Azure AD conditional access policies allows to provide conditional based access to cloud workloads.
In one of my previous blog post I explain it in detail what is conditional access policy and how we can configure it. you can find it on http://www.rebeladmin.com/2017/07/conditional-access-policies-azure-active-directory/ . I highly recommend to read it before we continue on this post.
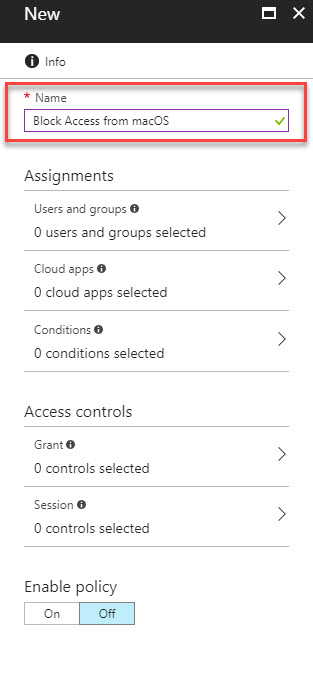
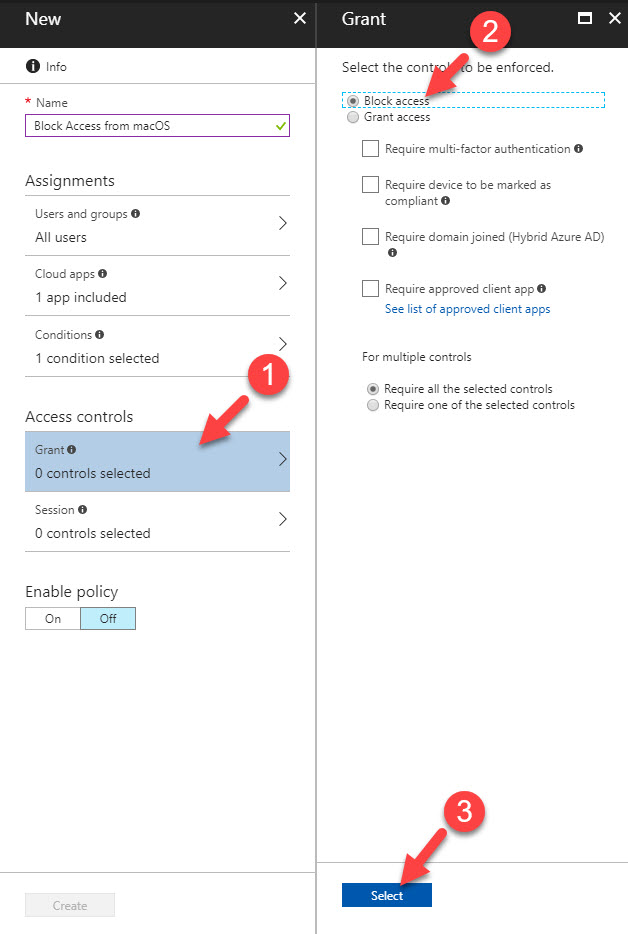
In Condition Access Policy, there are two main section.
