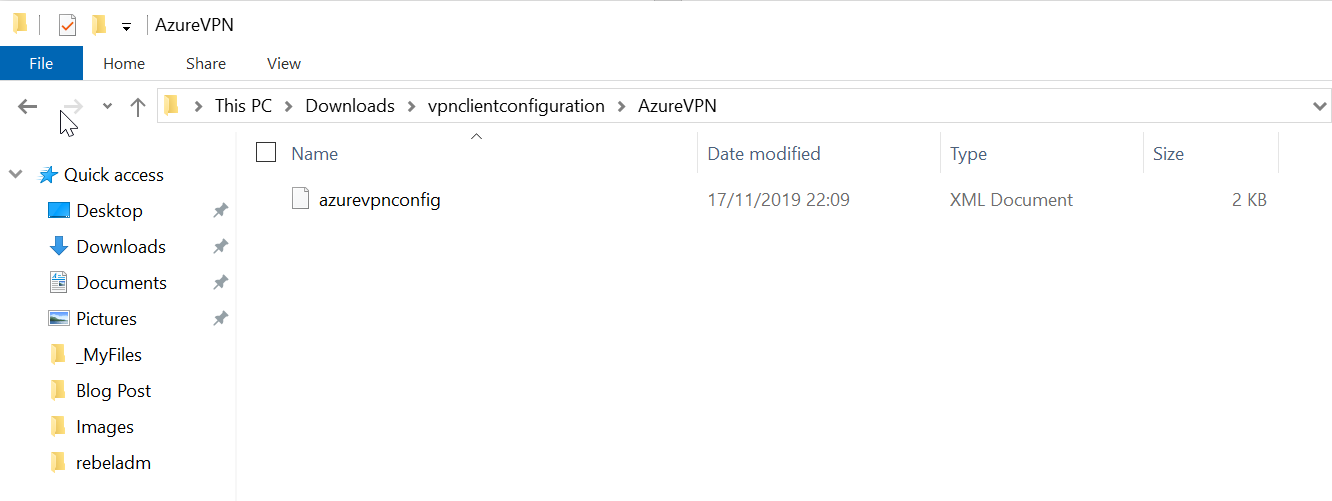
9. Then extract it and confirm if you can see azurevpnconfig.xml in vpnclientconfiguration\AzureVPN
Configure Client
Now we are done with the configuration, the next step is to test it with the client.
1. Log in to the client computer.
2. Download VPN client from https://www.microsoft.com/p/azure-vpn-client-preview/9np355qt2sqb?rtc=1&activetab=pivot:overviewtab
