There are 3 different methods which we can use to integrate on-premises Active Directory with Azure AD.
• Pass Password hash synchronization
• Federation using Microsoft AD FS or PingFederate
• Pass-through Authentication
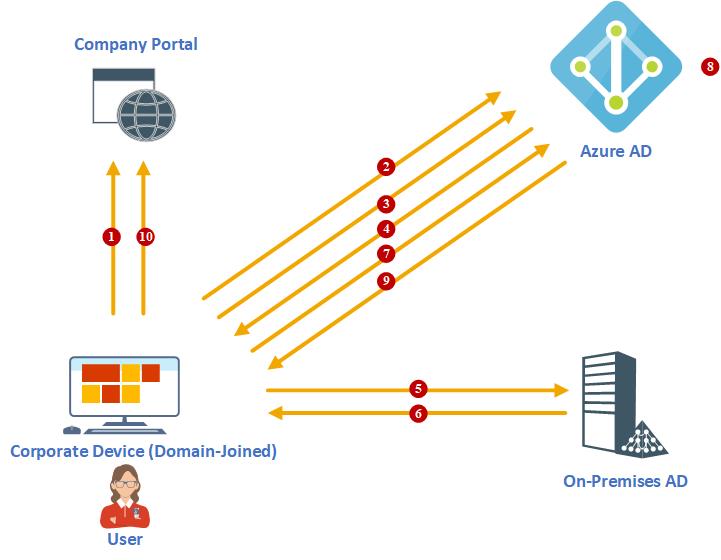
All above methods allow on-premises users to use their existing domain user names and passwords in order to authenticate in to Azure AD integrated services. However, even users can use same user name and passwords, when they access Azure AD integrated services from corporate device (Domain member), they still have to authenticate via sign in page. Azure AD Seamless SSO allow users to access Azure AD integrated services via corporate devices without re-authentication. Azure AD Seamless SSO can use with password hash synchronization and pass-through authentication method. It is not supported to use with federated authentication method (AD FS already capable of provide SSO).
• Azure AD Seamless SSO feature can enable via Azure AD connect. So, it is not required any additional component in environment.
• This is a free feature. We do not need to pay anything for it.
• Azure AD Seamless SSO works only in domain-joined devices (no need to be Azure AD join)
• If SSO process is fail for any reason, user can still authenticate using user name and password.
• It is supported to work with browser-based web applications and Office 365 clients with app versions 16.0.8730 and above.
• Azure AD Seamless SSO accepts user names as value associated with userPrincipalName attribute or Azure AD connect Alternate ID attribute.
• Azure AD Seamless SSO uses the securityIdentifier claim in the Kerberos ticket to find the relevant user object in Azure AD.
• Once Azure AD Seamless SSO is enabled, if an application can forward domain_hint (OpenID Connect) or whr (SAML) parameter to identify tenant and login_hint (OpenID Connect) parameter to identify user, we can log in to Azure AD without typing user names. It is also possible if the application uses unique URL and pass the domain info or tenant info.
• Once user is logged in via SSO, if required user can still sign out and log in as a different user at any time.
Let’s go ahead and see how Azure AD Seamless SSO works during the authentication process.
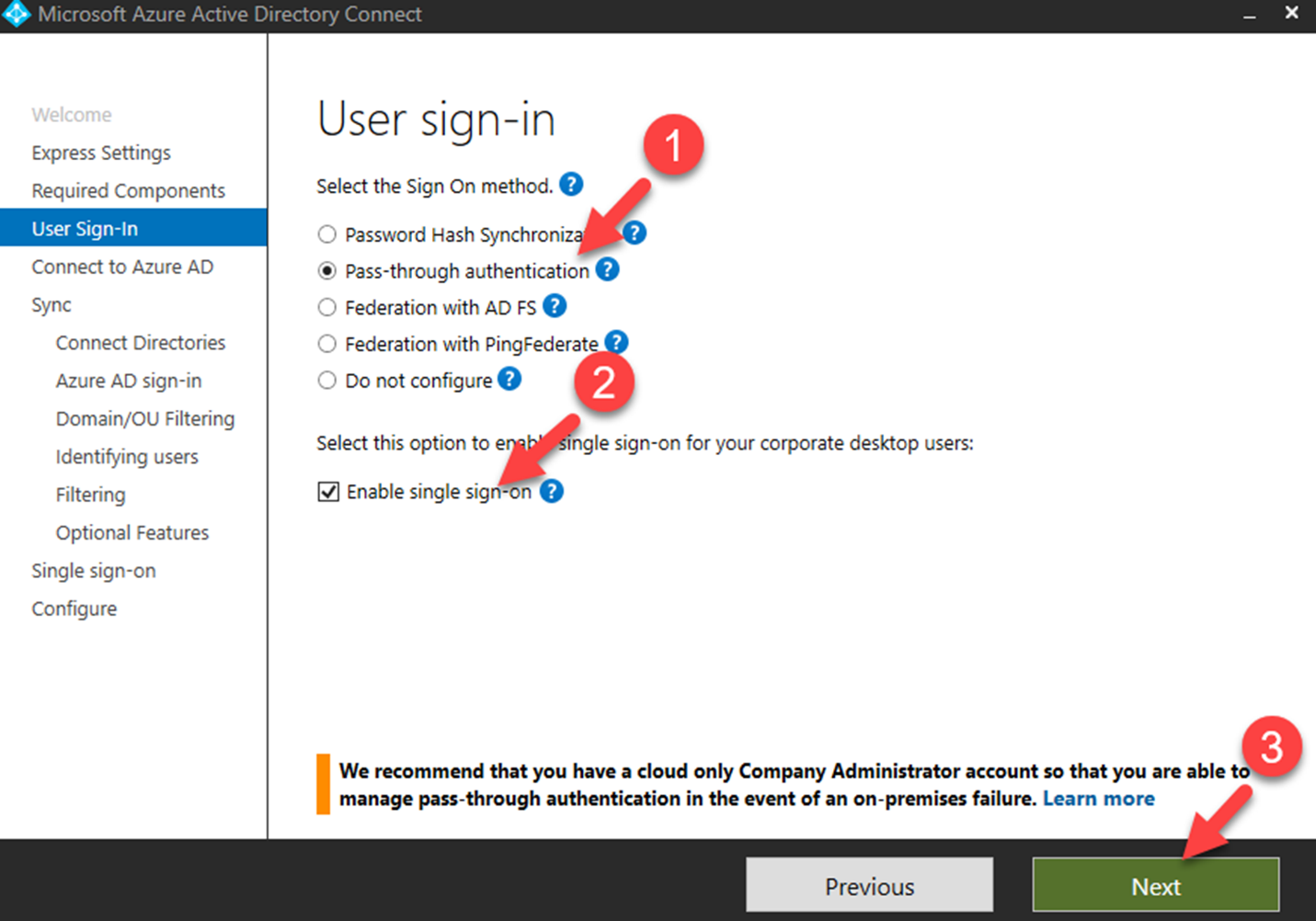
The above image shows the user sign-in configuration page of Azure AD connect. If you are using password hash sync or pass-through authentication, you can simply enable seamless SSO by selecting “Enable single sign-on” option.
This marks the end of this blog post. Hope now you have better understanding how Azure seamless SSO works behind the scene. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.




Very good post! Here is a to recreate the computer account: AZUREADSSOACC if it’s missing, without reinstalling AADConnect: https://www.sysadmit.com/2020/07/azureadssoacc-recrear-cuenta.html