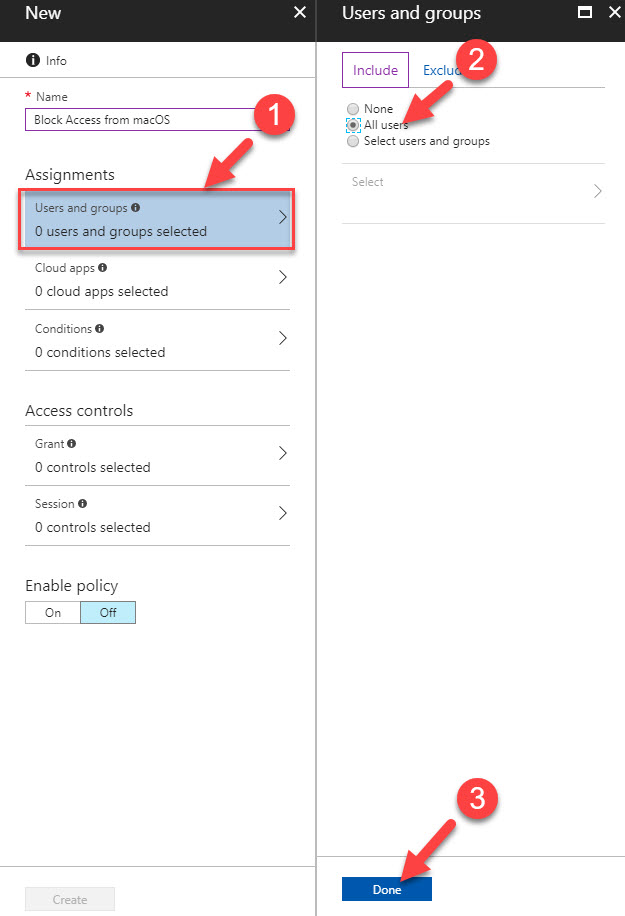
Assignments – This is where we can define conditions applying to user environment such as users and groups, applications, device platform, login locations etc.
Access Control – This is to control access for the users and groups when they comply with the conditions specified in the “assignments” section. it can be either allow access or deny access.
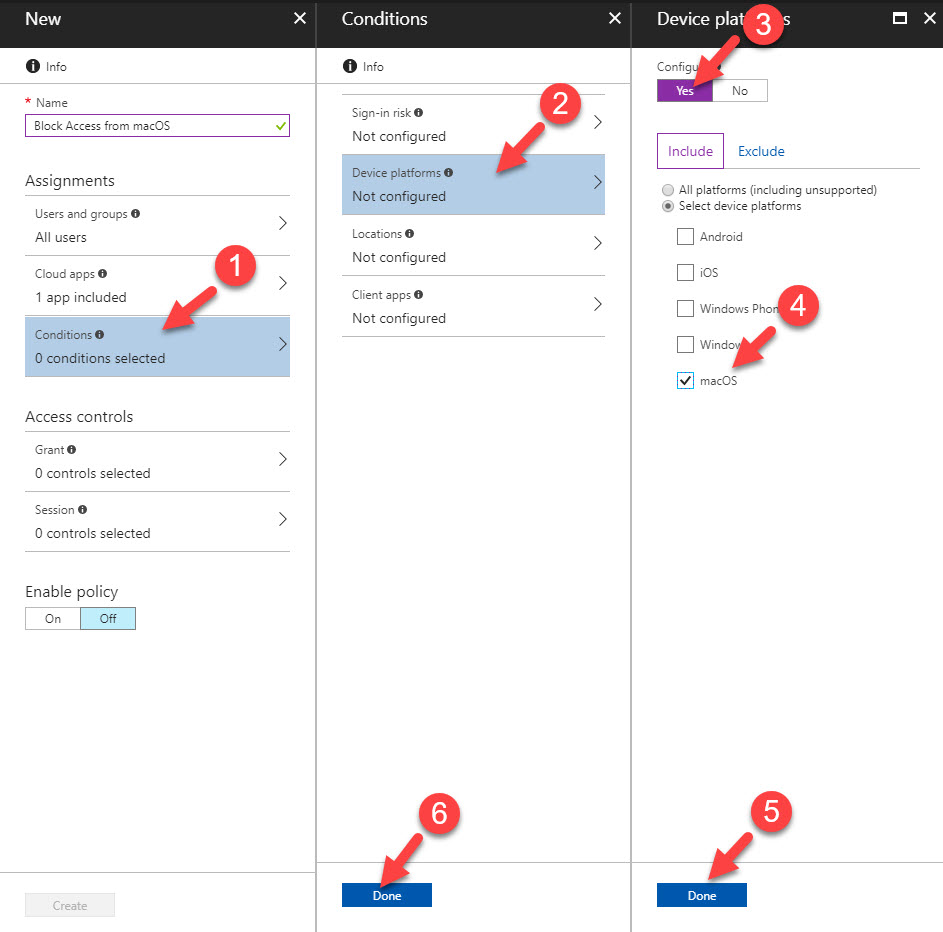
Under Assignment section we can define device platforms involves in the condition. Before when I wrote my previous post it was only supporting for following platforms.
