In on-premises Active Directory environment, we use “trusts” to establish identity infrastructure connection between businesses. Based on trust type and access permissions, users from one organization can access resources/services in other infrastructure using their own domain credentials. Azure AD B2B does the same thing for cloud resources but in much more easier way. In this demo I am going to demonstrate how easily we can allow users from other organizations to access our cloud resources using Azure AD B2B.
In my demo environment, I do have an Azure AD user group called sg-Finance . All the users from Finance department are members of this group. I have assign several SaaS applications to them. Company Contoso recently merge with another company. Few privileged users from new company like to access some financial data belongs to Contoso. The relevant data is currently available via SaaS applications which is used by sg-Finance group members. In this demo, I am going to invite external user to be part of sg-Finance group so they can access same applications.
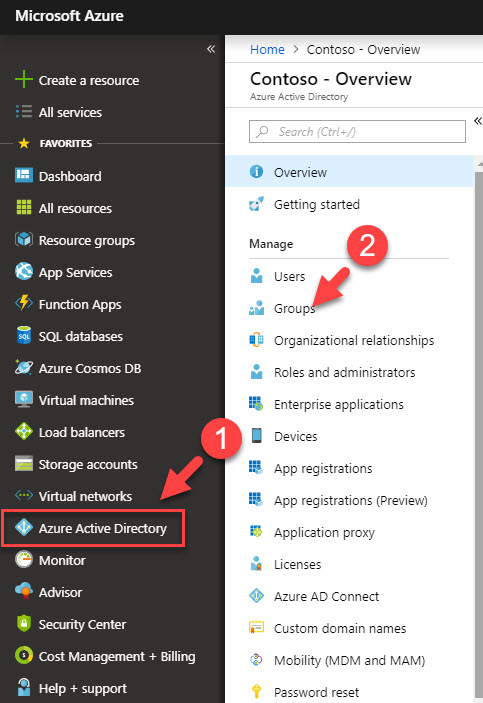
1. To start, log in to Azure Portal https://portal.azure.com as Global Administrator
2. Then go to Azure Active Directory | Groups
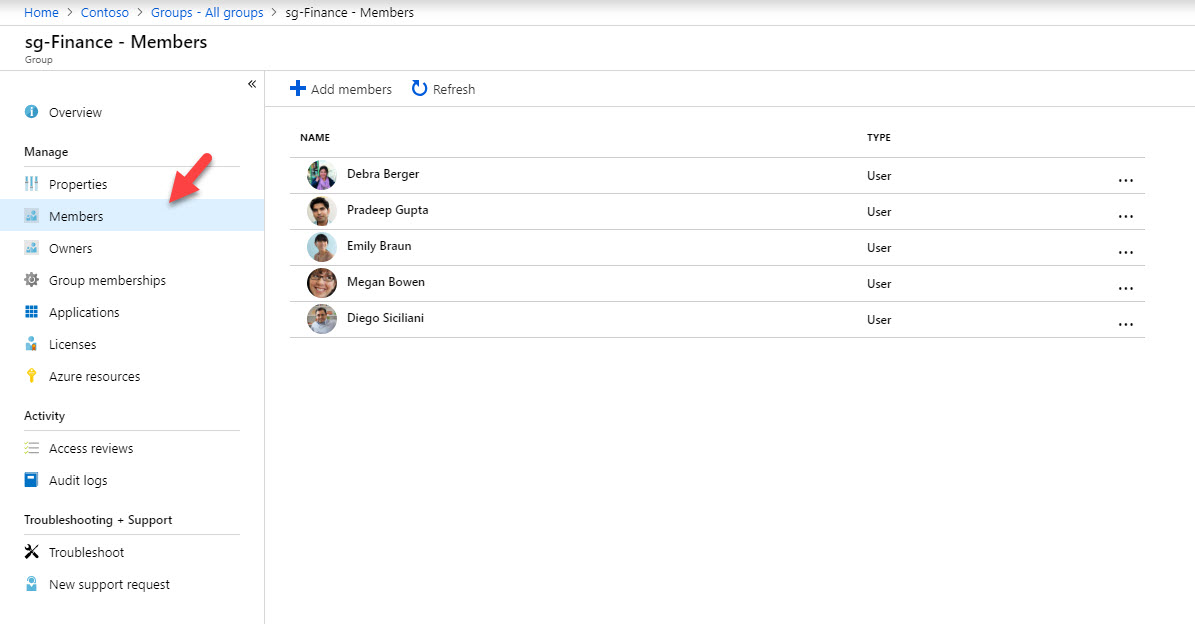
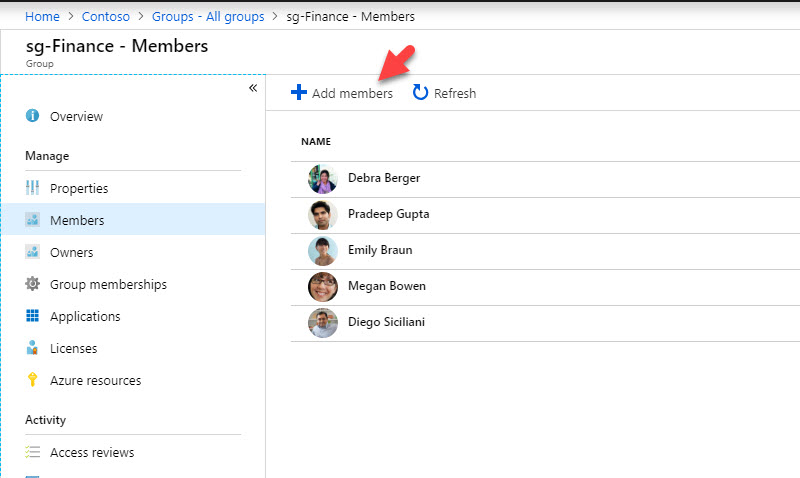
