In my previous posts, we learn how PKI works and what are the PKI components. You can find those articles in following links,
How PKI Works? – http://www.rebeladmin.com/2018/05/how-pki-works/
Active directory certificate service components – http://www.rebeladmin.com/2018/05/active-directory-certificate-service-components/
In this post we are going to look in to different PKI deployment models. In several places in above articles, I have mentioned about the PKI hierarchy and components in it such as root CAs, Intermediate CAs and Issuing CAs. Based on the business and operation requirements, PKI topology will also change. There are three deployments models we can use to address the PKI requirements.
Single-Tier Model
This is also called as one-tier model and it is the simplest deployment model for PKI. This is NOT recommended to use in any production network as its single point of failure of entire PKI.
In this model, single CA will act as root CA and Issuing CA. as I explain before the root CA is the highest trusted CA in PKI hierarchy. Any compromise to root CA will be compromise entire PKI. In this model its one server, so any compromise on server will easily compromise entire PKI as it doesn’t need to spread through different hierarchy levels. This is model is easy to implement and easy to manage. Because of that event it’s not recommended, this model exists in corporate networks.
Some CA aware applications, required certificates in order to function. System center operation manager (SCOM) is one of the good example. It uses certificates on to secure web interfaces, to authenticate management servers and many more. If the organization doesn’t have internal CA, the options are to purchase certificates from vendor or to deploy a new CA. In similar situations engineers usually use this single-tier model as its only use for a specific application or task.
|
Advantages |
Disadvantages |
|
Less resources and Low Cost to manage as the its all running from single server. It also reduces the license cost for the operating systems. |
High possibility of getting compromise as root CA is online and running entire PKI related roles from one single server. If someone get access to private key of root CA he has complete ownership over the PKI |
|
Faster deployment and it is possible to get CA running in short period of time. |
Lack of redundancy as Certificate issuing and management all depend on single server and availability of it will decide the availability of PKI |
|
|
It is not scalable and it will need restructure the hierarchy if need to add more role servers. |
|
|
All the certificate issuing and management done by one server and all the work requests has to handle by it. it creates a performance bottleneck. |
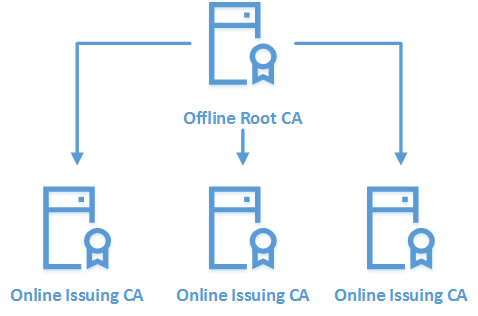
Two-Tier Model
This is the most commonly used PKI deployment model in corporate networks. By design the root CA need to keep offline and it will prevent private key of root certificate been compromised. root CA will issue certificates for subordinate CAs and Subordinate CAs are responsible for issuing certificates for objects and services.
|
Advantages |
Disadvantages |
|
Improved PKI security as root CA offline and it’s been protected by private key been compromised. |
High Maintenance – Need to maintain multiple systems and need skills to process the manual certificates request/approval/renewal between root CA and subordinate CA |
|
Flexible scalability – Can start small and expand by adding additional subordinate CAs when required. |
Cost – Cost of resources and licenses are high compare to Single-Tier model |
|
Restrict Issuing CA impact in CA hierarchy by controlling certificates scope. It will prevent issuing “rouge” certificates. |
Manual certificate renewal process between root CA and subordinate CAs adds additional risks as if administrators forgot to renew it on time it can bring whole PKI down. |
|
Improved performances as workloads can shared among multiple subordinate CAs. |
|
|
Flexible maintenance capabilities as less dependencies. |
|
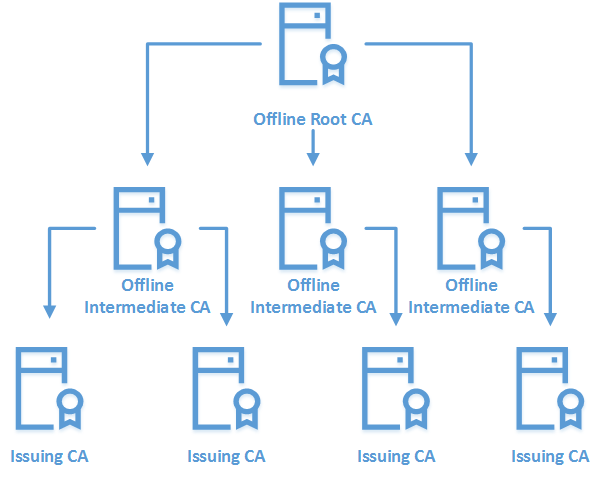
Three-Tier Model
Three-Tier model is the highest in the model list which operates with greater security, scalability and control. Similar to two-tier model it also has offline root CA and online Issuing CAs. Addition to that there will be offline intermediate CAs which operates between root CA and subordinate CAs. Main reason for it is to operate intermediate CAs as Policy CAs. In larger organizations, different departments, different sites, different operation units can have different certificate requirements. As an example, a certificate issued to a perimeter network will required manual approval process while others users in corporate network prefer auto approval. IT team prefer to have advanced Cryptography provider for its certificates and large key while other users operates with default RSA algorithm. All these different requirements are defined by the Policy CA and it publish the relevant templates, procedures to the other CAs.
|
Advantages |
Disadvantage |
|
Improved security as it adds another layer of CAs to the certificate verification. |
Cost – Cost of resources and licensee are high as its need to maintain three layers. It also increases the operation cost. |
|
Greater scalability as each tier can span horizontally. |
High Maintenance – When number of servers increases the efforts need to maintain those also increases. Both tiers which operates standalone CAs required additional maintenance as its not supported for automatic certificate request/approval/renewal. |
|
In event of compromise of issuing CA, intermediate CA can revoke the compromised CA with minimum impact to existing setup |
Implementation Complexity is high compare to other models. |
|
High Performance setup as workloads are distributed and administrative boundaries are well defined by intermediate CAs. |
|
|
Improved control over certificate policies and allow enterprise to have tailored certificates. |
|
|
High availability as dependencies further reduced. |
|
This marks the end of this blog post. In next post we are going to look in to deployment of AD CS. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.




What will be Solution for HA Mode ? 2 Tier Model ?