In my previous post I have explain how to enable azure ad domain services. If you not read it yet you can find it here.
Once the domain service are enabled the next step to sync the credentials to the Azure AD domain services. Then users can use their logins to log in to the managed domain services. This post is to explain how we can do it in cloud-only environment as well as in hybrid setup.
Cloud-Only Setup
If you have cloud only setup the users who is going to use azure ad domain services need to change their passwords. Once user reset the password it generate the credential hashes which is uses by azure ad domain services for Kerberos and NTLM Authentication.
There is 2 ways to do it,
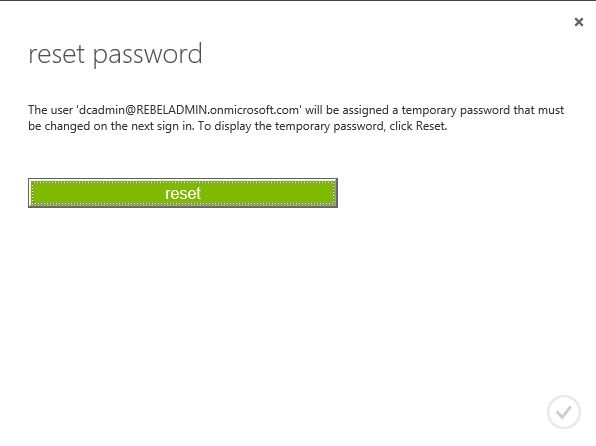
1) Force password reset – in the console we can reset the password for user. It will generate temporally password for the user. So in next login, user need to provide new password.
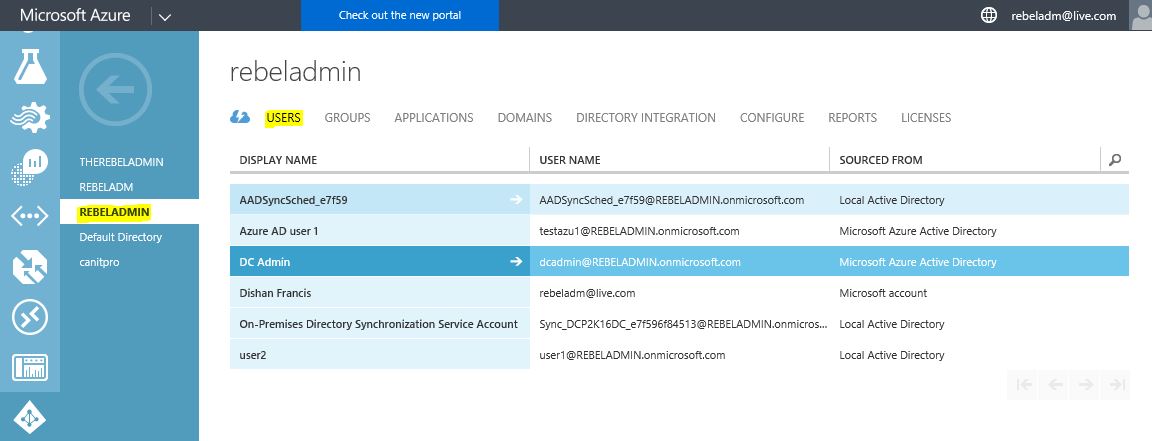
To do this, log in to Azure AD instance (which is enabled with Azure AD Domain services) and then click on users tab.