• Android
• iOS
• Windows Phone
• Windows
From November 14th 2017, Azure AD add macOS to the list. With this update following OS versions, applications, and browsers are supported on macOS for conditional access:
Operating Systems
macOS 10.11+
Applications
Microsoft Office 2016 for macOS v15.34 and later
Microsoft Teams
Web applications (via Application Proxy)
Browsers
Safari
Chrome
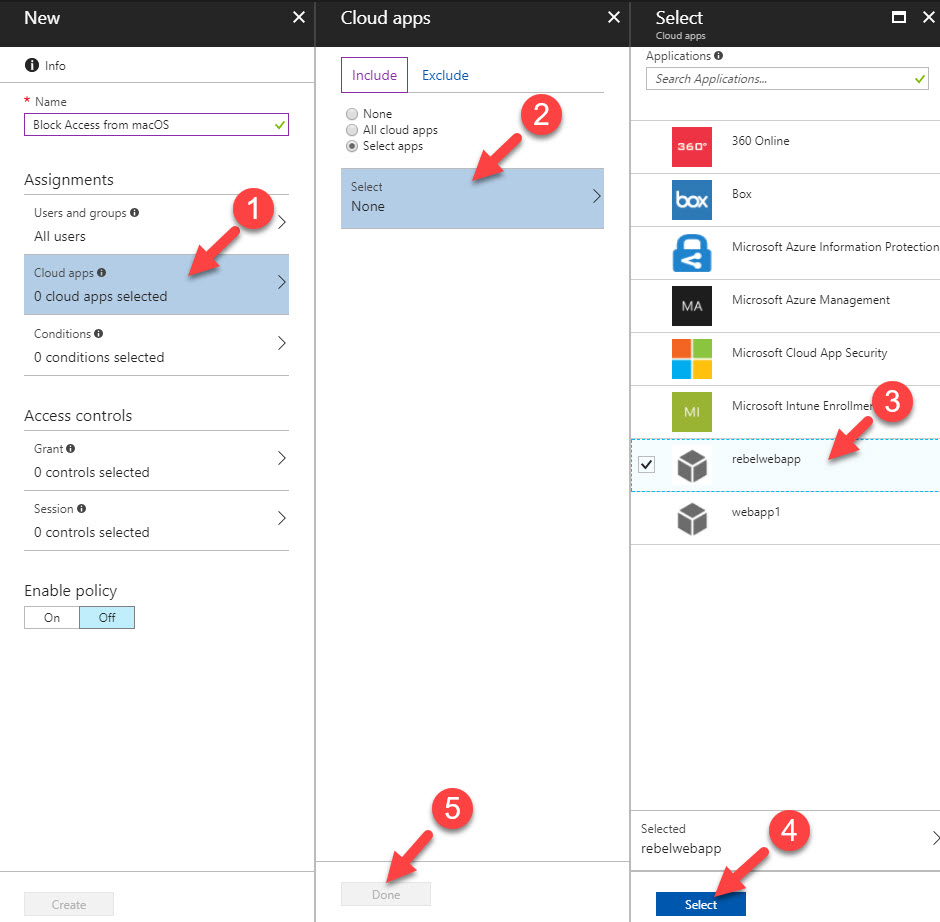
In original documentation, it didn’t say anything about web apps but in this demo, I am going to use