What will happen if you have deleted the wrong user account? Or any other AD object? In your AD environment. “Recovery” is the answer but issue is how fast and how easy you can do it.
Once active directory object is deleted, it is automatically goes in to the deleted object container in the AD. Then during the active directory garbage collection process it will clean up these deleted AD objects permanently. By default this process is occurs in every 12 hours. So if need to recover a deleted object (unless you use an active directory backup) it is possible to do before the garbage collection process occurs in AD using LPD.exe tool. But the issue is even you can recover the object along with metadata it will lose its some attributes such as group membership.
Microsoft has come with a feature to answer this. It starts with windows server 2008 R2 and called as “Active Directory Recycle Bin”. This feature is exactly work as “Recycle Bin” in windows operating system. You can use this to undelete any deleted AD objects. More importantly you can restore it with few clicks along with all the attributes. By default AD recycle bin holds deleted objects for 180 days before permanently remove from the system.
This feature is need to be enabled manually in active directory. To use this feature the domain forest functional level at least need to be set to windows server 2008 R2. Also you need to manually enable this feature and once this feature is enabled you can’t disable it.
Let’s see how we can do this. In my demo I am using active directory runs on windows server 2012 R2.
1) Log in to the Domain Controller as member of domain admin group or enterprise admin group.
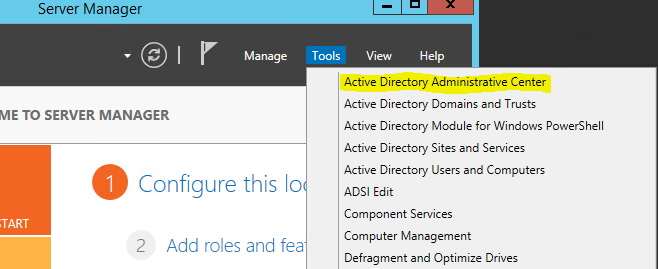
2) Then Server Manager > Tools > Active Directory Administrative Center
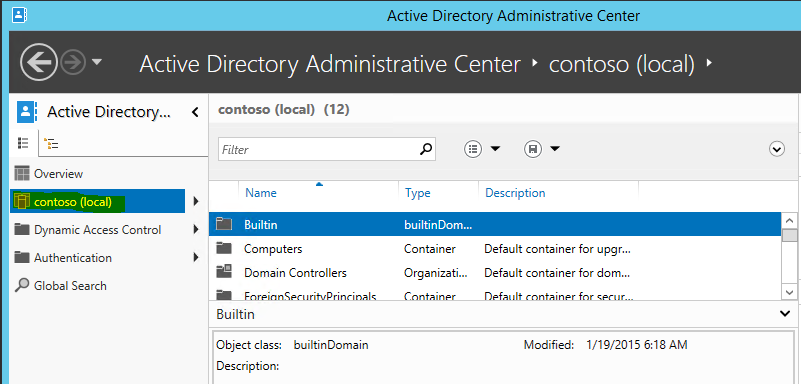
3) It will open Active Directory Administrative Center mmc and click on the domain name
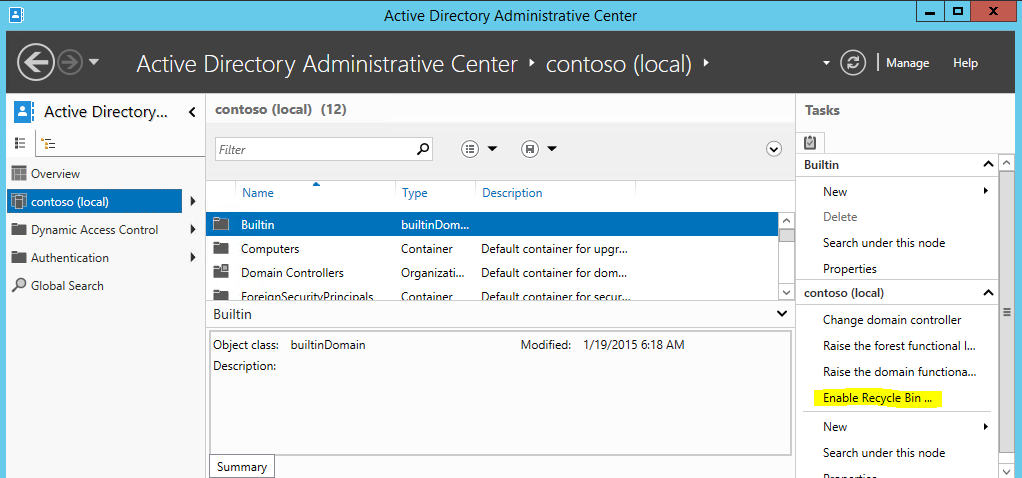
4) Then under Tasks panel click on “Enable Recycle Bin”
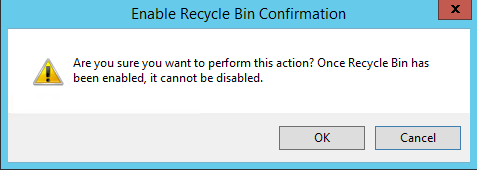
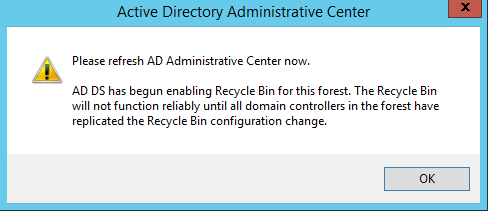
5) Once click on it, it will open up pop up saying to confirm the action. As I mentioned earlier once this feature is enable you can’t disable it.
6) Then it will give info window about the function and the replication. Click ok to exit form window.
It will take some time to replicate across the domain controller in the forest. After replication it’s time to test the functions and see how the restore process works.
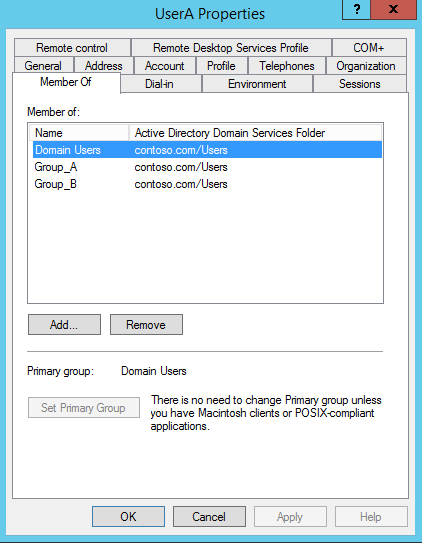
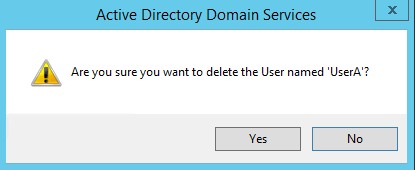
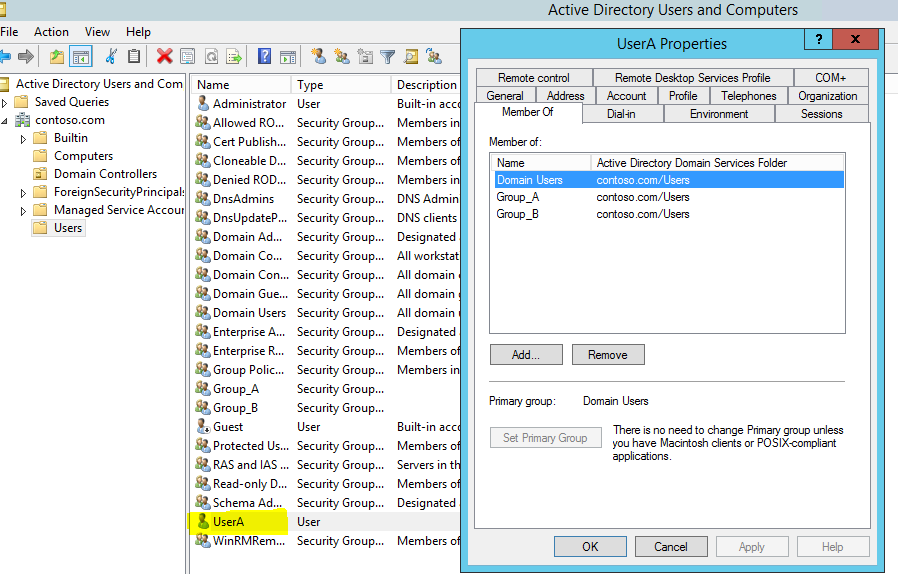
For my demo I am using a user account called “User A” and he is member of Gorup_A and Group_B as well. I am going to delete the user and recover it using the AD recycle bin feature.