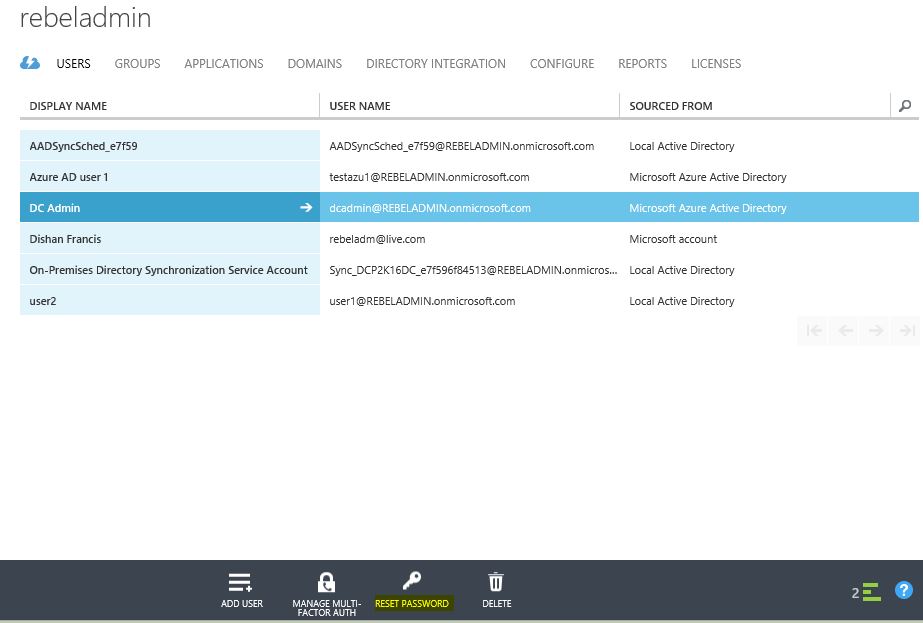
Then select the user to reset the password and in the bottom click on RESET PASSWORD button
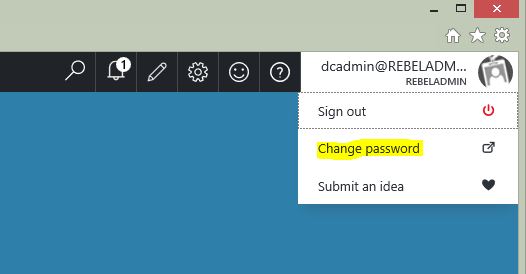
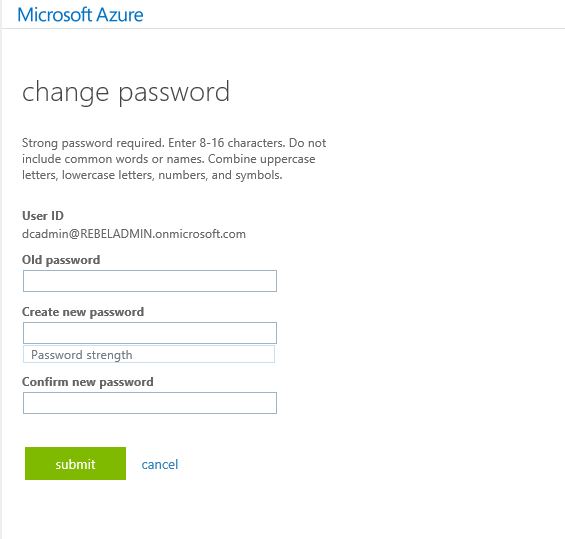
2) Change Passwords from use logins – By login in to the Azure portal, users can reset their passwords. (https://portal.azure.com)
Once user log in to the portal click on the right hand corner where user name displays and then click on “change password”
Hybrid Setup
If you have on-premises AD and sync it already with Azure AD, we need to sync credential hashes required for NTLM and Kerberos authentication via Azure AD Connect. These are not sync with azure ad by default.
First thing first, if you have Azure AD connect installed in your servers, it need to upgrade with latest version. The latest recommended version is 1.1.130.0 – published on April 12, 2016. You can download it using https://www.microsoft.com/en-us/download/details.aspx?id=47594 , this is important as older version of Azure AD Connect do not have this sync feature.
