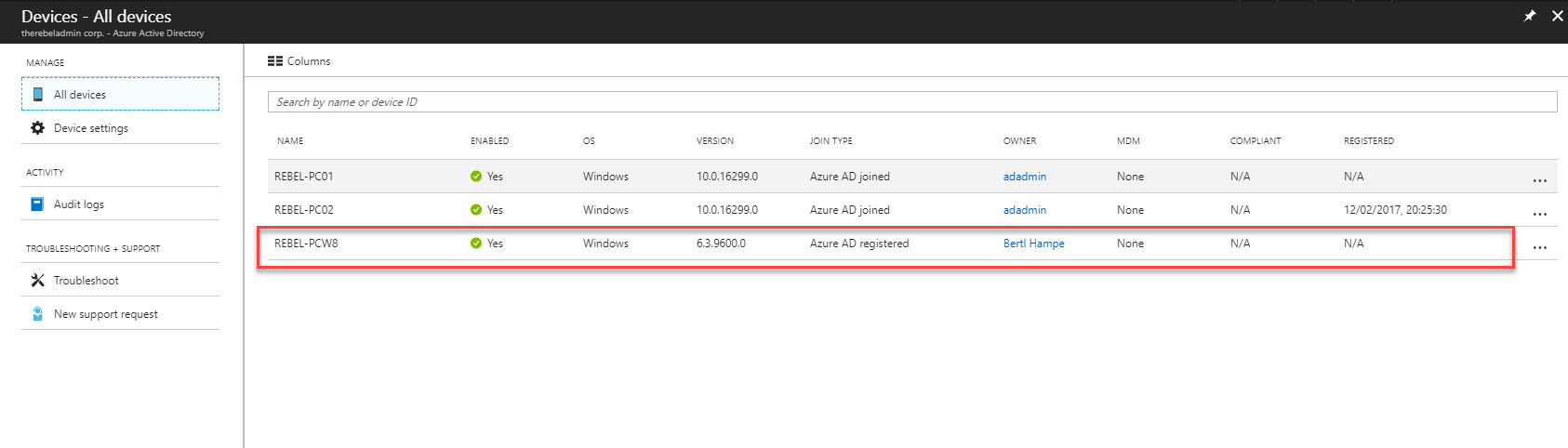
Devices runs with Windows 10 and Windows Server 2016 can directly connect to Azure AD. I have used it on my last few posts and explain different features available for Domain Joined Devices. However not every device in an infrastructure runs with Windows 10 or Windows Server 2016. If it is cloud only environment, you can simply connect your VMs in Azure to Azure AD without issue. but if it is remote devices you do not have option than upgrading to windows 10 and windows 2016. In Hybrid Environment with some configuration changes, Azure AD allow to join devices runs with,
• Windows 8.1
• Windows 7
• Windows Server 2012 R2
• Windows Server 2012
• Windows Server 2008 R2
In this demo, I am going to explain how we can connect these down-level devices to Azure AD.
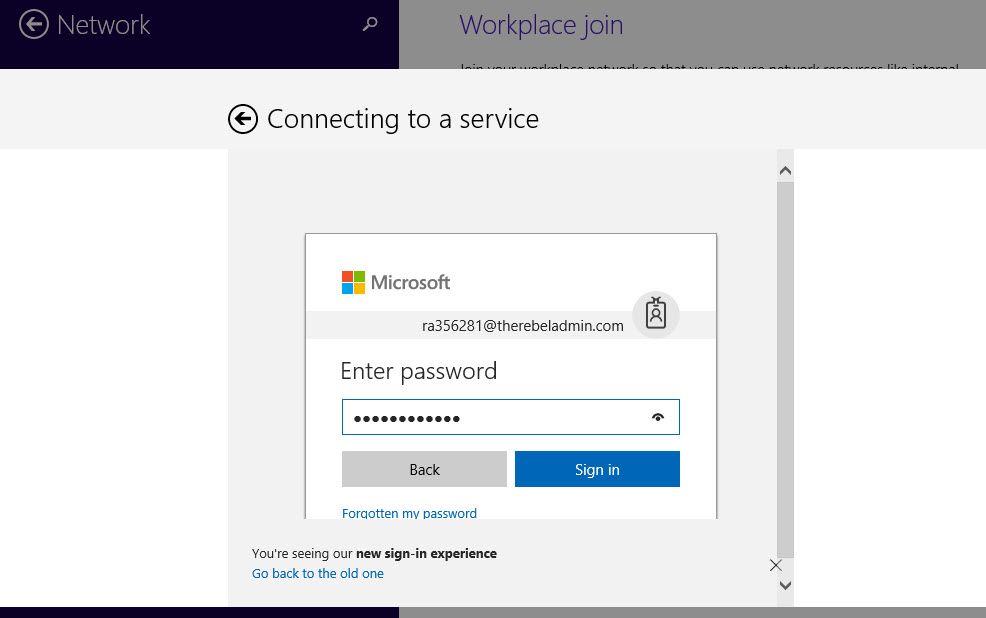
