In my previous blog post, I illustrated the process of enabling Windows LAPS with Azure AD using Group policies. In that discussion, we focused on devices that are Hybrid Azure AD Joined. Another approach to configuring the Windows LAPS settings is through Microsoft Intune. If the corporate devices are already managed using Microsoft Intune, we can effortlessly create a LAPS policy to configure the LAPS settings on endpoints.
In this blog post, I am going to demonstrate how we can set up LAPS policy using Microsoft Intune.
Prerequisites
1. Devices need to be successfully onboard to Microsoft Intune.
2. Need a user account with appropriate permissions to set up and manage LAPS Intune policy. By default, the relevant permissions are granted to Endpoint Security Manager built-in role. Also, you can use a custom role with appropriate permissions explained here.
3. Local Administrator Password Solution (LAPS) (Preview) feature should be enabled.
To enable this feature to follow the steps in my previous blog post https://www.rebeladmin.com/2023/06/how-to-configure-windows-laps-with-azure-ad/
After ensuring that all the prerequisites have been met, the next step is to create a LAPS policy.
Create LAPS Policy
To create policy,
1. Log in to https://endpoint.microsoft.com/ as Endpoint Security Manager or a user who has appropriate permissions to create LAPS policy.
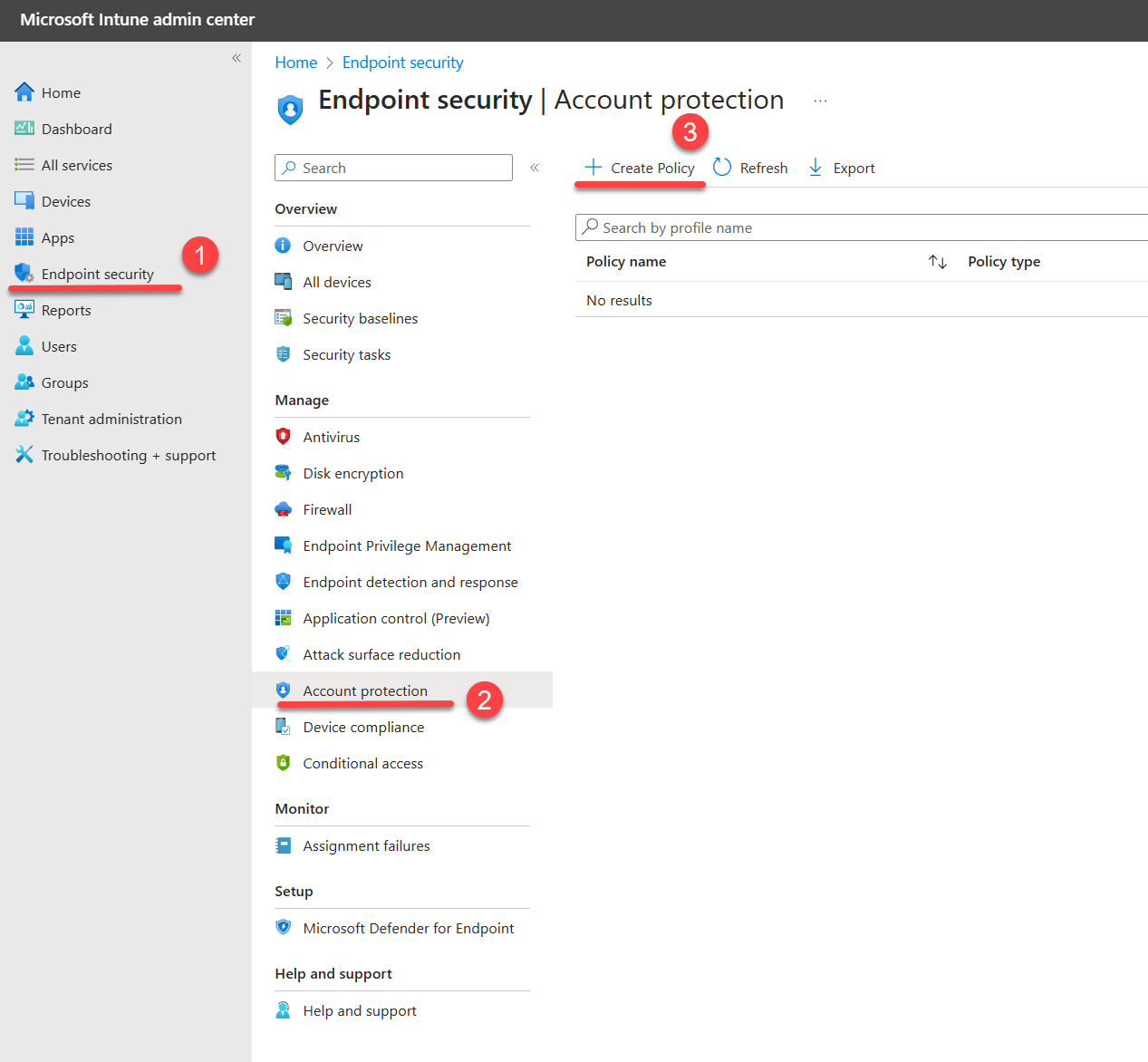