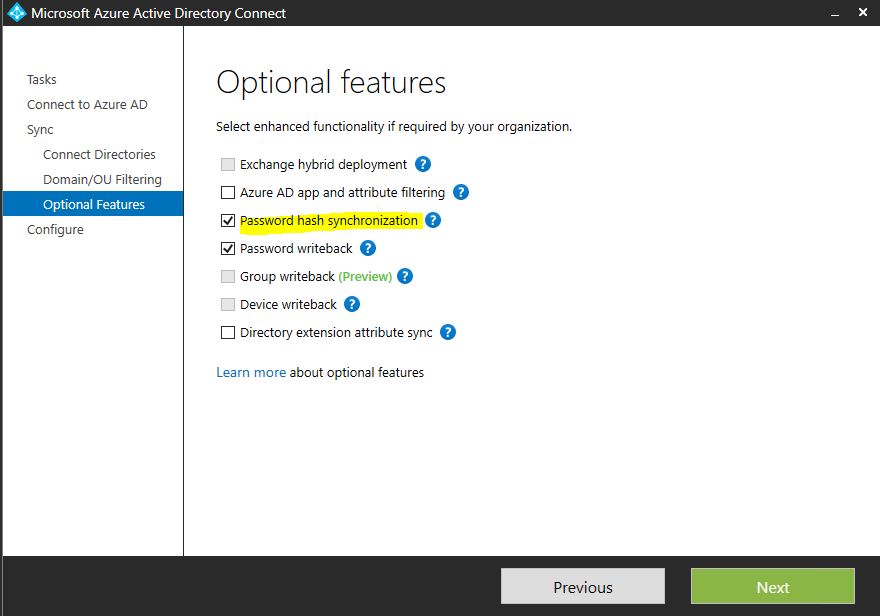
After upgrade (or new install) make sure the password synchronization is enabled. To do that,
• Log in to the server which have Azure Ad sync installed (with appropriate permissions).
• Double click on Azure AD Connect
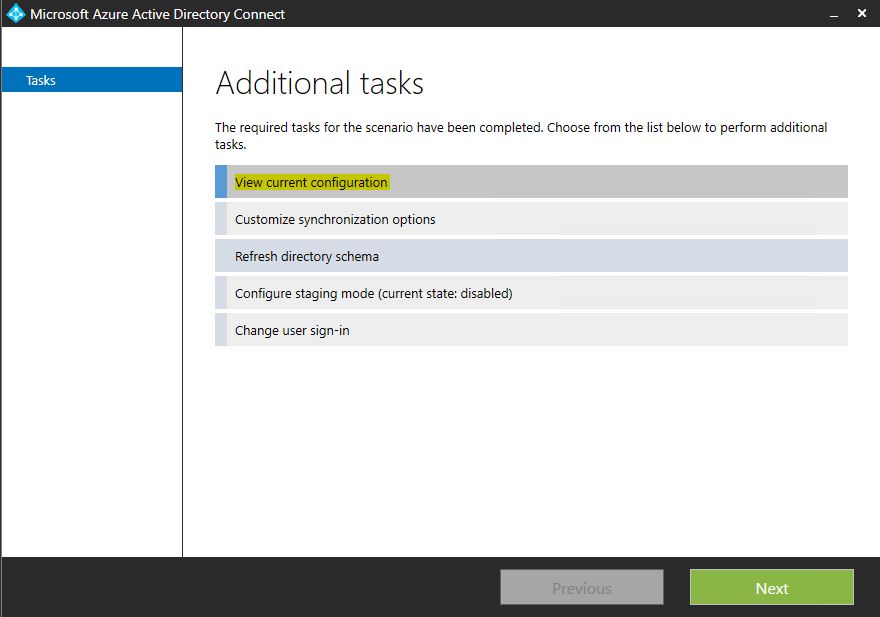
• Then in new window select the option “View current configuration” and click on “Next”
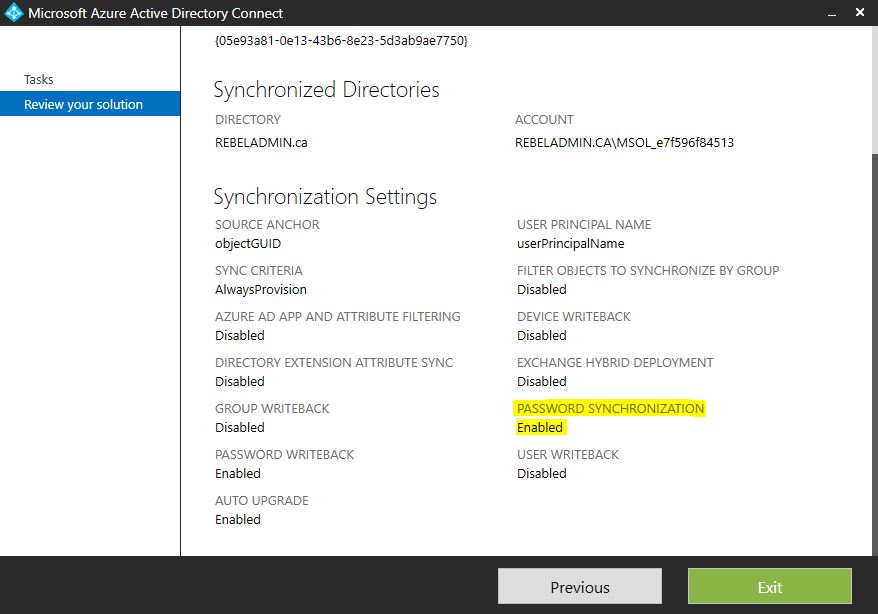
