In an active directory domain environment by default any authenticated user from domain, can add workstations to domain up to 10 times. But there are situations where you may need to increase this limit or completely disable this limit.
For ex- Let’s assume an employer bring his laptop in to office and plug it in to company network. Unless its control via NPS (network policy server) or network level port protection user can simply add it to the company domain using his/her user credentials. It’s defiantly a threat to the organization’s network and data.
On another example let’s assume we restructured company domain hierarchy and we need to change domain to the different domain. If the company have 500+ workstations it will take days to move them to the new domain. But if we adjust this limit we can get help from department leads, managers to help with the process without delegating permissions.
So based on the requirement, let’s see how we can edit this limit. In demo I am using a domain controller which runs windows server 2012 R2. But same steps can use for server 2008 environment as well.
Note – This limit is do not apply for any user account which is a member of domain admins or enterprise admins group.
1) Log in to the DC server as domain admin or enterprise admin.
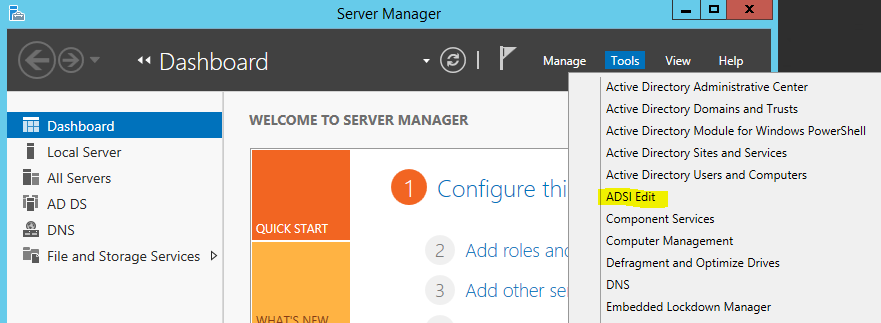
2) Go to Server Manager > Tools > ADSI Edit
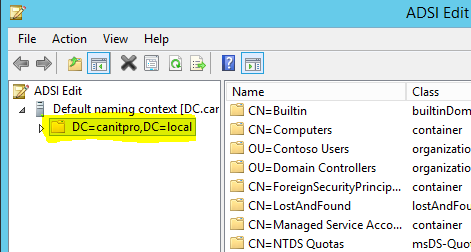
3) In console expand default naming context and select the correct domain. ( in forest there can be different domains based on the config )
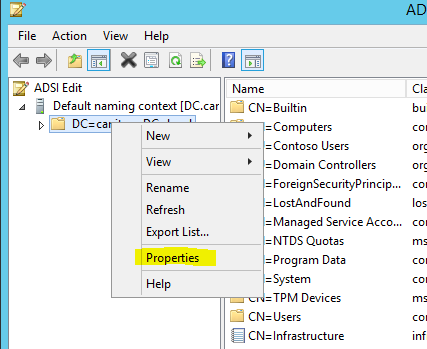
4) Then right click on it and select “properties”
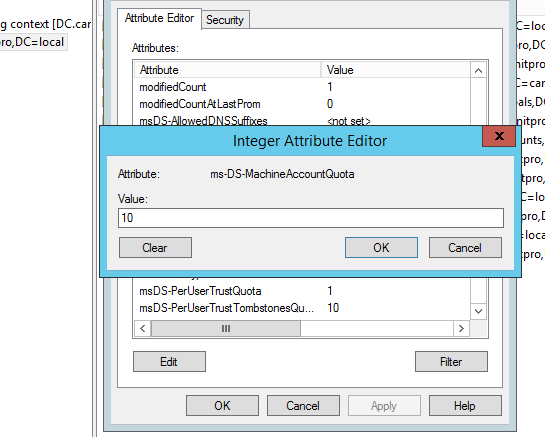
5) Once list is open find the attribute called ms-DS-MachineAccountQuota. This is the attribute responsible for above limit. By default its set to 10. If set it to 0 it will disable this limit and otherwise the value can adjust based on the requirements.
6) Once done click on ok until you exit from the popup window.
This is the end of the post and if you have any questions feel free to contact me on rebeladm@live.com




How to give access to set of peoples or groups members access