Users or groups access and permissions to a shared folder is controlled by its Access Control List (ACL). Similar way we can define permissions to Active Directory Objects. This can apply to individual object or apply to AD Site/Domain/OU and then inherit to lower level objects.
As an Example, I have a security group called “First Line Engineers” and Liam is a member of this group. Liam is engineer of Europe office. In active directory environment, he should allow to add user objects under any sub OU in “Europe” OU. But he should not be allowed to delete any object under it. Let’s see how we can do it using ACLs.
1) Log in to Domain Controller as Domain Admin/Enterprise Admin
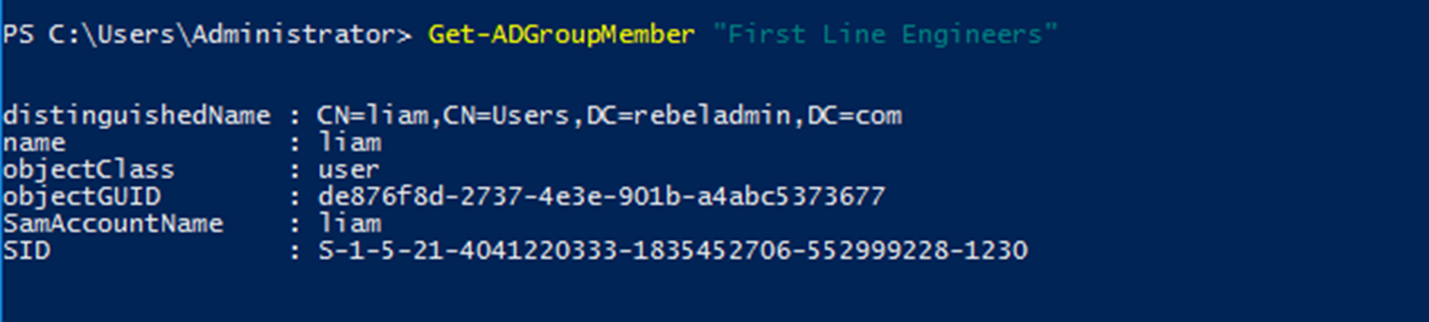
2) Review Group Membership Using
Get-ADGroupMember “First Line Engineers”
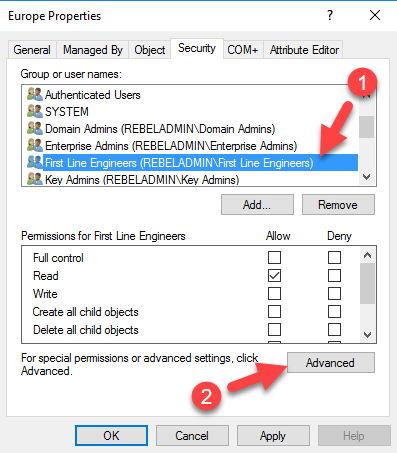
3) Go to ADUC, right click on the Europe OU and click properties. Then go to Security tab.
4) In security tab, click on Add
5) In the new window, type First Line Engineers and click Ok. After, In Security Tab, select First Line Engineers and click on Advanced
6) In next window, select the First Line Engineers from the list and click on Edit
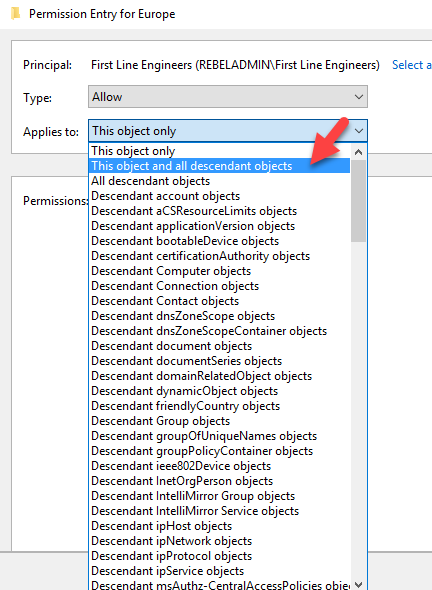
7) From Applies to list select “This object and all descendant objects”. Then it will apply permission to all child objects.
8) Under the Permissions section, tick Create All child objects and click Ok.
9) Then keep clicking Ok until all permission window closed.
10) Then I log in to Windows 10 computer which has RSAT tools installed as user Liam.
11) According to permissions, he should be able to add user account under Europe OU.
New-ADUser -Name "Dale" -Path "OU=Users,OU=Europe,DC=rebeladmin,DC=com"
This successfully add the user. Let’s see if we can add another user on different OU.
New-ADUser -Name "Simon" -Path "OU=Users,OU=Asia,DC=rebeladmin,DC=com"
And as soon as I run it, I gets access denied error.
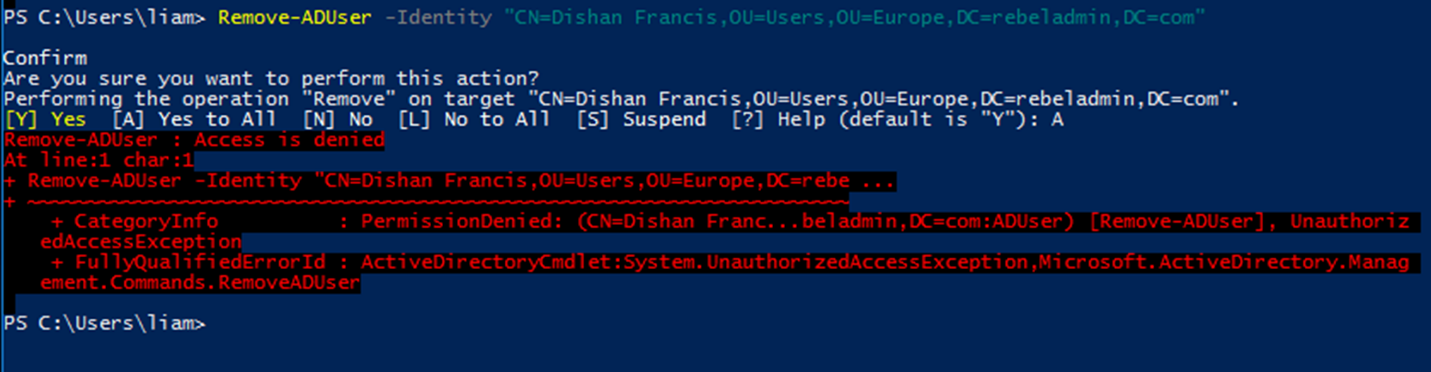
According to applied permissions, I should not be able to delete any object under OU=Users,OU=Europe,DC=rebeladmin,DC=com either. Let’s check it using,
Remove-ADUser -Identity "CN=Dishan Francis,OU=Users,OU= Europe,DC=rebeladmin,DC=com"
And as soon as I run it, I gets access denied error.
As above confirms we can manage permissions for AD management tasks in granular level.
This marks the end of this blog post. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.