“Security”, it’s always a concern in any computer infrastructure. Most of the time giving the “technology” is not enough to maintain security in infrastructure. It’s depend on the way users, admins apply these tools and practices in their infrastructure.
Now a “hacking” question! If someone wants to hack your infrastructure what is the way to start? What account privileges can do the more damage? Yes it must be domain admin account (well some may not agree, I will be discussing about privileged access management in future posts in detail). But most admin like to keep them secure. If someone trying to login those accounts you may notice quickly. But will you apply same security to your sales computers? Or receptionist? In lot of infrastructure I seen people use company ID as the user name and password most of the time same as they like to keep this simple. So isn’t those easy to get in to your infrastructure rather than through a “server”? So if attacker fill that pc with junk, delete apps etc. the user will call up the admin to help. Most of time support engineers have domain admin privileges for “easy support”. When they RDP to the pc to help the user, the attacker in back ground can harvest the credentials of the admin user because when connect via RDP the credentials of the admin user will transmitting to the pc. The above example is just one way, even it can apply for your servers, cloud VM etc.
So question is what is the secure way then?
Yes Microsoft seen this issue and introduced Restrict Admin mode for RDP connections. This is applies to windows server 2012 R2 and new. Supported desktop OS version are windows 8.1 and new.
What is it?
When this mode is enabled the RDP client will not send plain-text or any other re-usable form of credentials to the remote PC or Server.
Also will not be able to use any other network resources from that pc or server through restricted admin mode connection with out authentication again.
For ex- to daisy chain the RDP connections, Network Drive access
Also it will effect on the applications specially if you use single-sign-on.
Enable Restricted Admin mode in target computer
Before we use restricted admin mode against a server or pc we need to enable it on target. To do that we need to add a registry entry.
To do that,
1) Log in to server or pc as administrator
2) Start > Run > regedit
3) Brows to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa
4) Add Registry Key DisableRestrictedAdmin Type: REG_DWORD Value: 0
5) You do not need Reboot to apply the changes
This also can publish via a group policy setting.
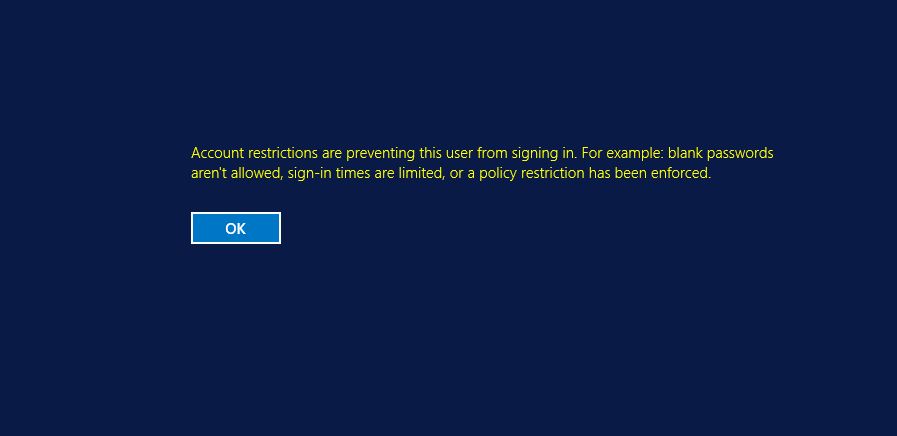
If above is not done, when you connect to the server with Restricted Admin Mode you will get following error
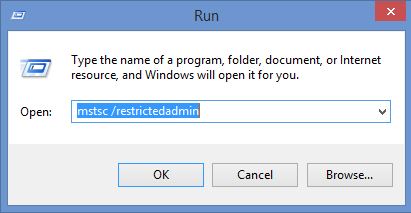
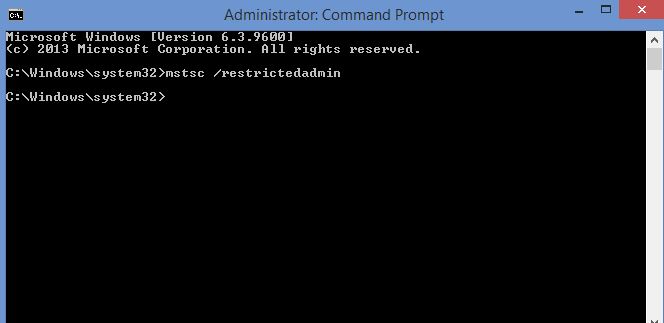
Once changes are made can connect to target with using one of following methods,
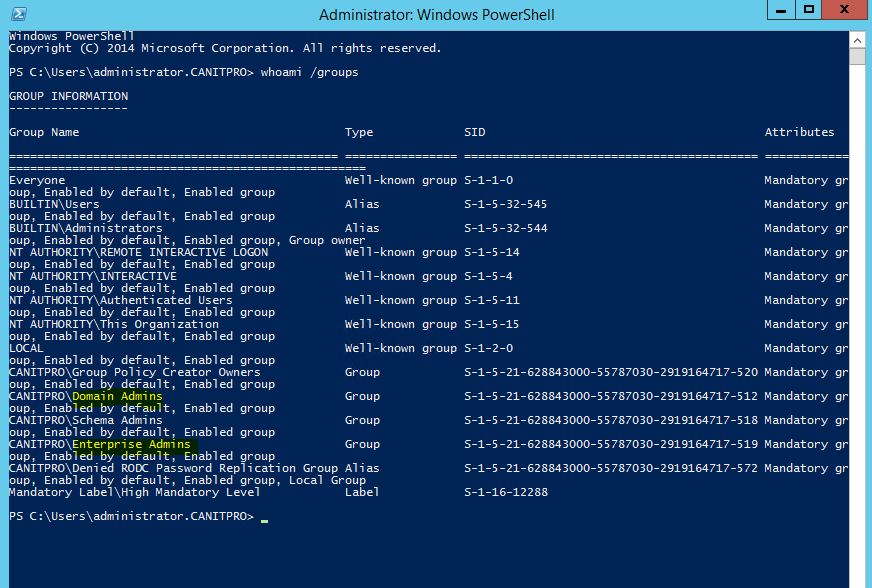
In my testing I am using a member server in domain and I am login in with Domain admin account.