2. Go to Endpoint security | Account protection | + Create Policy
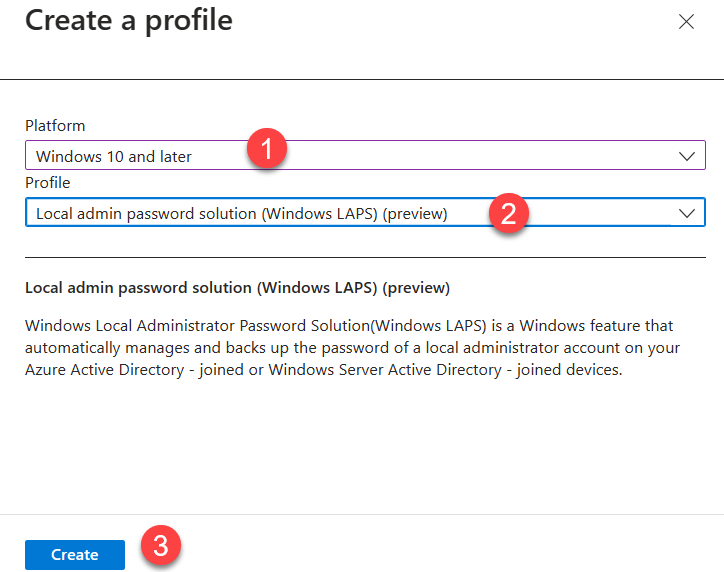
3. In the policy window select Windows 10 and later as Platform and Local admin password solution (Windows LAPS) (preview) as Profile. Then press Create
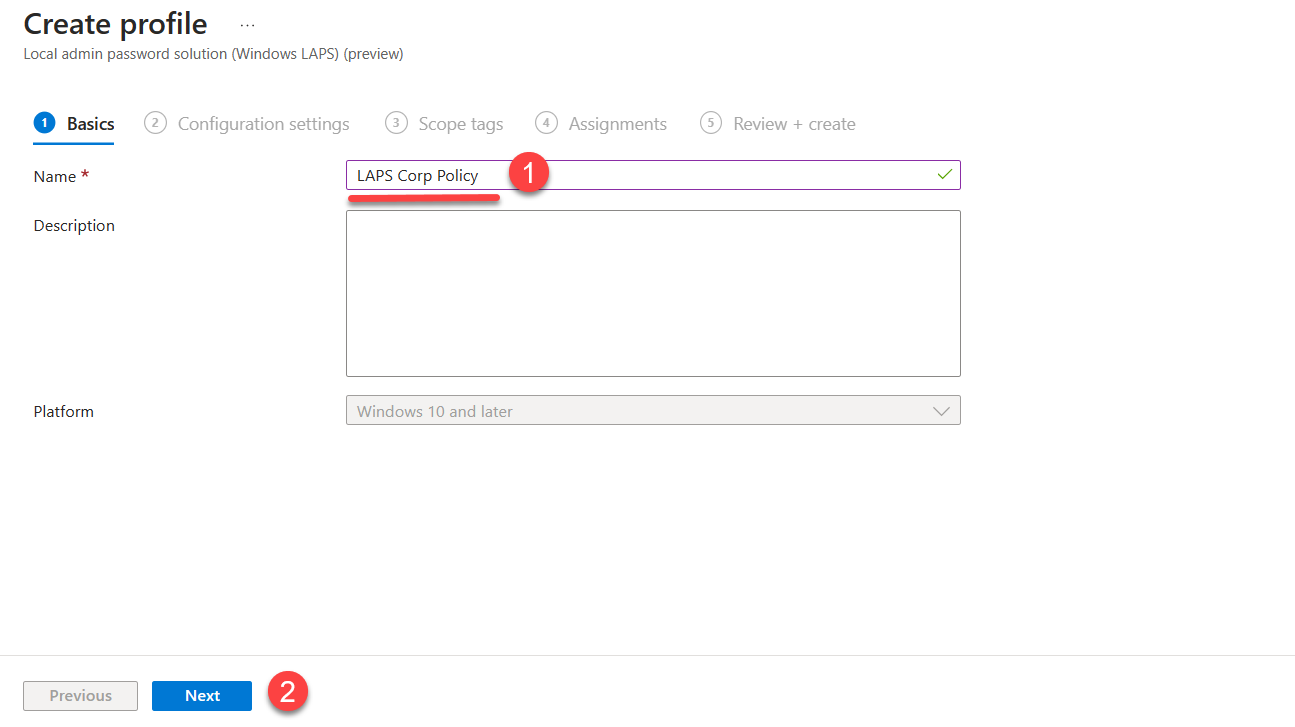
4. In the policy wizard, define Name for the policy and click on Next
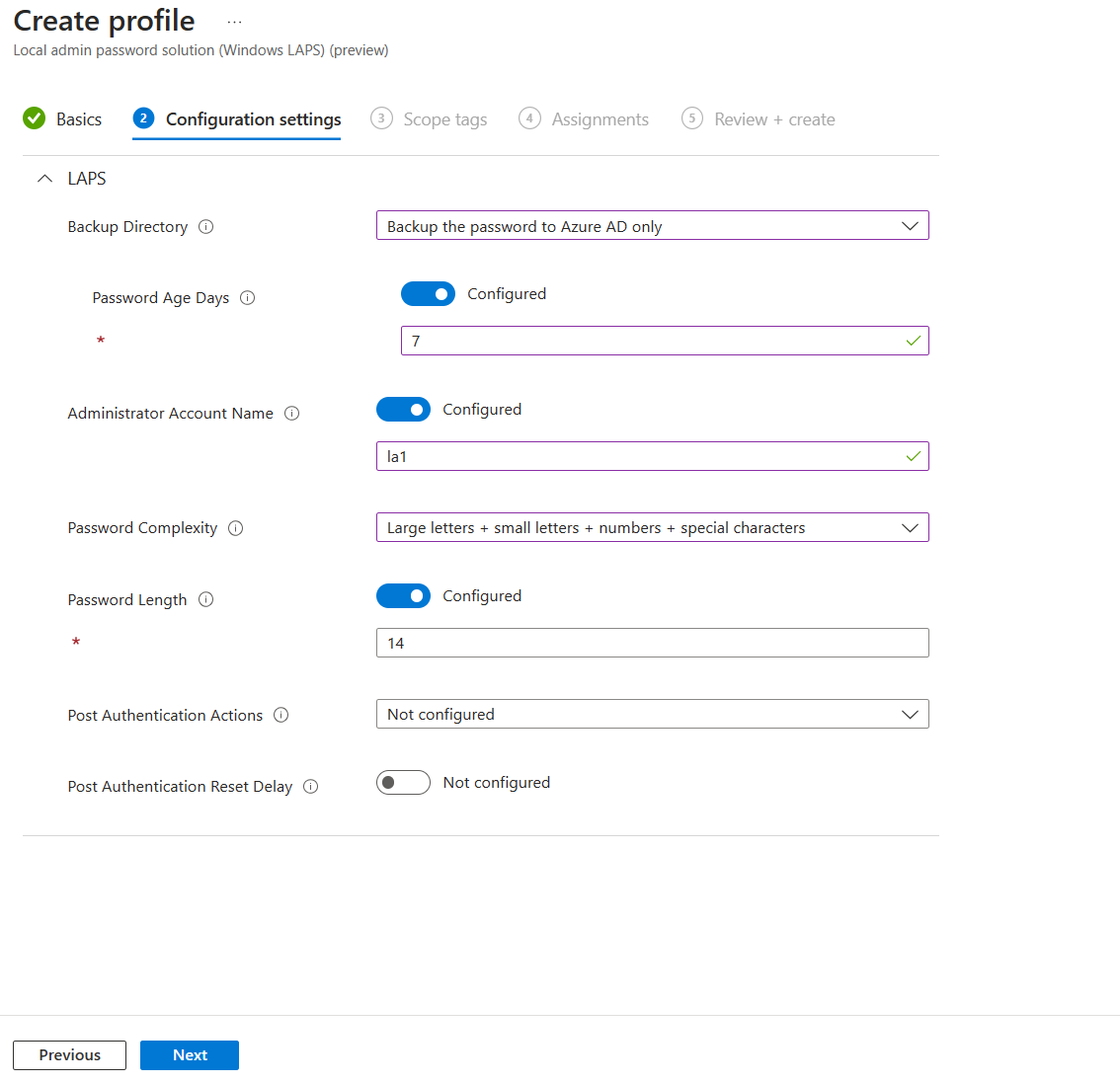
5. In the configuration window, make sure to select Backup the password to Azure AD only option under Backup Directory. After that can configure the rest of the settings according to IT requirements. These settings are similar to what you can configure from GPO. For my demo environment, I have defined the following settings,
