Single-sign on provides seamless sing on experience to multiple systems using one identity platform. Azure AD supports three types of single-sign configuration methods for applications.
Federated single sign-on – This is the most commonly used SSO type. when it is in use, applications redirect users to Azure AD for authentication. This method can use with any application that use SAML 2.0, WS-Federation, or OpenID Connect authentication protocols.
Password-based single sign-on – In this method, Azure AD manages credentials for the application and replay when required. In this method end user do not need to know the credentials to access the application.
Linked single sign-on – This allows to link existing single-sign on configuration for an application with Azure AD. This also allows to link applications with Azure or Office 365 portals.
In this post I am going to explain what is password-based single sign-on and how we can use it with third part SaaS application.
Azure AD Password-based single sign-on works with any third-party SaaS app which have HTML based sign in page. In this method, application credential will be saved in directory and when required Azure AD will retrieve credentials and pass it to application sign in page on behalf of user. There are two types of credential management methods.
Administrator managed – In this method administrator will create & manage credentials for the application. Credentials will be securely saved in directory and administrator can assign it to user or groups as required. When user access the application, credentials will be retrieved from directory and pass it to application sign in process automatically. So, end user does not require to know the credentials for the app.
User managed – In this method, administrator assign application to users or groups. When user logins for first time they can enter their own username and password to the application. Then these credentials will be saved securely in directory and use for future logins. In this scenario end user have full control over their own credentials.
Now it is time to configure Password-based single sign-on for SaaS app and see how it works. in my demo I am going to use twitter app for this. Before we start, we need to create demo account in twitter using https://twitter.com/signup
1. To configure Password-based single sign-on for twitter, log in to https://portal.azure.com as global administrator
2. Then go to Azure Active Directory
3. In new window, click on Enterprise applications
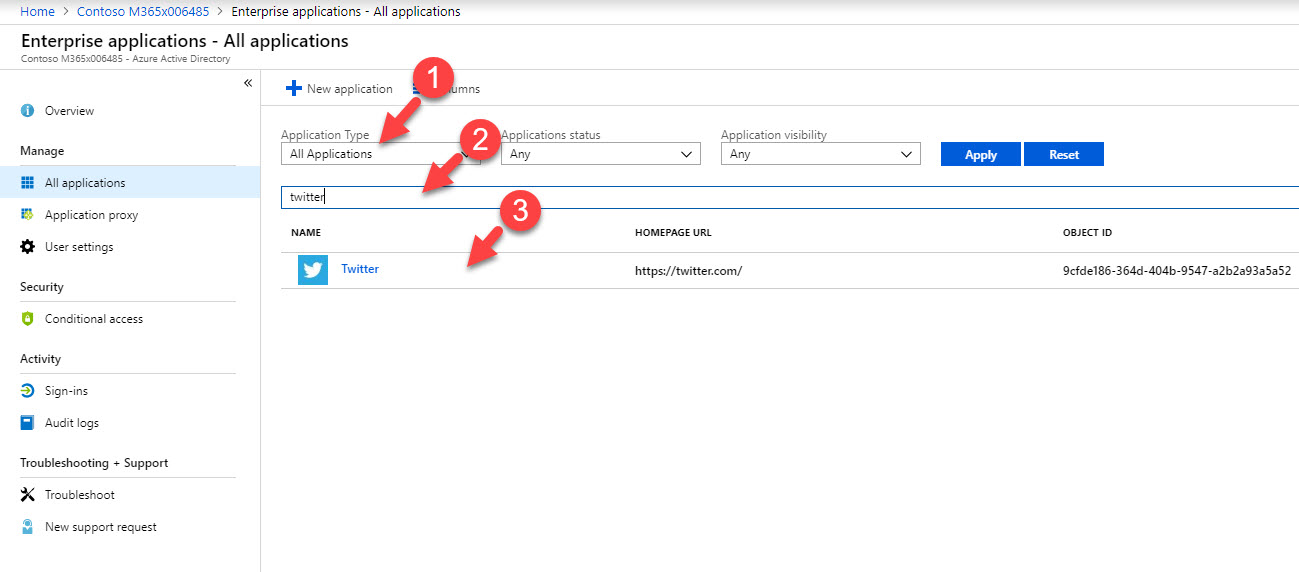
4. Then select all applications under application type and search for twitter app. Once app is return under search results, click on it. if you do not have twitter app under the results, click on New Applications to add the app from gallery.