Now in the whoami /groups it shows I am a domain admin and enterprise admin.
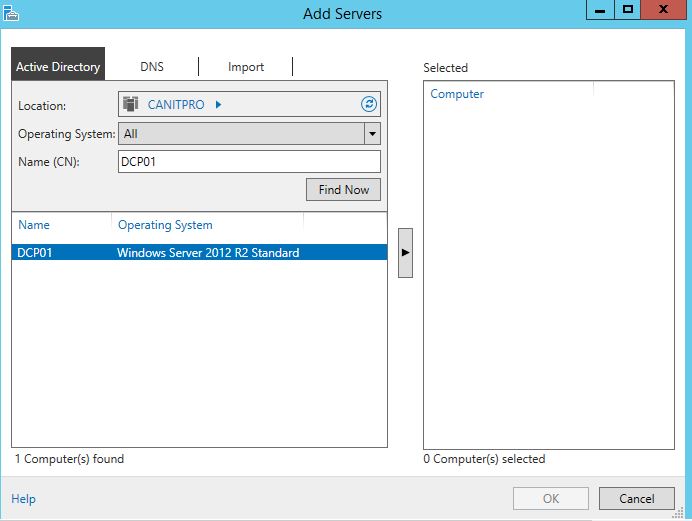
Now I am trying to connect to another server DCP01 using Server Manager
Then it gives access denied error even I am Domain admin.
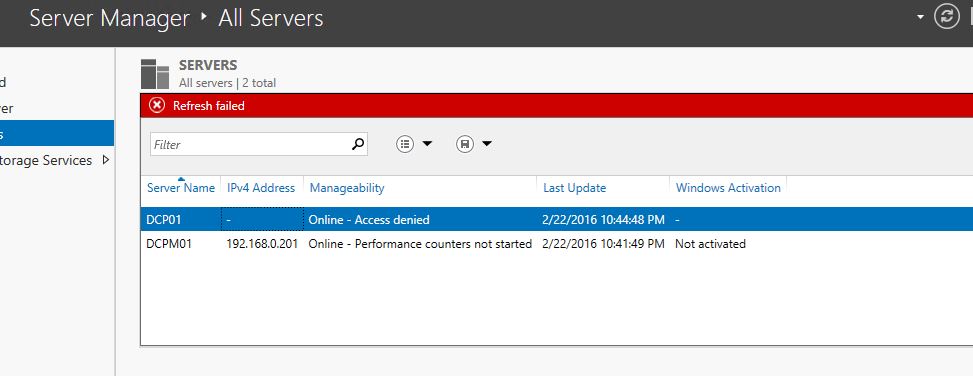
So yes with restrict mode you can’t connect to other network resources as its not passing the credentials.
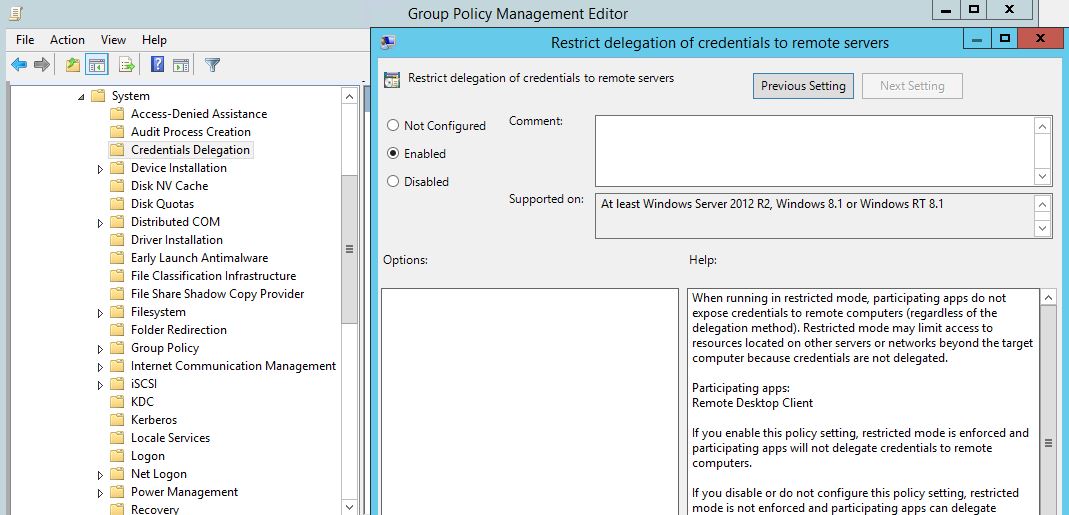
You can enable Restricted Admin Mode for computers using GPO. So when you use RDP client from those PC by default it will use Restricted Admin mode.
To do that in GPO go to Computer Configurations > Policies > Administrative Templates > System > Credential Delegation
Then Set Restrict Delegation of credential to remote servers to enable
Hope this article helps to understand Restricted Admin mode for RDP and way to use it.
If you got any questions feel free to contact me on rebeladm@live.com






In addition to restricted admin mode, one may use tools like on premise R-HUB remote support servers for remote access of computers. It is an on premise solution which works from behind the firewall, hence better security.