To recover the object
1) Go to Server Manager > Tools > Active Directory Administrative Center
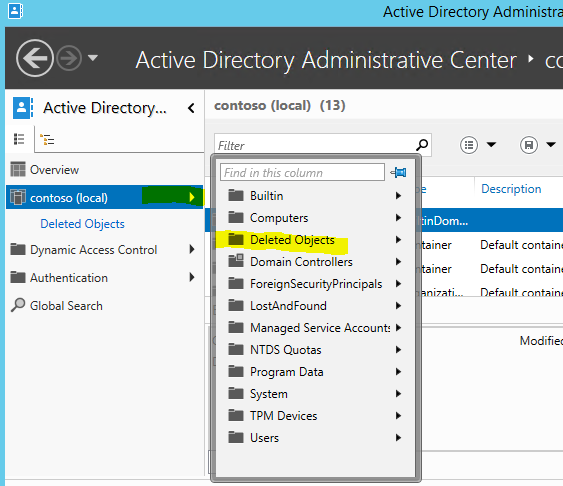
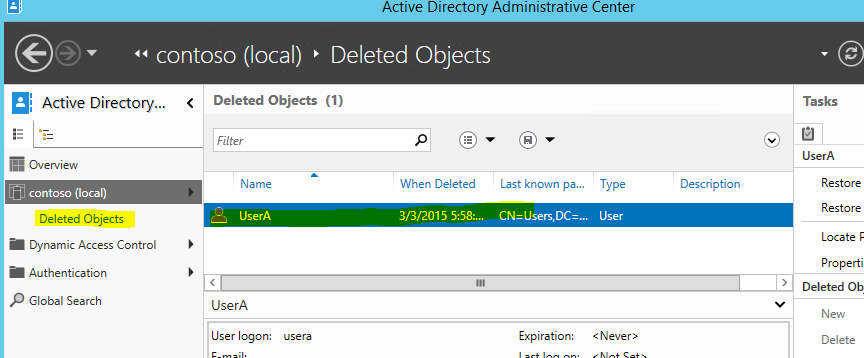
2) Then click on domain name and the arrow in front. Then click on option “Deleted Objects”
3) Then it will show the objects captured by the AD recycle bin feature. In here we can see the UserA account I have just deleted.
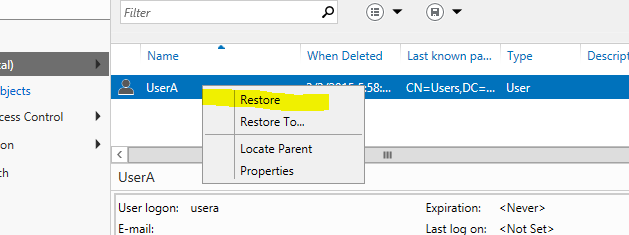
4) To restore the object, right click on object and select “Restore”. This will restore it to original location it was. If you need you also can select which container it should restore to using “restore to” option.
5) Now in AD I can see the restored object along with its attributes.
So as you can see it was very fast and effective solution. This is the end of this article and if you have any questions feel free to contact me on rebeladm@live.com




so gud