3. Then go to sg-Finance group and then Members.
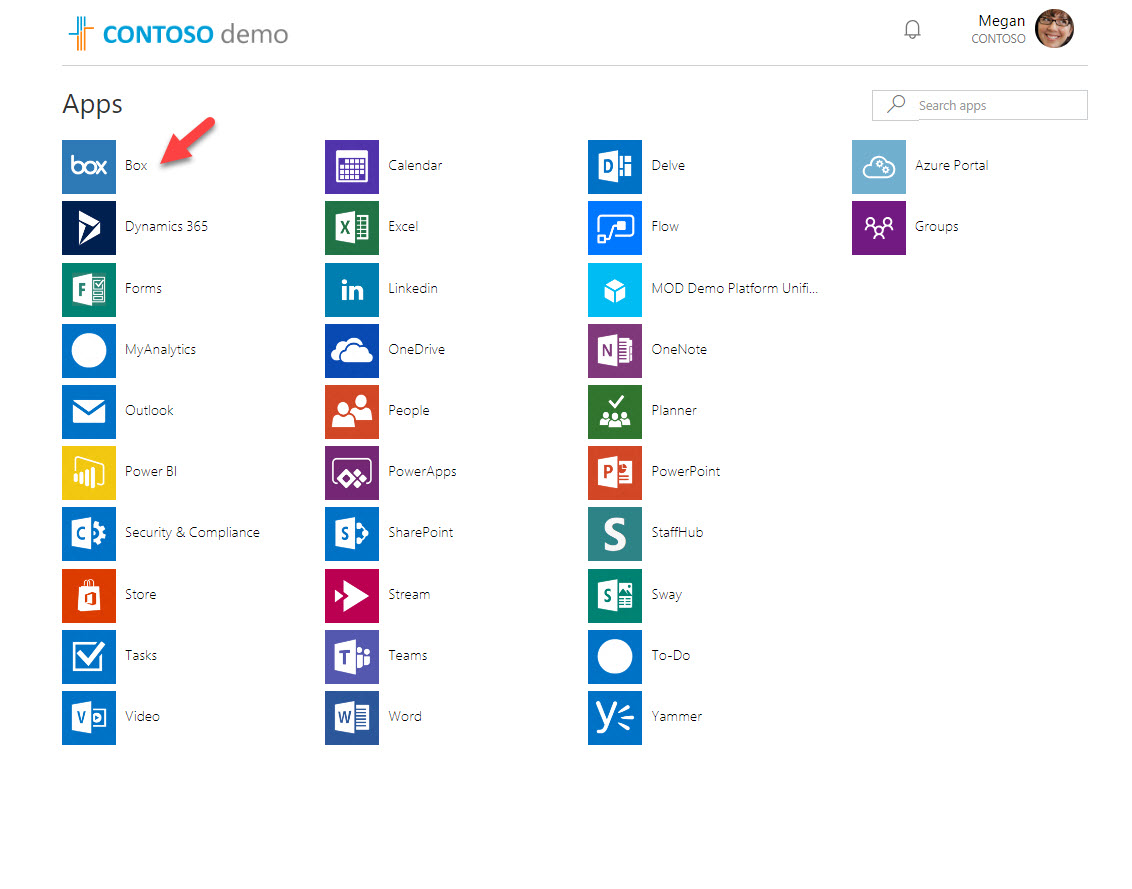
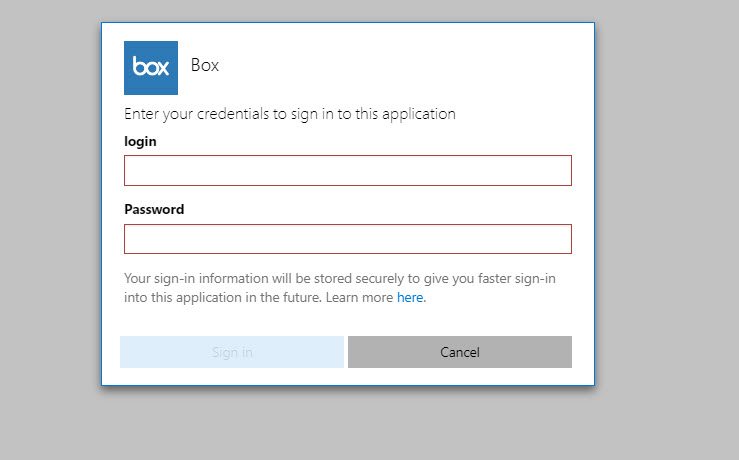
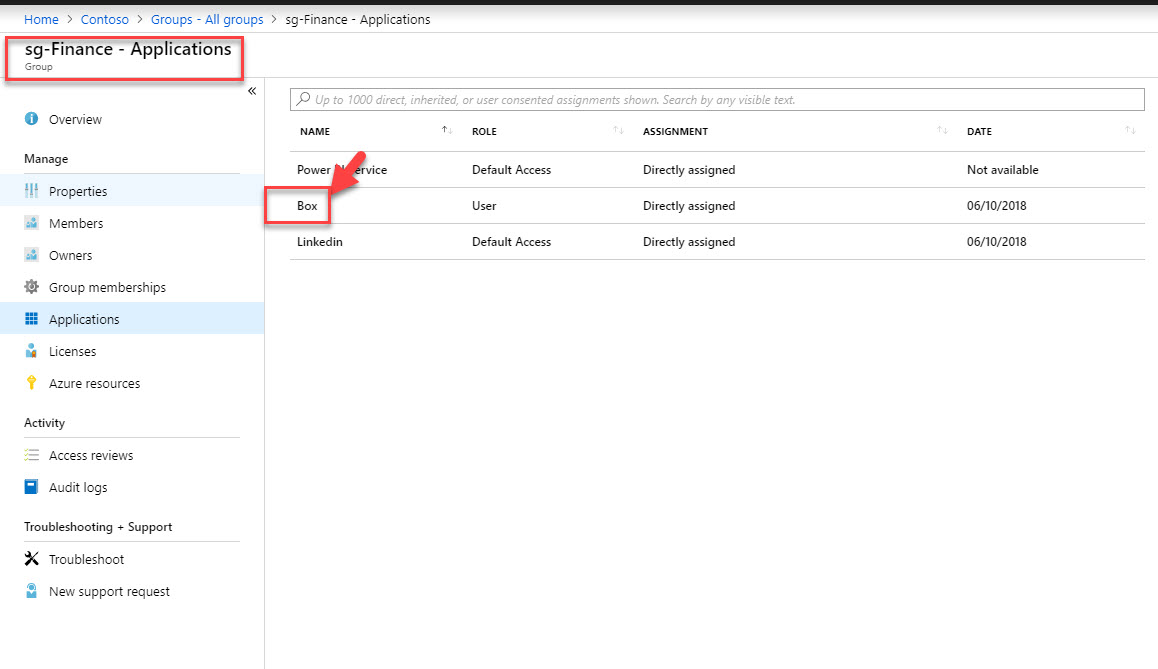
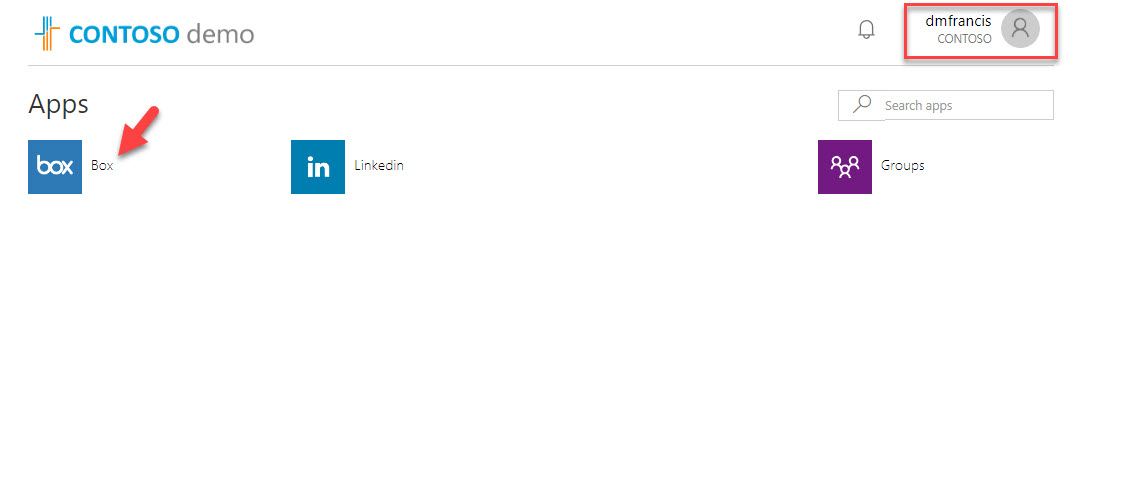
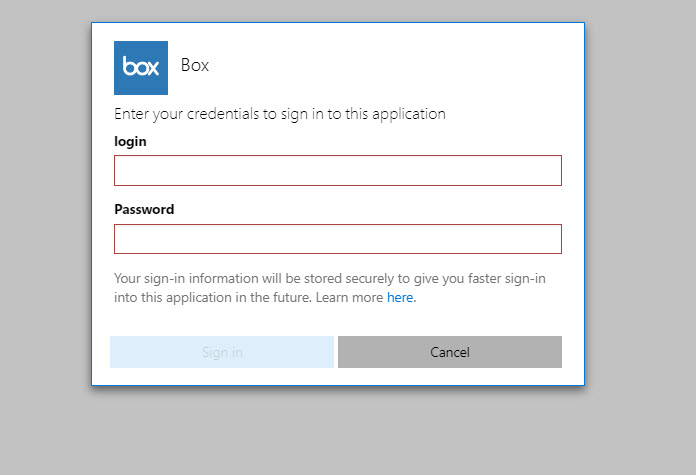
4. In here, Megan is a member of this group. I log in to http://myapps.microsoft.com as Megan to verify SaaS application access. In this demo I am using Box as sample app.