• In next window check if the password sync is enabled
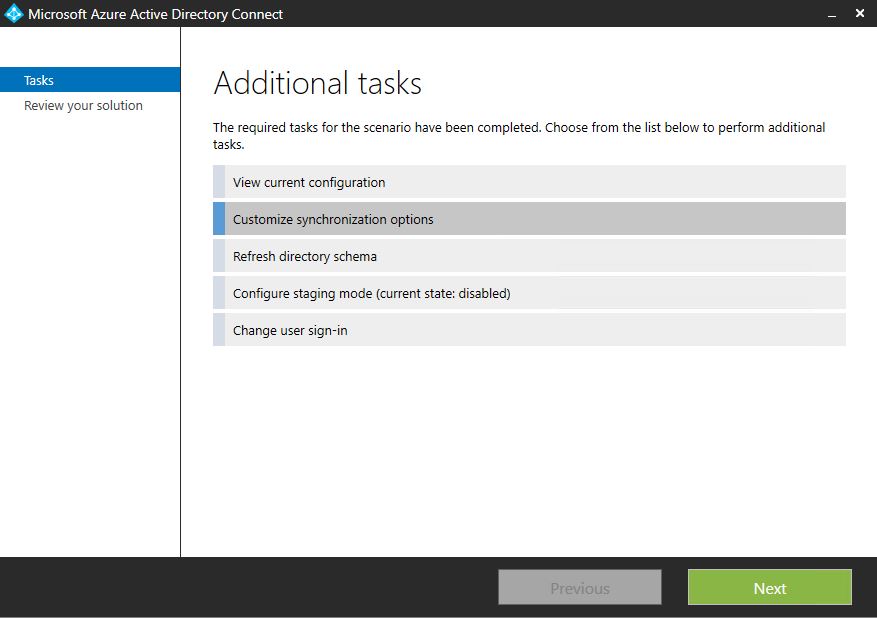
• If not go back to the previous window and select option “Customize Synchronization Options” and click next
• Then under the “Optional Features” enable password hash synchronization.
With the install if use the express settings this is enabled by default. Also check if the synchronization happening without errors.