3. Once the installation is completed, launch the app.
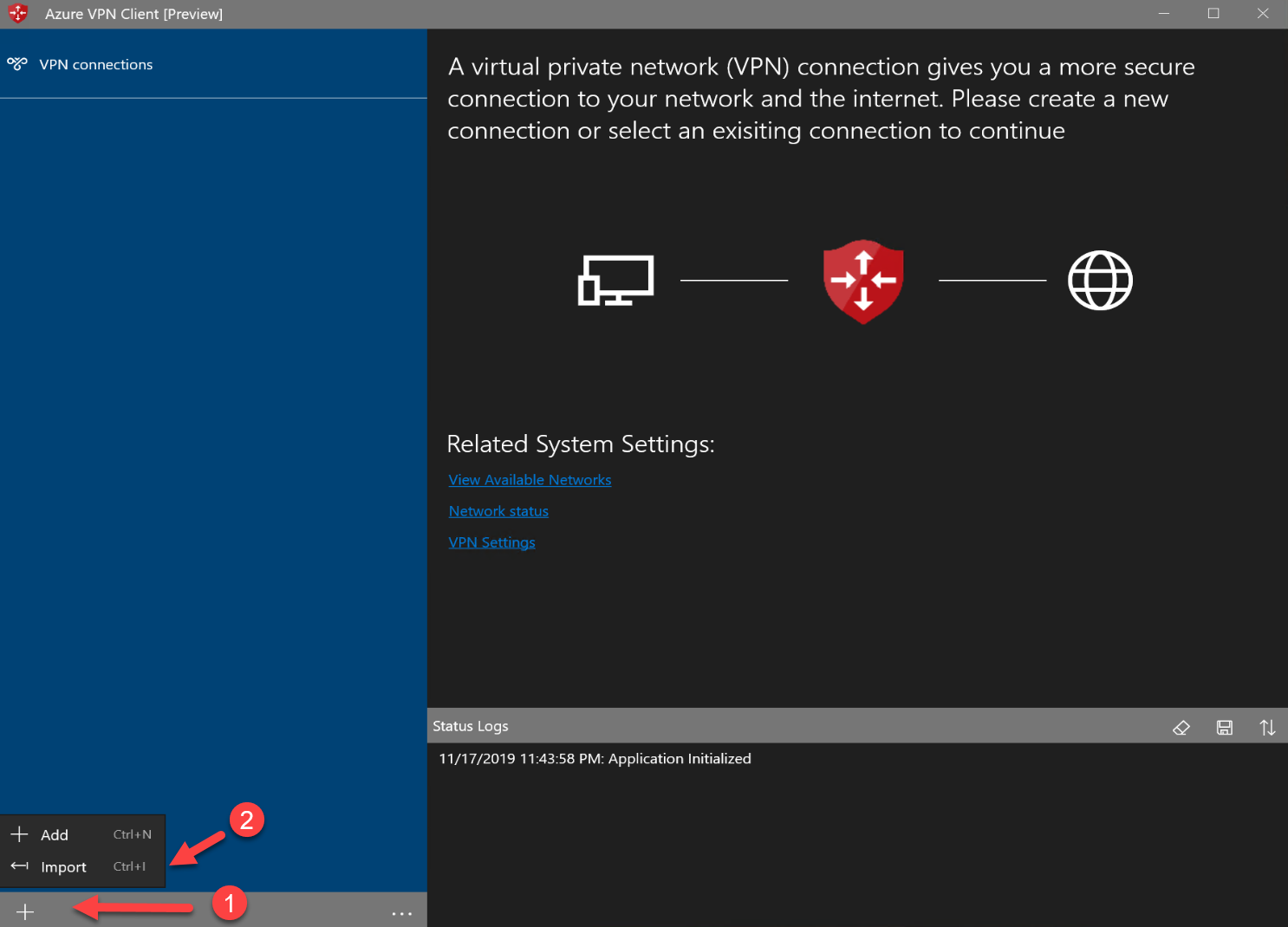
4. In application, click on the Import option to import the VPN settings.
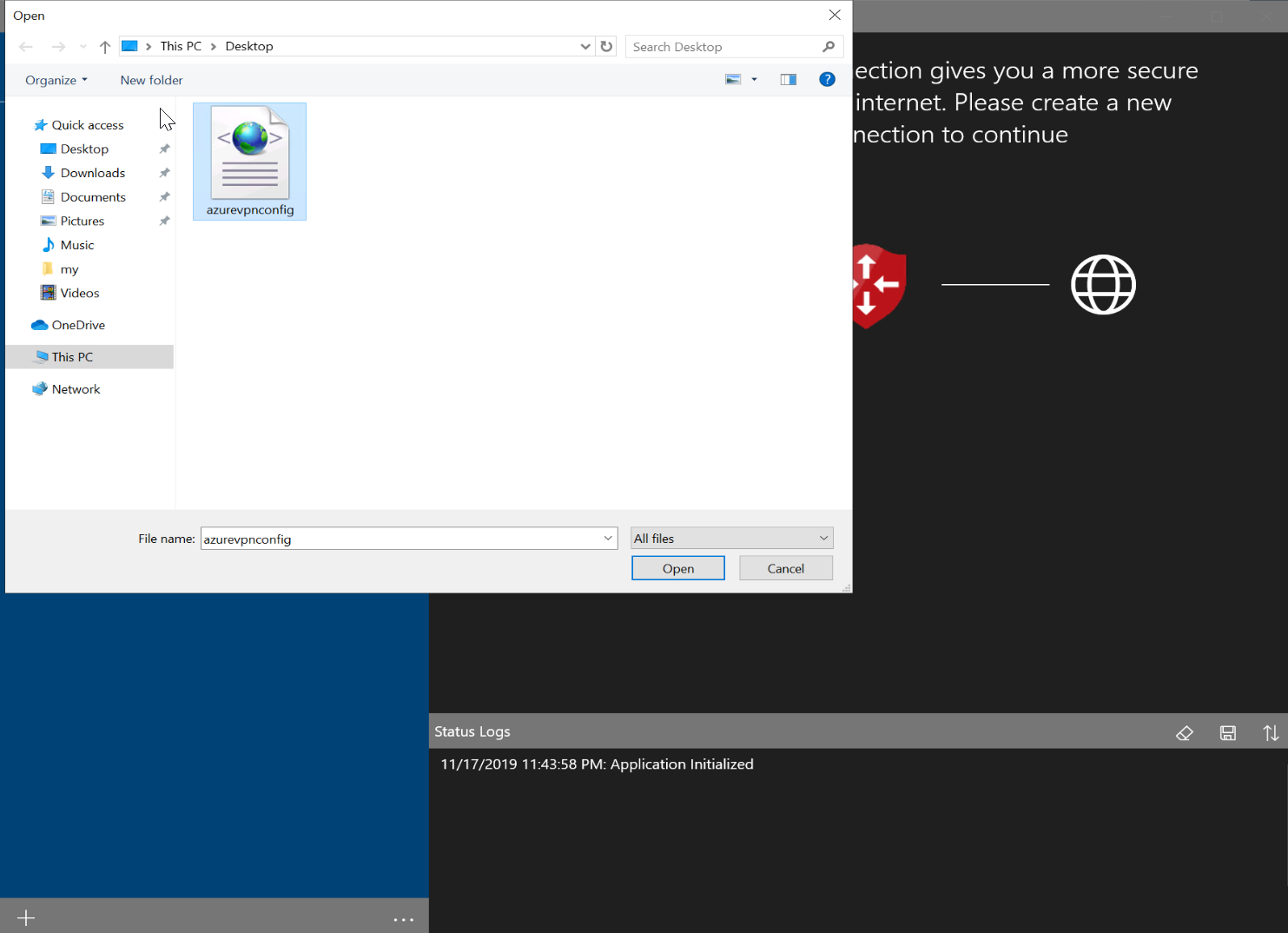
5. Then browse and select the azurevpnconfig.xml file we downloaded.
6. In the app window, we can see the imported config, click on Save to complete the import process.
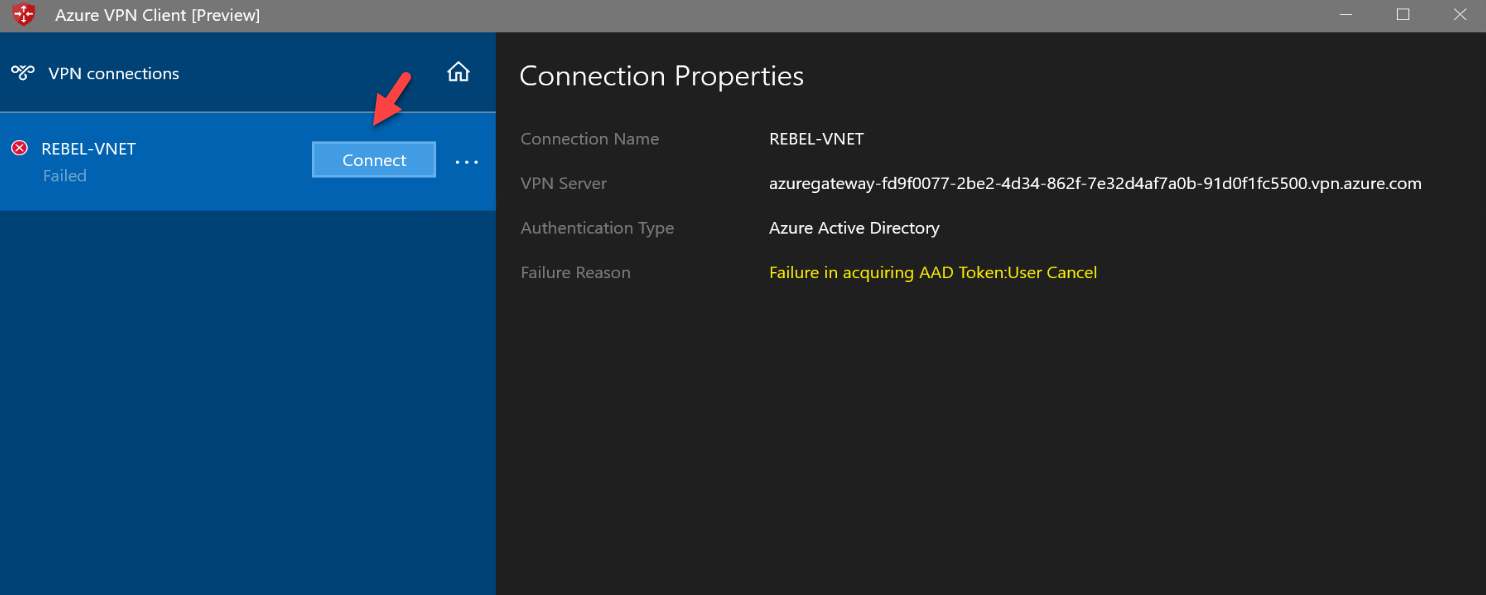