5. Now go back to group page and click on Add members
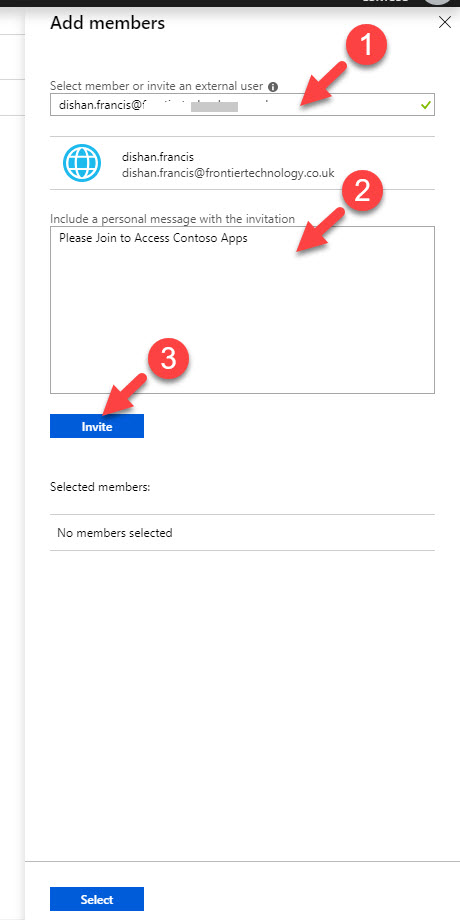
6. In new window, type the email address for the external user. Then type a message and click on Invite.
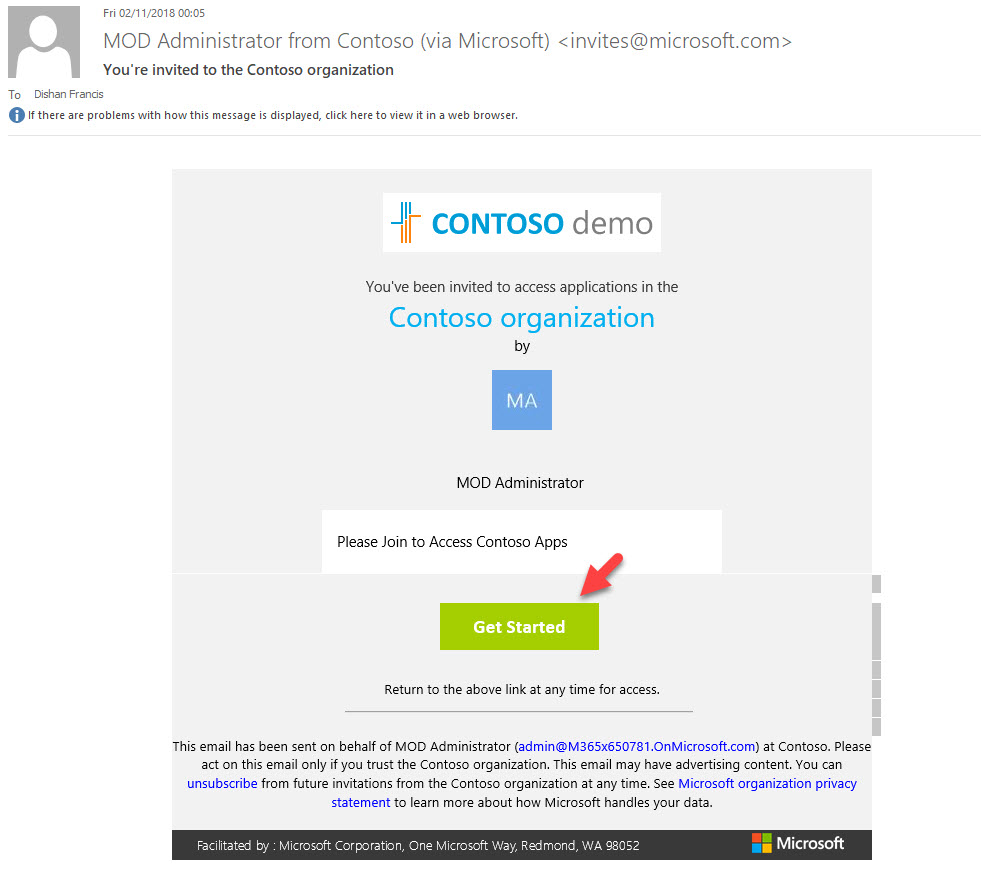
7. After few seconds, external user will receive email similar to below. To sign up, external user need to click on Get Started button.
