In an organization there can be lot of applications, services running to serve its user base. Some time when you setup an application services it asking you to use a service account with certain permissions.
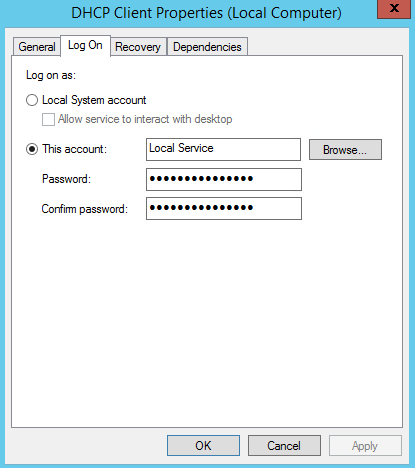
In a computer normally we can run application as Local Service, Network Service or Local System. Also if required you can use a user account setup on the domain or local computer.
Traditional Service Account
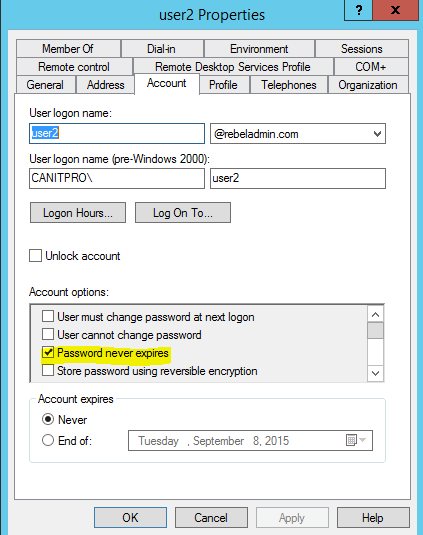
Well in past (before server 2008 R2) a service account is nothing but a user account. As you know by default a typical user account password expires (in domain it’s depend on group policies), if it’s happens to a service account, the service or application will stop running as it can’t authenticate. So what usually do is create a user account and set password “not to expire”. So it’s more vulnerable.
Managed Service Accounts
Microsoft introduce Managed Server Accounts (MSAs) with windows server 2008 R2 to address the issues with traditional service accounts.
In traditional service account its night mare to handle the password changes. But with MSA it will automatically will change the password. In AD DS it will store the MSA object as msDS-ManagedServiceAccount. However MSAs are cannot be use between multiple computers or in cluster environment. MSA uses a complex, random, 240-character password and change that automatically when it reach the domain or computer password expire date. By default its 30 days’ time. It also can’t be locked out and can’t use for interactive logins. Mainly the benefits of MSAs are automatic password change and simplified SPN (Service Principal Name) management.
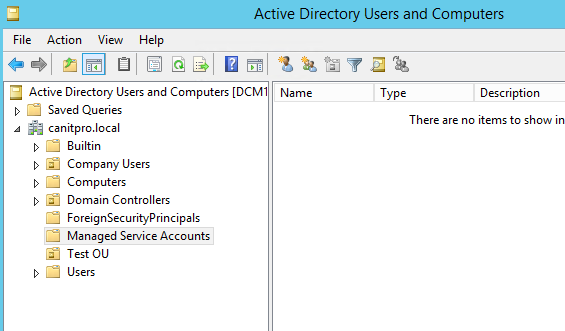
In AD DS, MSA’s will stored under CN=Managed Service Accounts, DC=<domain>, DC=<com>, Container.
In order to run MSAs you need to have following in your environment,
• Windows server 2008 R2 or later domain controller
• AD module for powershell
• .NET framework 3.5
Let’s see how we can create the MSA
1) Load the powershell cmd with domain administrator privileges
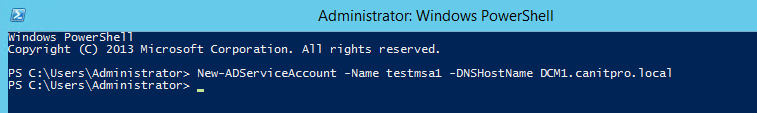
2) To create service account,
New-ADServiceAccount –Name <MSA_Name> –DNSHostname <DNS name of Domain_Controller>
So in my demo-
New-ADServiceAccount –Name testmsa1 –DNSHostname DCM1.canitpro.local
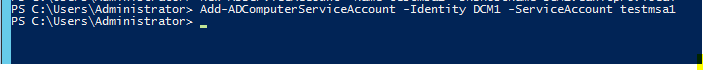
3) Then we need to associate it with the computer object
Add-ADComputerServiceAccount –identity <Host_Computer_Name> -ServiceAccount <MSA_Name>
In my demo I associate it with computer DCM1
Add-ADComputerServiceAccount –identity DCM1 -ServiceAccount testmsa1
4) Then we need to install the MSA in hostcomputer.
Install-ADServiceAccount –Identity <MSA_Name>
In my demo its
Install-ADServiceAccount –Identity testmsa1
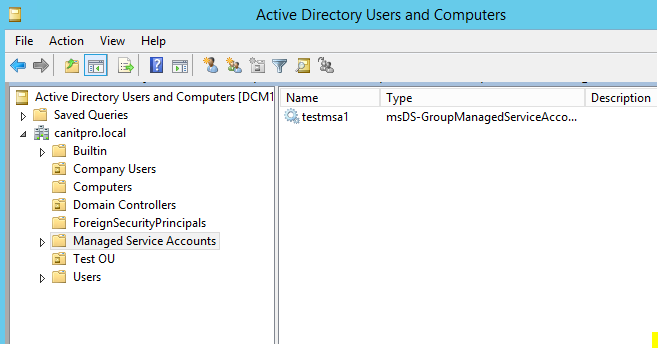
Now we can use it to assign for service. If you go to AD now we can see the new account under MSA OU
If you have any question feel free to contact me on rebeladm@live.com