• Password Age – 7 days
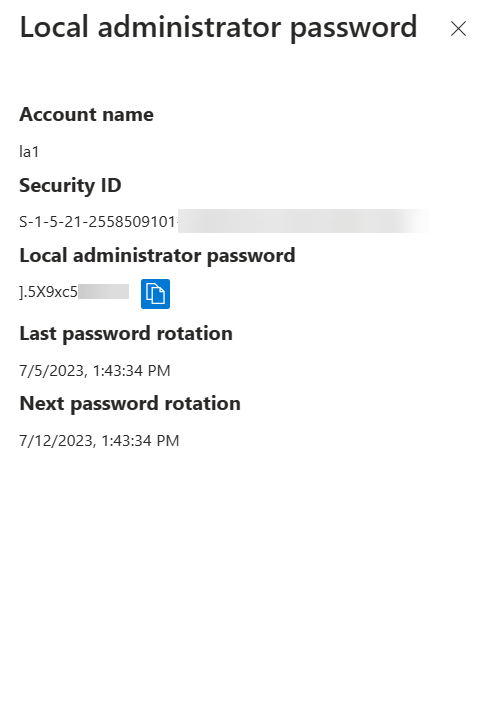
• Administrator Account Name – la1
• Password complexity – Large letters + small letters + numbers + special characters
• Password Length – 14
Note – If you are going to use a custom administrator account, make sure the account already exists in the endpoints as a local administrator. If the account does not exist, The policy will not create the account.
6. Keep the default in the Scope tags page and click Next.
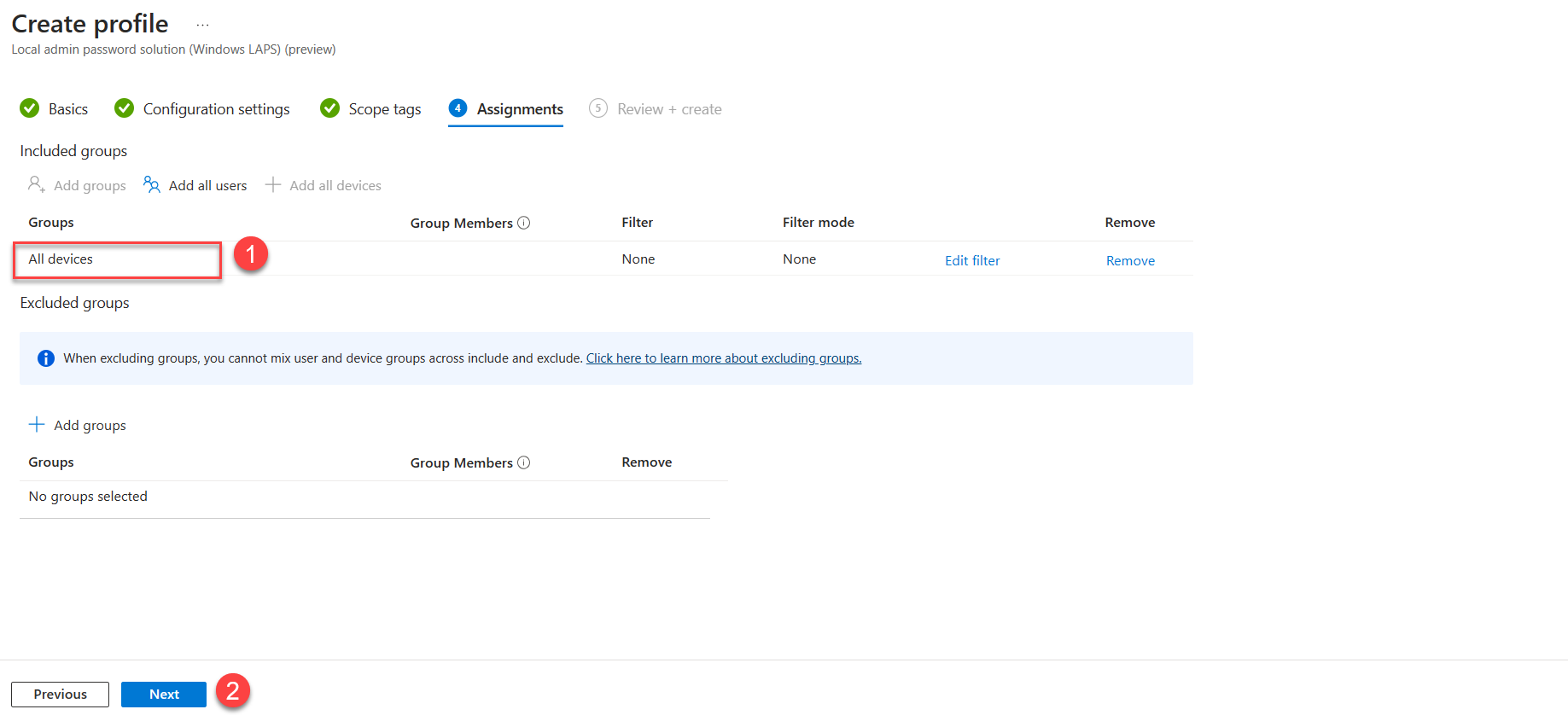
7. In Assignments, define the policy targets. You can choose a specific device group for this or else use + Add all devices option.