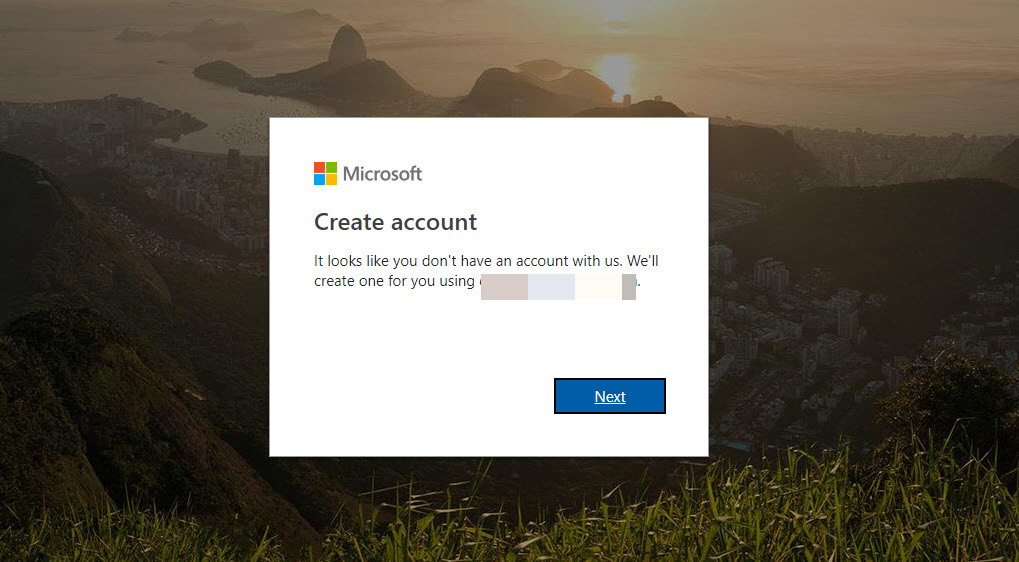
8. Then user get option to create new Microsoft account, if he/she do not have one already.
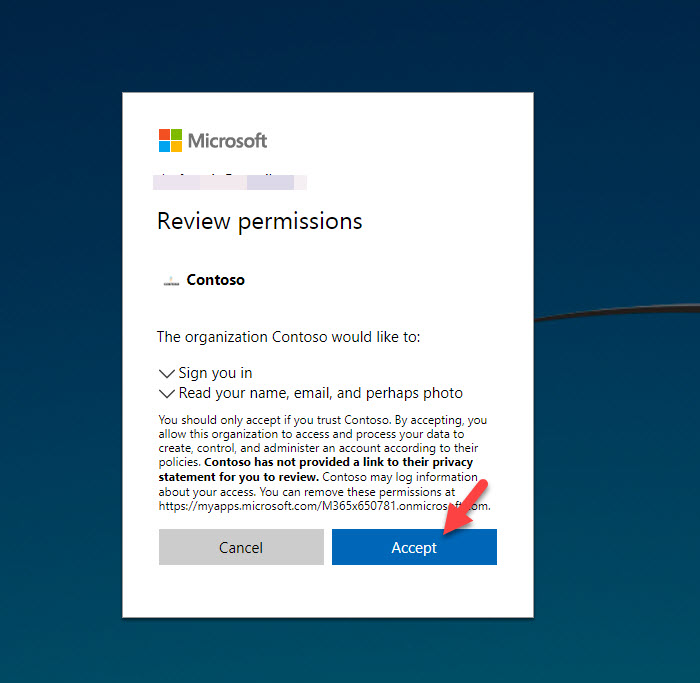
9. At the end of sign up process click on Accept permissions to complete the process.
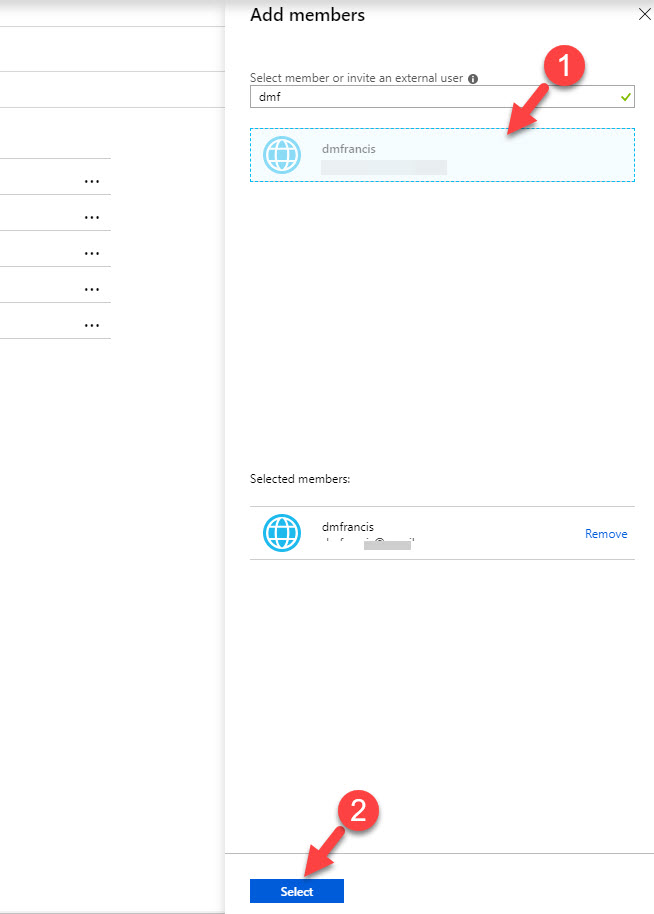
10. Once sign up process completed, go back to add members page (under sg-Finance group) and search for the new external user. Once it appears in the list, click on Select