conditional access with on-premises web app which is publish to internet using Azure Application Proxy. I wrote article about application proxy while ago and it can access via http://www.rebeladmin.com/2017/06/azure-active-directory-application-proxy-part-02/
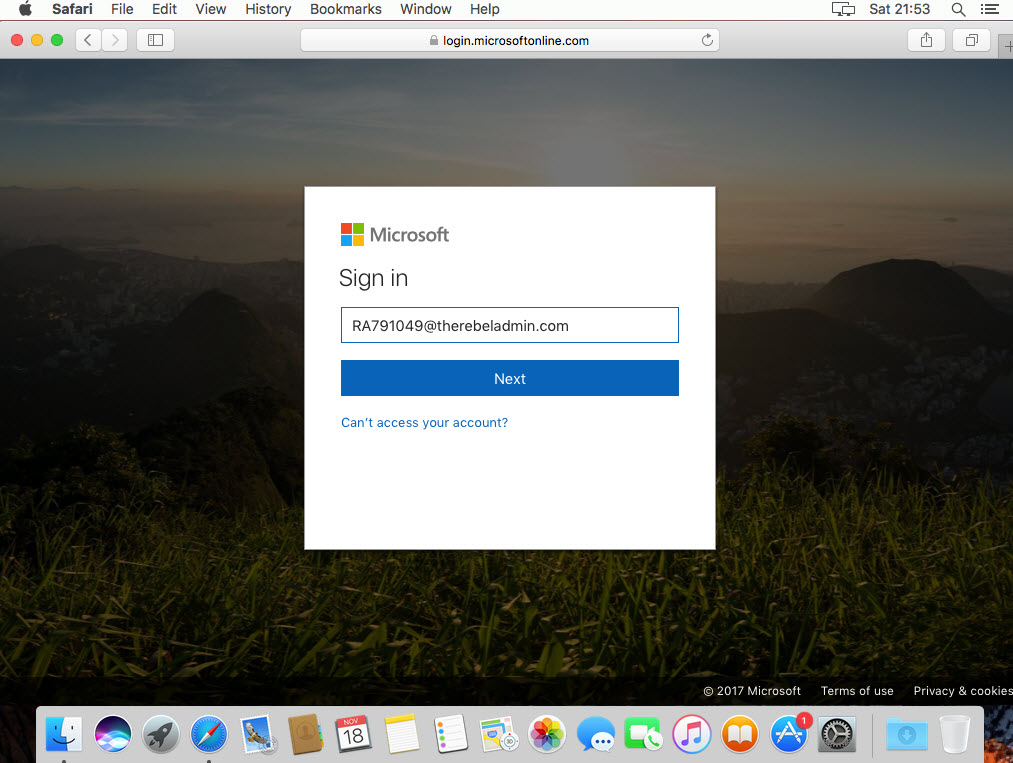
Before start configuration, let me explain little bit about my environment. I have on-premises domain environment with therebeladmin.com. I integrated it with Azure AD Premium and I have healthy sync. I have on-premises webapp and I have