8. In the Review + create page, review the policy settings and click on Create to complete the policy configuration.
Testing
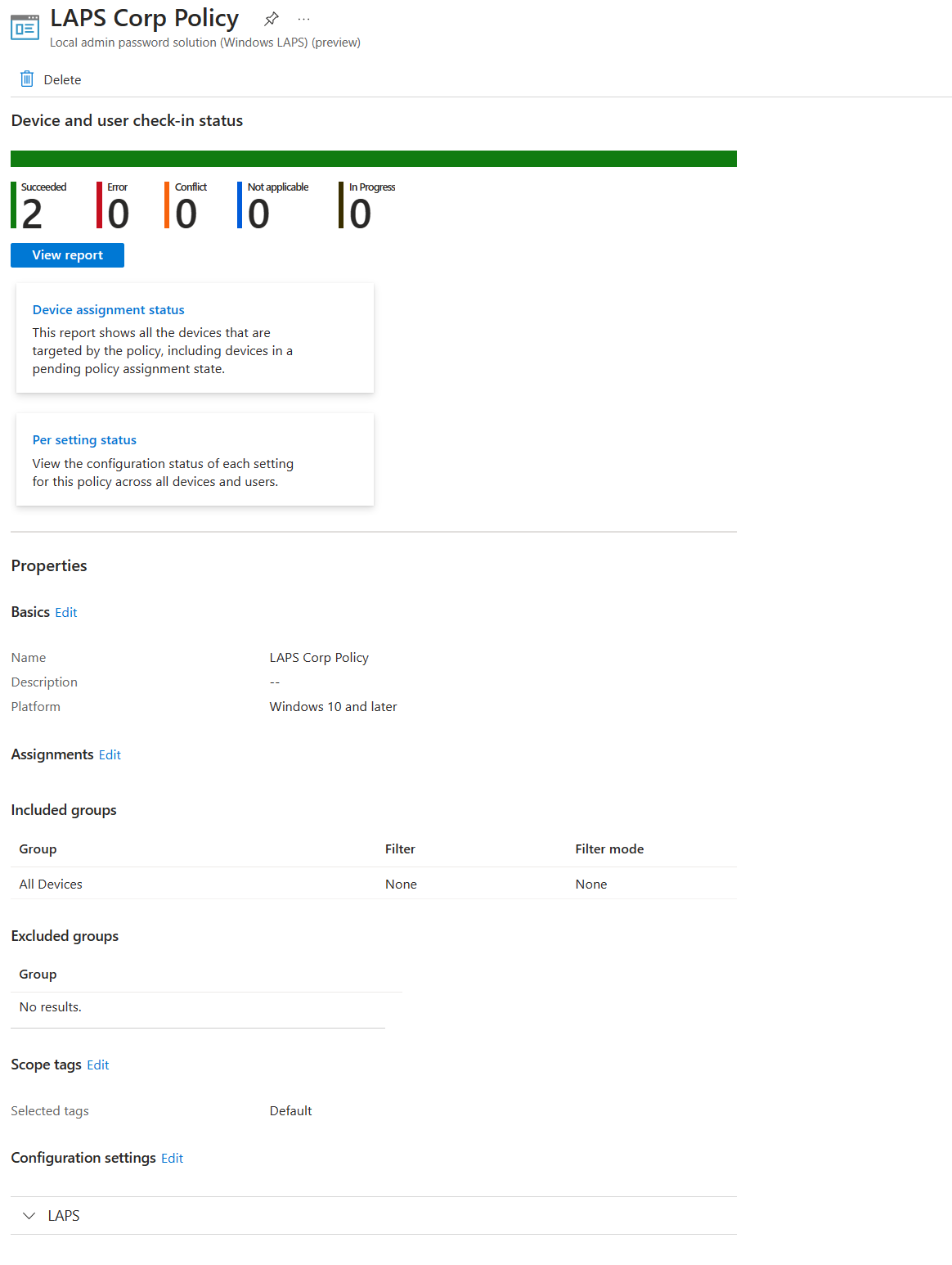
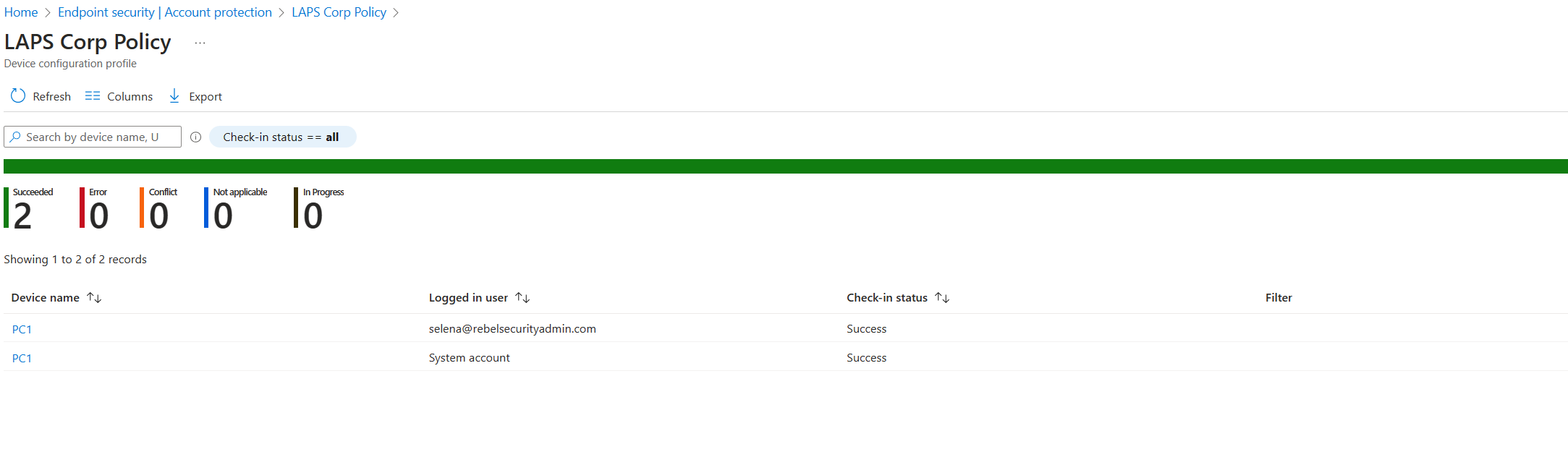
Once the policy is pushed out, you can see the policy status from the policy overview page.
To do that you can click on the newly created policy in Endpoint security | Account protection
As we can see the policy sync successfully.
Let’s go ahead and check the local admin password details. To do that, we need an account with one of the following roles assigned,