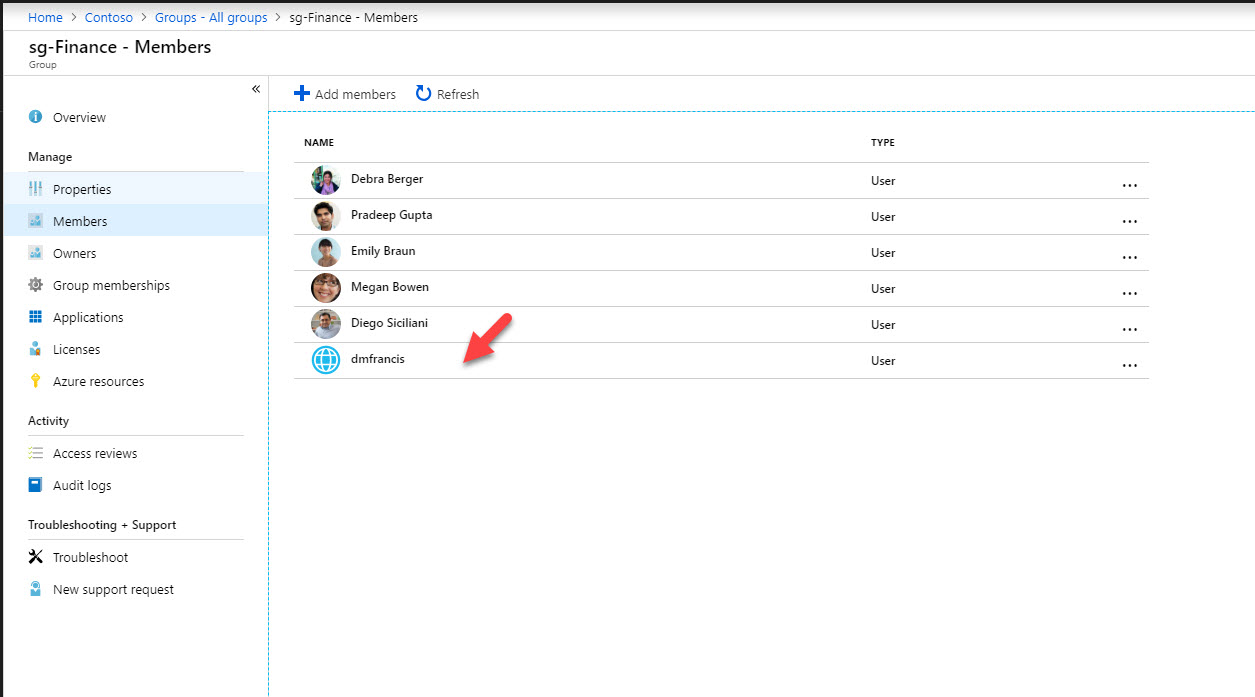
11. After that, we can see the new user under the members.
12. Now it’s time for testing, I went ahead and log in to http://myapps.microsoft.com as external user and was able to access Box app as expected.
As we can see, with few clicks we were able to assign permission to external user and make him a part of an Azure AD group. This marks the end of this blog post. If you have any further questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.