published it to internet using Azure Application Proxy so I can use Azure AD authentication with it. webapp can access via https://webapp-myrebeladmin.msappproxy.net/webapp/
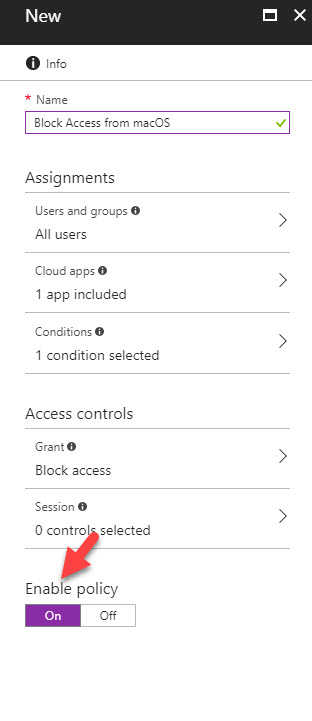
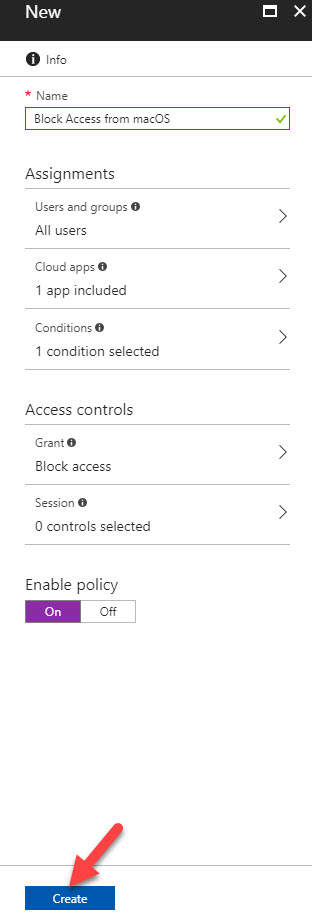
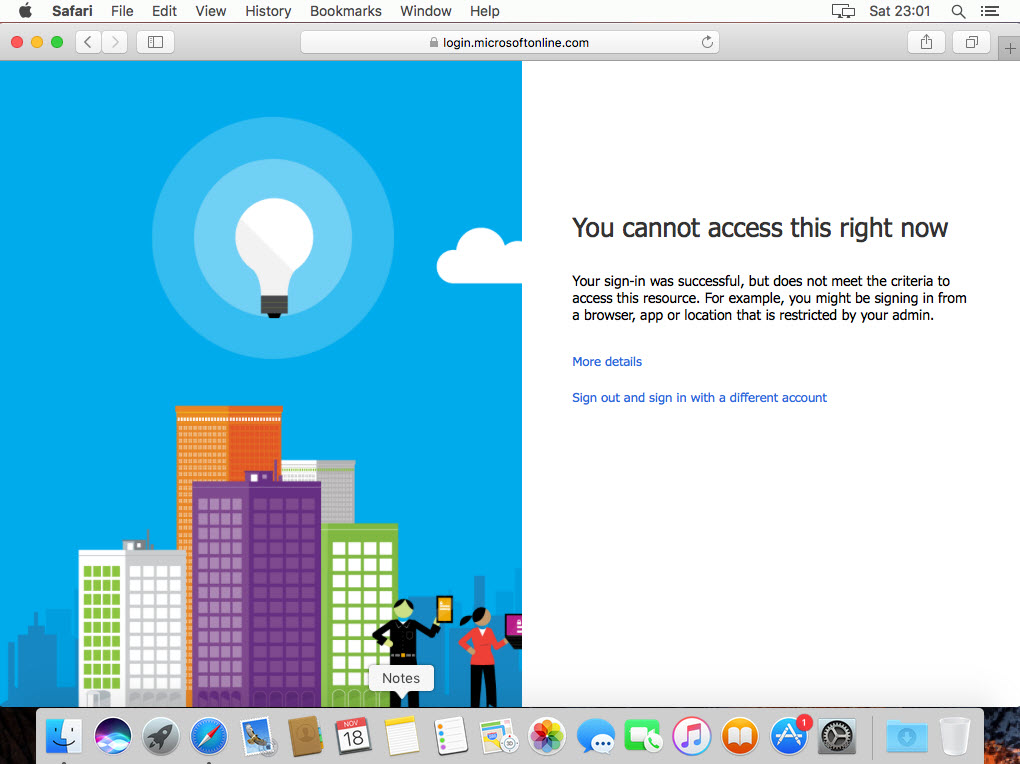
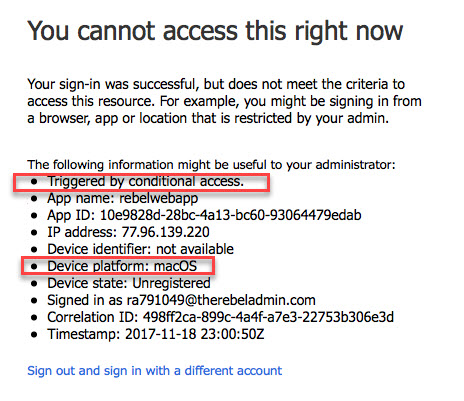
I have a mac with sierra running. In this demo, I am going to setup a conditional access policy to block access to webapp if the request coming from a mac environment.
In order to configure this,