It’s been quite some time from my last post. I have been involved with a large data center migration project for last month and gave me little time to involve with the blog.
In a company environment sometime you may have requirements where you need to block certain software access, software application install. In windows xp and windows vista Microsoft introduce Software Restriction Policies (SRP) where administrators can define rules and enforce application control policies. but it’s quite been a management burden for the administrators as these rules based on "Hash rules". Hash value is a digital fingerprint which remains valid even the name or location of the executable file change. But every time software is updated new values need to be created.
With windows 7 Applocker, Microsoft gave more control over the software restriction. This is part 1 of the series of posts which explain the AppLocker and the use of it.
According to Microsoft (http://msdn.microsoft.com/en-us/library/dd548340%28v=ws.10%29.aspx) Applocker can mainly use for following,
- Prevent unlicensed software from running in the desktop environment if the software is not on the allowed list
- Prevent vulnerable, unauthorized applications from running in the desktop environment, including malware
- Stop users from running applications that needlessly consume network bandwidth or otherwise affect the enterprise computing environment
- Prevent users from running applications that destabilize their desktop environment and increase help desk support costs
- Provide more options for effective desktop configuration management
- Allow users to run approved applications and software updates based upon policies while preserving the requirement that only users with administrative credentials can install or run applications and software updates
- Help to ensure that the desktop environment is in compliance with corporate policies and industry regulations
System Requirement
Applocker can use with operating systems after Windows 7. It can be used in standalone workstations as well as in AD environment. In AD environment we can use it Group Policy to define the AppLocker rules.
Concerns
Applying application restriction rules can be a overhead for the administrators. Most of time administrators block all apps and then allowing only the required app. But you should not forget that operating system itself use different executables, scripts for its functions. If you not planned this properly it can lead in to chaos.
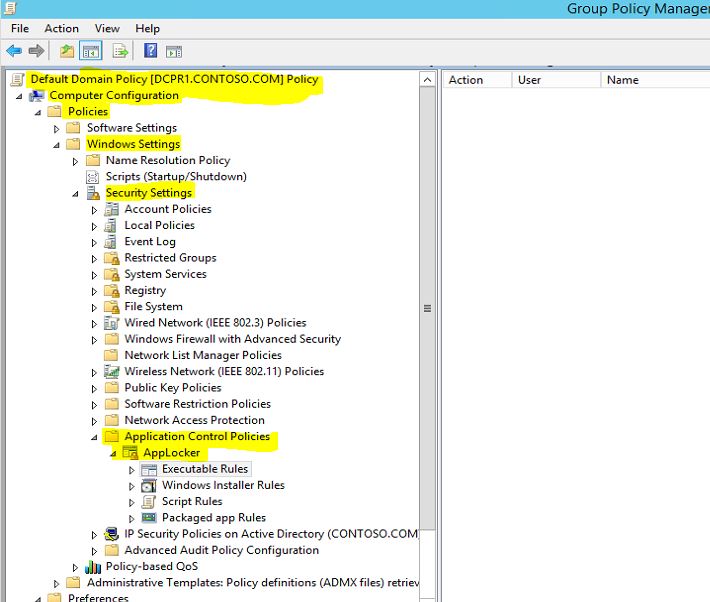
In AD if you going to define applocker rules, the rules are located in GPO > Policy Name > Computer Configuration > Policies > Windows Settings > Security Settings > Application Control Policies > AppLocker
In the container there are four nodes as you can see, those are contains the different type of rules.
Executable Rules : This will contains the rules which apply with executable files. usually those apply to application files with extension .exe and .com
Windows Installer Rules : This contains the rules which apply for the windows installer packages with .msi and .msp extensions
Script Rules : This contains rules which apply to scripts files with .ps1, .cmd, .vbs, .bat, .js extensions.
Packaged App Rules : This contains rules which apply to apps which purchased through windows store.
This is the end of part 1 of the AppLocker post series.