• Global Admin
• Cloud Device Admin
To view account and password details,
1. Log in to https://endpoint.microsoft.com/ as one of the above-mentioned user.
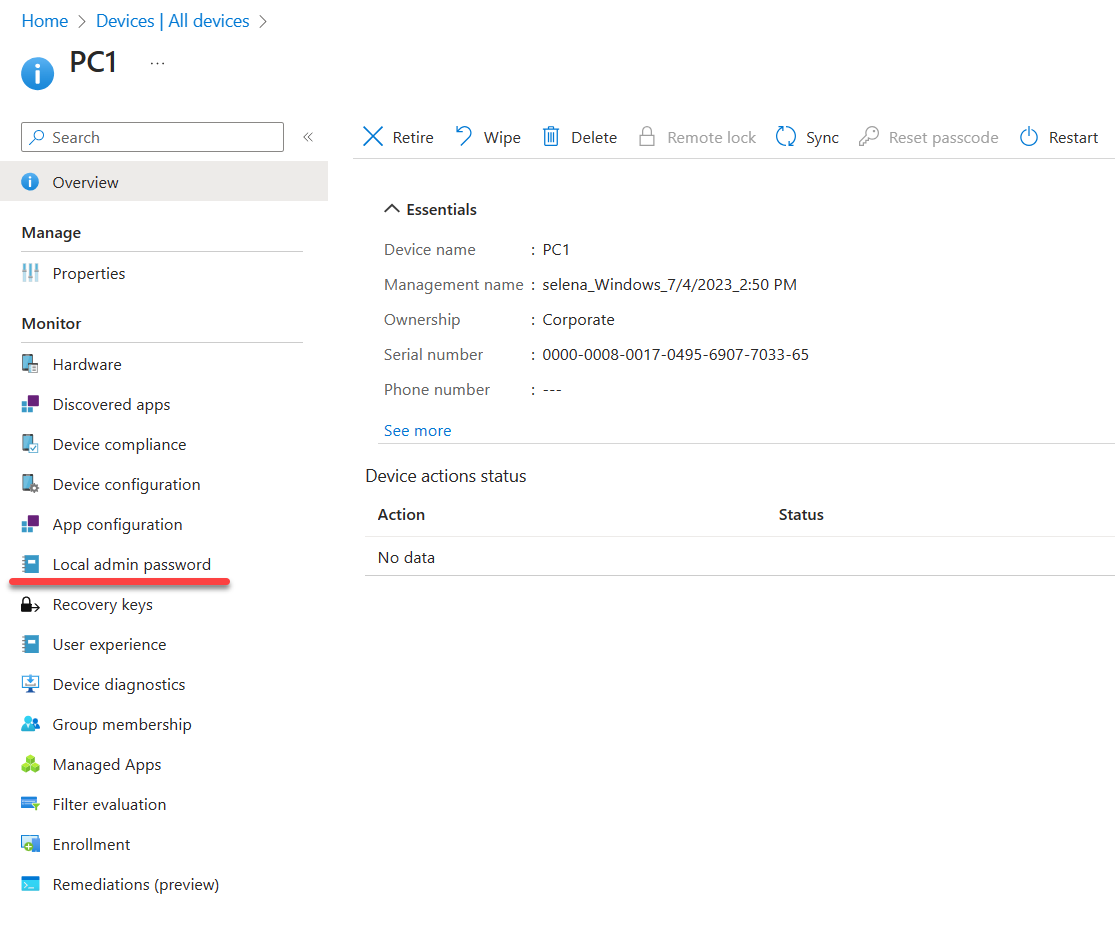
2. Then click on Devices | All devices
3. From the list, click on a device that has the LAPS policy applied.
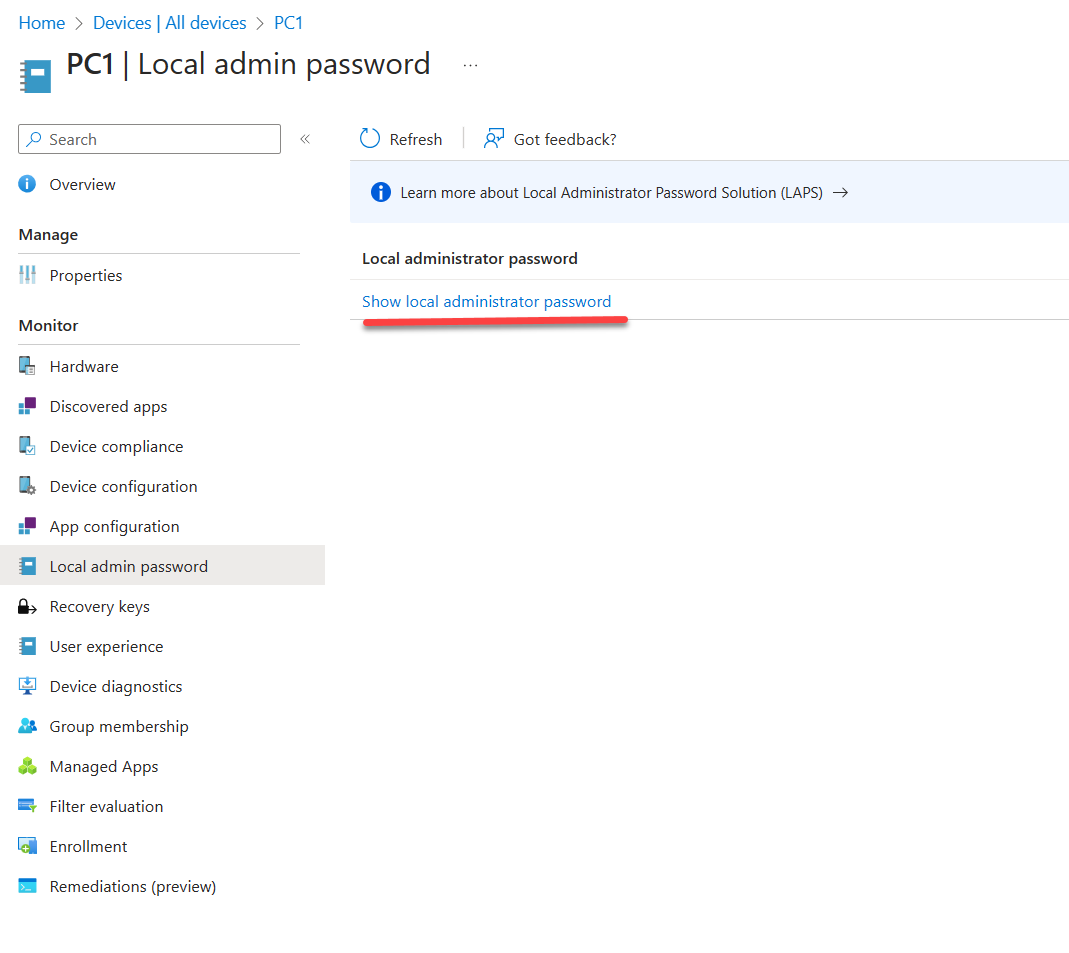
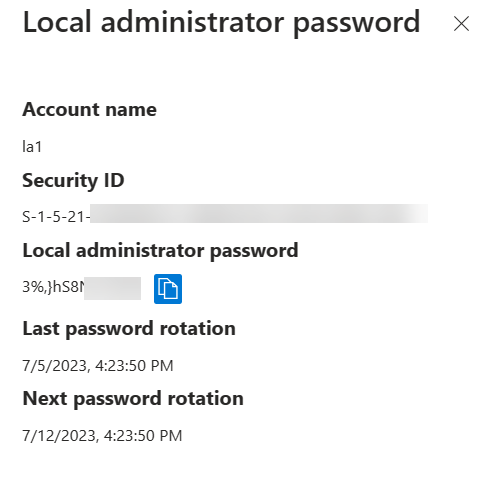
4. On device property page, click on Local admin password.
5. Then click on Show local administrator password to reveal the account and password details.
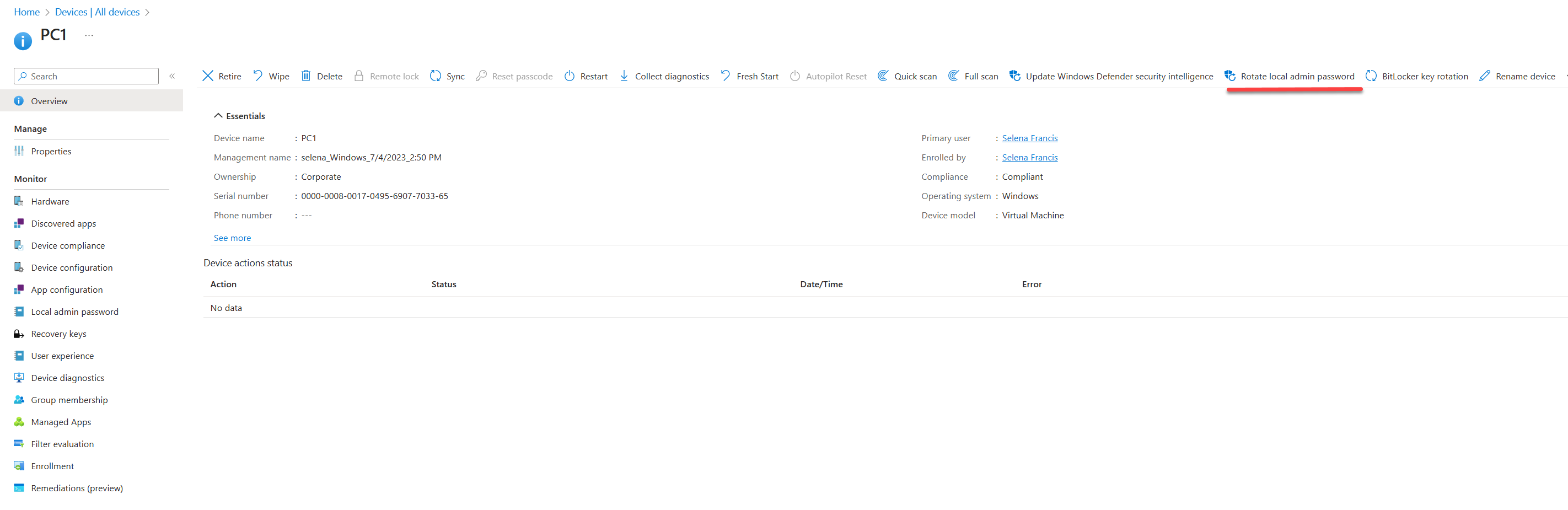
Using Intune we also can forcefully rotate the local admin password.
To do that we need to log in to Intune with an account that has the following permissions.
• Managed devices: Read
• Organization: Read
• Remote tasks: Rotate Local Admin Password
Once logged in to https://endpoint.microsoft.com/ as a user who has the above-mentioned permissions, go to the relevant device overview page and then click on Rotate local admin password
After a few minutes, we can see a new password for the local admin account. Please note this activity will reset the Password age.
As we can see Windows LAPS configuration via Microsoft Intune is working as expected. This marks the end of the blog post and if you have any questions feel free to reach me at rebeladm@live.com