7. Then click on the Connect button to initiate the VPN connection.
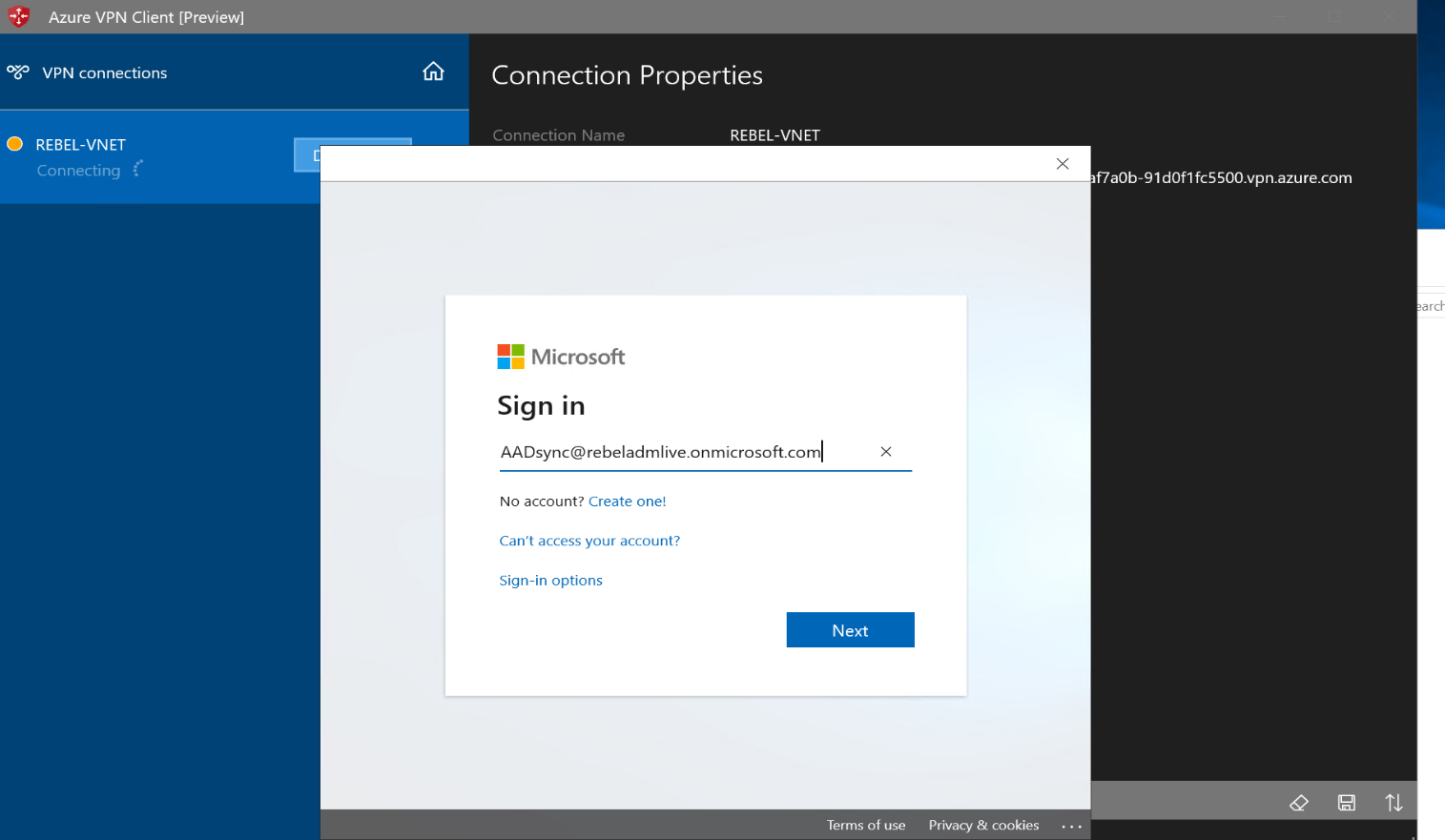
8. As expected, it is now prompted for user name and password. Log in using valid Azure AD user name and password.
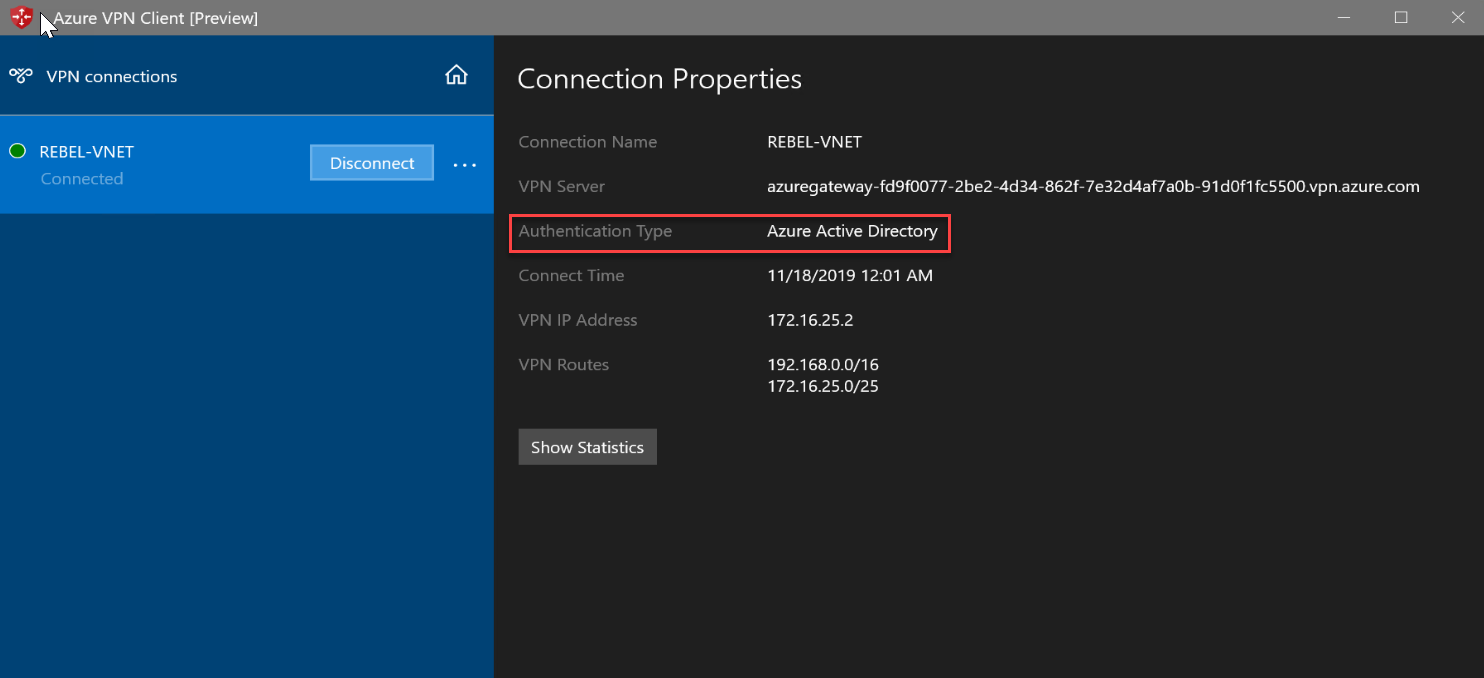
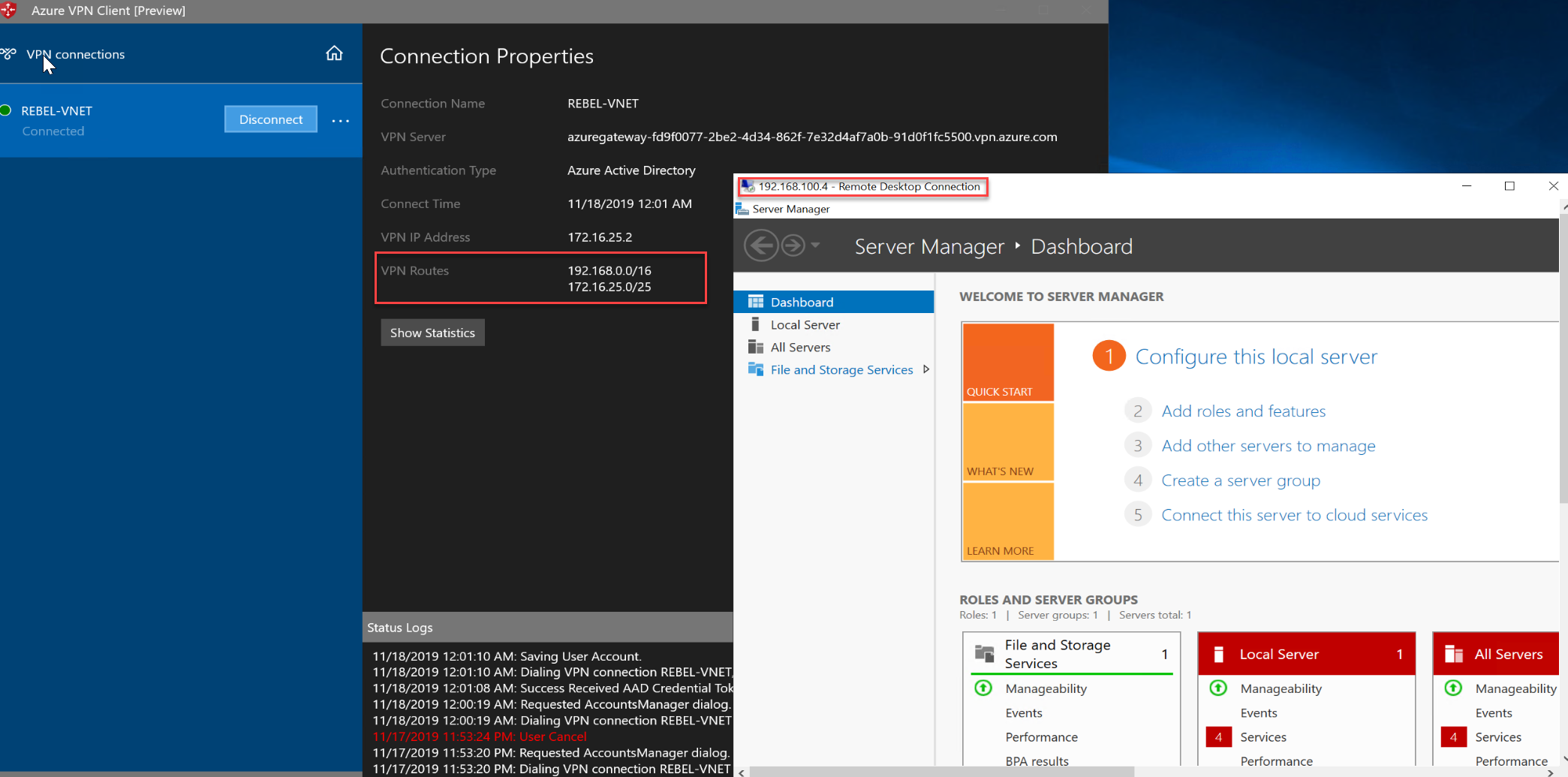
9. After successful authentication, we can see the connection has been initiated successfully.
10. I also can connect to a VM running on the virtual network via its private Ip address.
This marks the end of this blog post. I hope now you know how to enable Azure AD authentication for Azure P2S VPN. If you have any further questions about this feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.





Is it possible to have an IKEv2 STS tunnel between premise and azure and then utilise these OpenVPN P2S connections to effectively allow clients on the VPN (wherever they may be) to gain access to some on premise servers (as well as that in the VNET) ? Apparently it’s possible using both IKEv2 for both S2S and P2S but I’m not too familiar with openvpn. This link is useful but only covers IKEv2 connections.
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-point-to-site-routing#vnetbranchbgp
Nice Article. Missed a Disclaimer: This will not work with Azure AD joined devices (managed by Endpoint Manager/ Intune). You must be an administrator to be able to initiate connections when using Azure VPN Gateway. If you really want to have a proper solution for all your employees ( both admins and non admins), better to be away from Azure VPN Gateway.
If I have let-say 300 Users working from Home
What I should be using
P2S SSTP
or OPENVPN ?