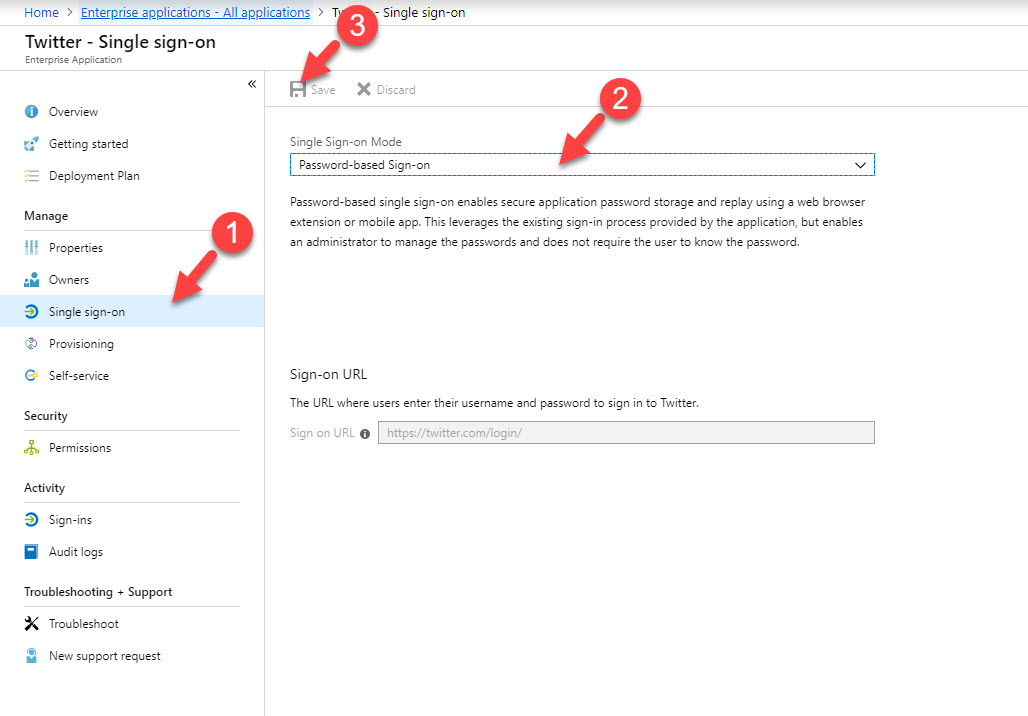
5. In new windows, click on Single sign-on under Manage. Then from the mode drop down select Password-based single sign-on and click on Save.
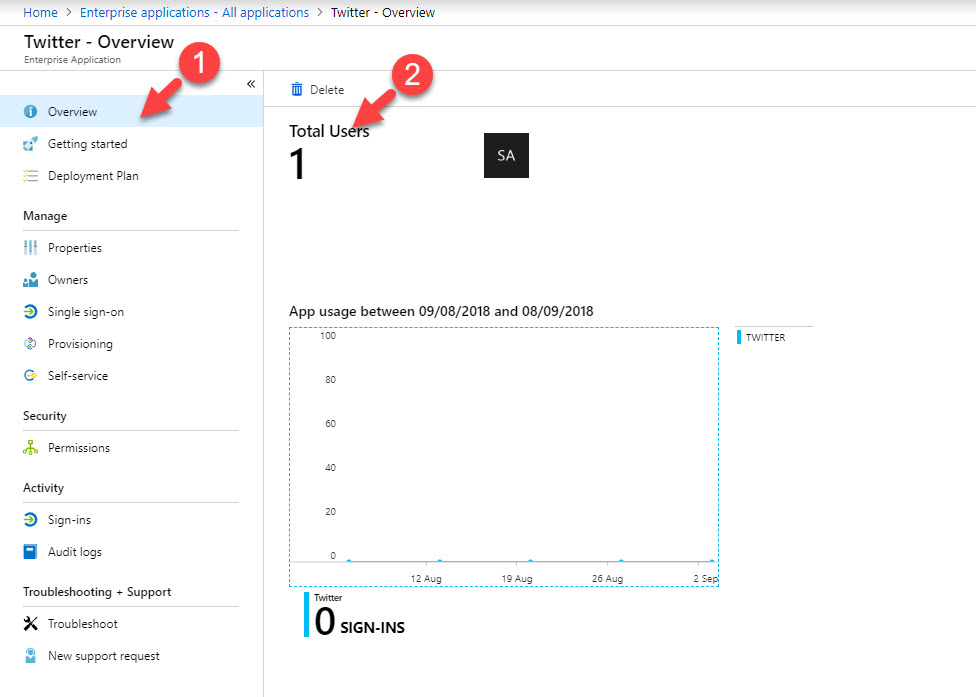
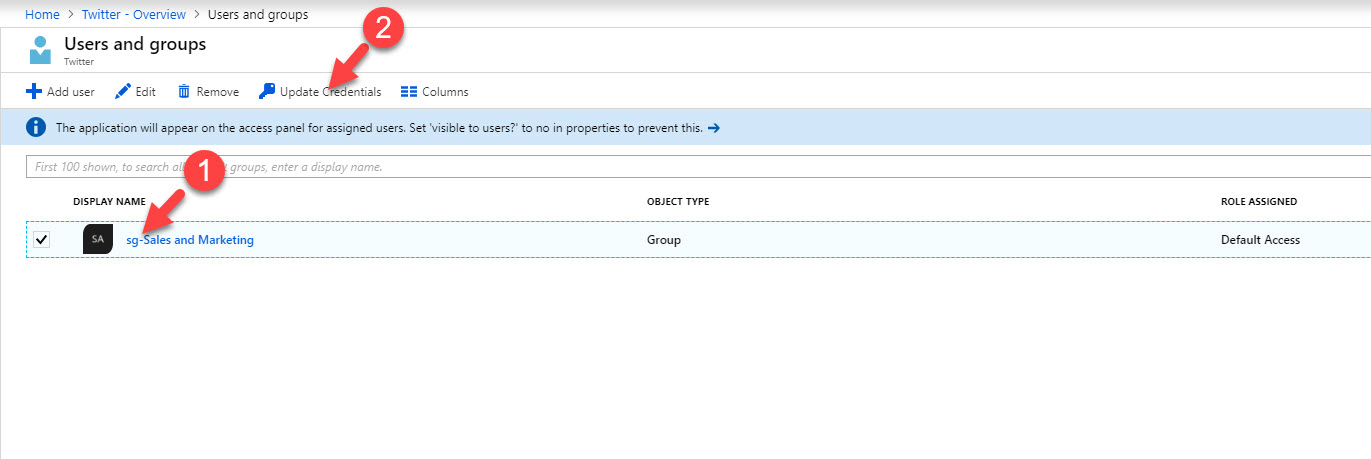
6. Click on Overview and then total users to select groups. In my demo I am going to assign it to sales & marketing group. once group is selected, click on Update Credentials.
7. Then in next window, type the credentials for the app and click on Save.