To check that go to start > azure ad connect > synchronization services
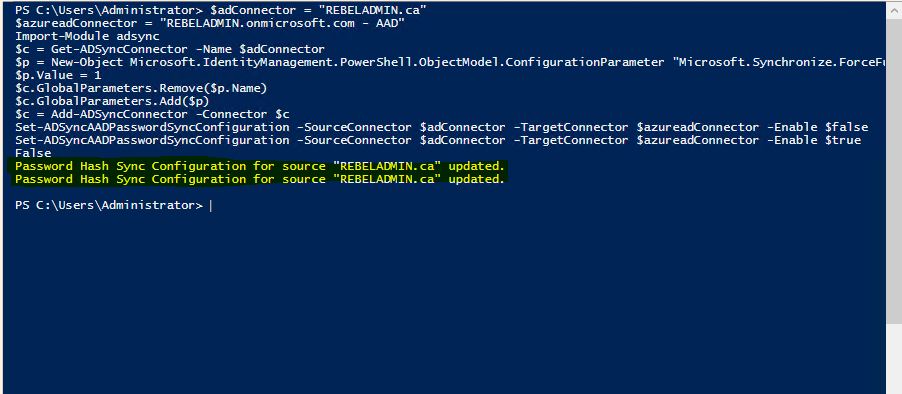
To do a full forceful password sync you can use following PowerShell script
$adConnector = "<CASE SENSITIVE AD CONNECTOR NAME>"
$aadConnector = "<CASE SENSITIVE AAD CONNECTOR NAME>"
Import-Module adsync
$c = Get-ADSyncConnector -Name $adConnector
$p = New-Object Microsoft.IdentityManagement.PowerShell.ObjectModel.ConfigurationParameter “Microsoft.Synchronize.ForceFullPasswordSync”, String, ConnectorGlobal, $null, $null, $null
$p.Value = 1
$c.GlobalParameters.Remove($p.Name)
$c.GlobalParameters.Add($p)
$c = Add-ADSyncConnector -Connector $c
Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $aadConnector -Enable $false
Set-ADSyncAADPasswordSyncConfiguration -SourceConnector $adConnector -TargetConnector $aadConnector -Enable $true
In here
$adConnector = "<CASE SENSITIVE AD CONNECTOR NAME>"
$aadConnector = "<CASE SENSITIVE AAD CONNECTOR NAME>"
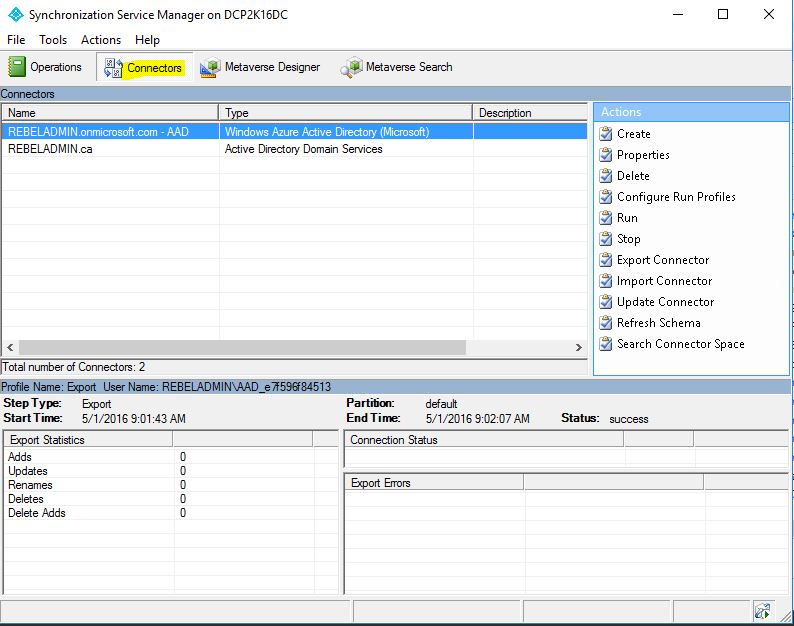
Should replace with the info related to your setup, this can find using “synchronization services” window. Click the “connectors” tab.
Once it’s edited with relevant info it can execute.
Hope this helped and if you have any questions about post feel free to contact me on rebeladm@live.com





HI,
Just wanted to confirm we already have a hybrid setup where we have on-premises AD syncing with Azure AD. If we wanted to remove the on-premise and have it all on Azure we should be OK to enable azure AD domain services on our domain (as per your previous setup guide), then sync credential hashes required for NTLM and Kerberos authentication via Azure AD Connect by forcing the password sync using powershell? I don't want to be forcing users to reset their passwords.