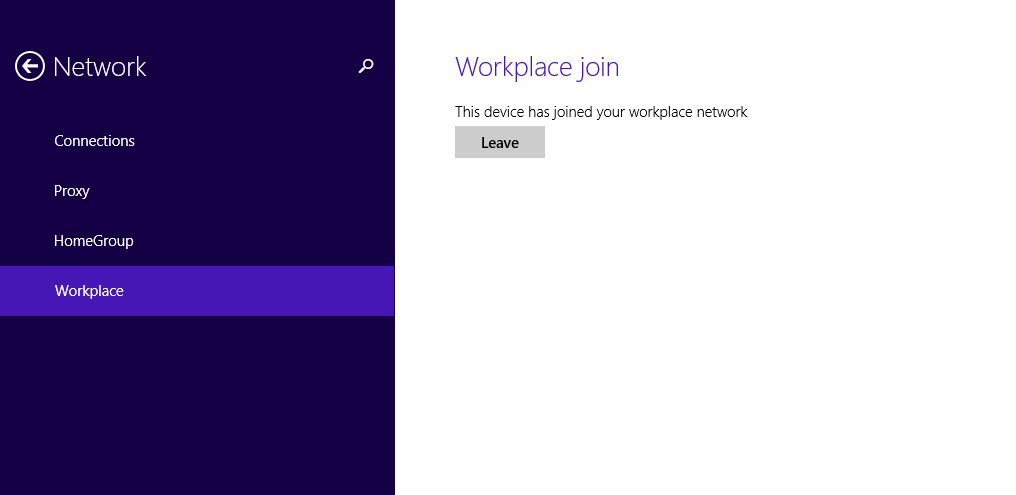
If it is hybrid environment, it will be either federated or non-federated environment. In this post, I am only going to focus on non-federated environment. The configuration and prerequisites are different from one method to another.
In non-federated environment,
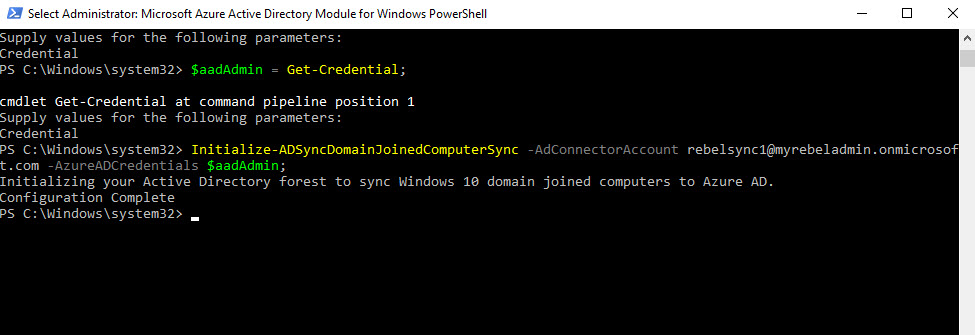
Import-Module -Name "C:\Program Files\Microsoft Azure Active Directory Connect\AdPrep\AdSyncPrep.psm1";
$aadAdmin = Get-Credential;
Initialize-ADSyncDomainJoinedComputerSync –AdConnectorAccount [AD connector account] -AzureADCredentials $aadAdmin;
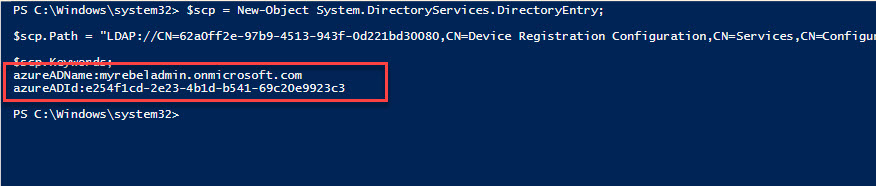
$scp = New-Object System.DirectoryServices.DirectoryEntry;
$scp.Path = "LDAP://CN=62a0ff2e-97b9-4513-943f-0d221bd30080,CN=Device Registration Configuration,CN=Services,CN=Configuration,DC=therebeladmin,DC=com";
$scp.Keywords;




thank you so much for this!