8. Once it is done, I logged in to the https://myapps.microsoft.com as member of selected group and click on to launch twitter.
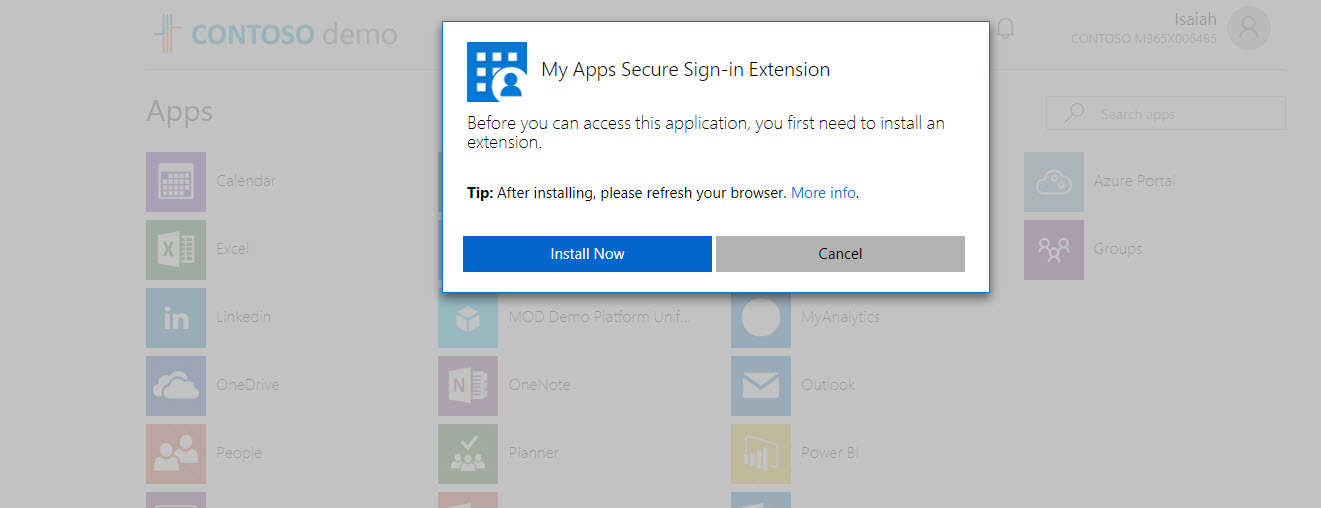
9. Then it asks me to install the extension.
10. Once it is done, I relaunch twitter app and it log me in direct.
This marks the end of this blog post. Hope now you have better understanding what is password-based single sign-on and how to use it. If you have any further questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.